Similar to how the nervous system forms one of the basic functional building blocks of our human body, computer networks are at the very core of the interconnected, seamless world that we all know today. Hence, it is of paramount importance to dedicate our efforts and focus on building and maintaining the security posture of our networks. Protecting our networks from internal and external threats is one of the most important aspects of any information security program for an organization.
In this prelusive chapter, we will be looking at the core concepts that will form our building blocks for a comprehensively secure network architecture, besides a few best practices and guidelines.
The following topics will be covered in this chapter:
- An overview of network security
- Network security architecture approach
- Network security best practices and guidelines
Technical requirements
There are no requirements for this chapter.
An overview of network security
For an effective network security apparatus to be in place, it is important to understand the central concepts associated with it and the implied technologies and processes around it that make it robust and resilient to cyber attacks. Today, some of the common challenges that security professionals face is the lack of a clear distinction between the devices in their infrastructure and the data that they hold or process. This is further complicated when the visibility is blurred by not having a demarcation of the various network boundaries. Today, we have evolved networks with components such as IoT, Industrial IoT (IIoT), and cloud computing, which have further added to the network complexity.
Network security in itself touches upon various attributes of security controls that a security professional should take into account, such as security gateways, SSL inspection, threat prevention engines, policy enforcement, cloud security solutions, threat detection and insights, attack analysis w.r.t frameworks, and so on.
Therefore, it is important, as a network security professional, to not only have clear visibility of your network but also understand the effectiveness of your security products/solutions. The following subsections will help us get familiar with the key terms and components of network security.
Network security concepts
As a network security professional, you should have a good understanding of major concepts such as the different attributes of network security, different types of network attacks, the fundamentals of a firewall's intrusion-detection/intrusion-prevention systems, the fundamentals of encryption and virtual private networks, operating system hardening, and many more.
Conceptually, cybersecurity focuses on the following attributes for foundational maturity, something that we will investigate deeply later in this book:
- Authentication: The process of verifying the identity of a user or process.
- Authorization: This is the process of validating the rights/privileges that a user has for a resource.
- Confidentiality: This refers to protecting information (data and system) from being accessed by unauthorized parties.
- Availability: This refers to data and systems being available for use.
- Integrity: This refers to maintaining the accuracy, consistency, and trustworthiness of data over its entire life cycle.
- Non-repudiation: This refers to the ability to assure that the sender accepts the authenticity of their signature message.
- Resilience: This refers to the ability of an entity to deliver the intended outcome continuously, despite adverse cyber events.
Before proceeding further, please ensure that you are familiar with the following concepts:
- OSI reference model: 7 layers and their corresponding functions and TCP/IP model
- Networking protocols and concepts: Proxies, security zones, DMZ, subnetting, and NAT/PAT
- Network connectivity devices: Firewall, DLP, IDS/IPS, and load balancer
- Common threats to network security: Virus, worms, trojans, RAT, sniffing, session hijacking, and DoS/DDoS
Next, we will take a look at the various attributes of network security and how to conduct continuous improvements and post-deployment analysis.
Network security components
A foundational well-thought-out network security architecture is key to an efficient, effective, and secure network infrastructure. Often, organizations face reliability issues, performance issues, cyber disruptions, and security incidents due to loopholes in the network architecture. Organizations should focus on areas such as network segmentation, adequate access controls, Defense-in-Depth (DiD), and the implementation of least privileges from a design perspective to begin with.
The first step in defending/protecting a network is to understand what that network comprises, how its elements communicate, and the architecture. Although there are many major frameworks available for implementing best practices for network design, each organization has different operational objectives and business goals, due to which contextualization and applying the best bit for the purpose of analysis needs to be done by a security architect.
As a best practice, break down all the security controls in the organization into major blocks and test each one. This allows you to validate their effectiveness and understand the improvement areas or security gaps. The overall blocks can be Identify, Detect, Protect, Respond, Recover, and Comply:
| Identify | Detect | Protect | Respond | Recover | Comply |
| Breach Stimulation | SOC 1 and SOC 2 | Security Awareness Training | SOAR | Data Backup | ISO Requirements |
| Red and Purple Teaming Exercise | Threat Hunting | SecDevOps | Digital Forensics | Data Recovery | GDPR/PIMS/and so on |
| Cloud Breach Stimulation | Threat Intel | CASB | Incident Response | Cyber Resilience | National and Regional Policies |
| Web/Mobile Application Attacks | Attack Surface Monitoring | WAF Assessment | Cyber Incident Response Team Assessment | BCP and DR | Industry and Regulatory Requirements and Mandates |
| Infrastructure Security Attacks | Cloud Security Monitoring | Third-Party Vendor Assessment | |||
| Security Architecture and Configuration review | SIEM and SOC Detection Assessment | Data Security and Classification | |||
| IoT and IIoT Security | UEBA | Identity and Access Management |
The preceding table shows the key components of a network security program and the solutions that should be (ideally) present in those components to give it holistic coverage against threats. Some of the key topics that organizations should focus on, to begin with, will be discussed in the following subsections.
Network and system hardening
One of the most fundamental security principals that a lot of organizations miss is reducing or restricting the attack surface. This includes changing the default configurations and the lack of system hardening. Some of the ways in which system hardening can be implemented include disabling default services, restricting default permissions that start up with power on, default usernames and passwords, open ports, and so on.
Concerning passwords and credentials, a policy must be developed that enforces the usage of complex passwords with more than an eight-character limit with the mandated usage of numeric values, capital letters, and special characters. A password change policy must also be in place.
Network segmentation
Network segmentation refers to segregating a network into sub-networks with the aim of improving performance and security (a reduced attack surface and grouping systems with similar security needs). This can be achieved by implementing firewalls, a virtual local area network (LAN), and software-defined networking (SDN), to name a few.
Proper network segmentation will allow the organization to segregate low-priority and low-trust network areas from the rest of the infrastructure or critical network segments, thus preventing widespread impact in the event of a cyber attack. This also helps with utilizing security monitoring platforms and access controls for the most business-critical segments of the organization.
Network choke-points
One of the major differentiating aspects between a fragile and resilient cybersecurity program is the strategy and approach toward building a comprehensive foundation. This foundation can be built only by having a clear visualization of the logical and technological layout of the environment. For example, identifying and adequately monitoring bottlenecks and choke-points can often help us discover larger and deeper problems in the network's foundation.
In military terms, a choke-point is a location on land or sea (a valley or a strait) where the military is forced to pass through a narrow column, which makes it easier for an opposing force to take them out with ease. Technically, this is a shooting a fish in a barrel kind of situation. In networking terms, a similar situation is faced when the data flow of a network is restricted due to bandwidth or application constraints.
From a network security standpoint, common examples include implementing a firewall for an internet-facing site or a load balancer that reroutes traffic based on bandwidth consumption. In the case of a Distributed Denial of Service (DDOS) or Denial of Service (DOS) attack, this can add to cyber resiliency. Today, we can build such scalable and highly available load balancers over the cloud by using services such as Google Cloud.
Defense-in-Depth
This is an implementation approach where multiple layers of security or defensive controls throughout the environment or landscape have redundancy in case of a security incident. This is also known as the castle approach. The reason why this approach is important is that it takes the weight off a single security/defensive control and supplements/compliments the security strategy by having multiple independent controls in place at different layers.
Originally, this was a military strategy, also known as deep in defense, that sought to hinder the movement of enemy forces. The focus is not on stopping them entirely via a frontal assault but by buying time and slowing down the attack's progression.
This is an effective measure as it often results in the attacker losing momentum over a period of time due to no-or-less progress. This vital time can be used to mount an attack on the assault forces or reenforce the defenses of the defending team.
Due diligence and cyber resilience
An organization must have a cybersecurity program that aims to annually review the cyber resilience of the organization's network. This is important from various aspects. First, this ensures that the operations team is ensuring due care and due diligence across the network. Second, this gives the leadership and operations team visibility into how the network has evolved over this period and what new changes have been made, how they impact the network topology, and how this changes the threat landscape for the organization in terms of new threats and vulnerability susceptibility that may stem from these changes. This also helps in mapping the relevancy of the security controls and level of compliance.
Soft targets
There is an English phrase that states a chain is no stronger than its weakest link, which means that a group is only as strong as its weakest link. In networking terms, this holds to the core, as discussed and explored in the preceding section. You, as a network security expert, need to identify and account for a single point of failure and implement a highly dependable process that will be put in place to mitigate such instances. We should also ensure that the appropriate controls are implemented around such susceptible resources of the network, as per their risk profile.
Continuous monitoring and improvement
Proactive network scanning should be implemented to hunt for unauthorized devices in the network and to monitor for suspicious activity in the network. This would ultimately lead to the requirement of a well-defined incident response mechanism.
Being a critical operational function, NOC also needs to aim for continuous improvement concerning processes, approaches, and turnaround time to showcase business outcomes and value creation.
Post-deployment review
The major focus here is to verify whether all the deployments are accurate and operate as expected. The idea is to evaluate the actual versus expected levels of service delivery and performance.
Now that we are familiar with the various network security concepts and their key components, next, we will take a look at the systematic approach that organizations should follow for a comprehensive network security architecture.
Network security architecture approach
A successful network security implementation will consider the following key pillars. Each organization and standard that talks about network security architecture may have a different block, but the foundational principles are always the same:
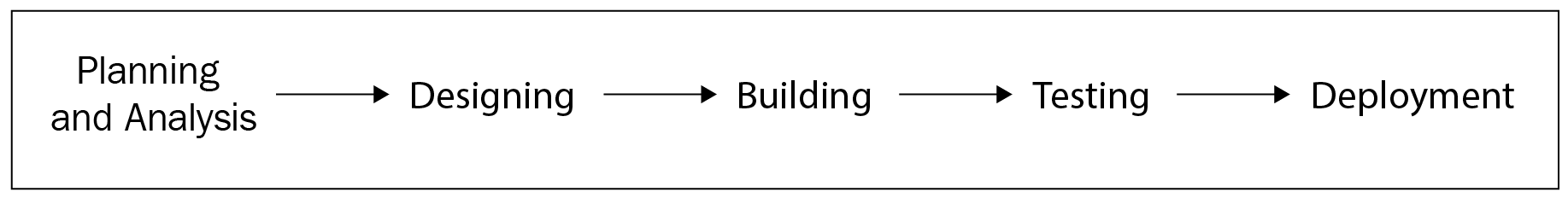
Let's quickly run through what these stages are about before analyzing them in detail in the upcoming subsections:
- Planning and analysis: The planning and analysis stage is responsible for developing a conceptual network security architecture design.
- Designing: This stage is responsible for developing a detailed network security architecture design.
- Building: In the building phase, we focus on developing the network components that were identified in the first phase of planning and analysis, as well as the second phase, where we created the outline design of how we envision the network to be formed.
- Testing: The testing phase focuses on validating the implementations that were done in the previous phase. This also accounts for how effective and efficient they are regarding their intended operational capability.
- Deployment: The major focus of the deployment phase is to ensure that the deployment and go-live plans are in place and that the operation teams are equipped to take over the operations for the network.
In the upcoming subsections, we'll understand what activities are carried out in these stages and how they achieve their goal.
- Simplex, half-duplex, and full-duplex communication
- Baseband and broadband
- Circuit-switched and packet-switched networks
- Basic concepts such as ARP and RARP and unicast, multicast, and broadcast traffic
- Distributed Network Protocol (DNP3 – used in SCADA and smart grid applications), storage protocols (FCoE, iSCSI), and Virtual SAN (vSAN)
- Software-defined networks
- Authentication protocols such as Password Authentication Protocol (PAP), Challenge-Handshake Authentication Protocol (CHAP), and Extensible Authentication Protocol (EAP)
Planning and analysis
The Planning and analysis stage is responsible for developing the conceptual network security architecture design, which covers the following:
- Network zoning and edge security
- Network access control
- Communication protocol security
- Network configuration management
- Network security monitoring and response
The objectives of this phase focus on the following activities:
- Defining the security domains and the security zones, their security boundaries, and inter-zone data flows
- Defining the communication security requirements for intra-zone and inter-zone data flows
- Defining network integration with AAA, management and monitoring systems, and operators
- Defining network access controls (physical and logical) for each security domain
- Evaluating and selecting a network security service and component vendors
There can also be additional activities, such as the following:
- Performing network discovery scans and comparing them to the existing network architecture documentation
- Identifying regulatory and policy security requirements
- Identifying the classifications, ownerships, and trust levels of different types of endpoints (users, systems, data), environments, and transit networks and performing threat modeling/threat assessment
- Identifying the classification of data flows
The following are the inputs and outputs of this phase:
|
Inputs |
Outputs |
|
|
The planning and analysis phase sets the stage for having a foundational understanding of the network requirements and constructs the basis for the next phase, which is designing the network architecture and its associated components.
Designing
The designing stage is responsible for developing a detailed network security architecture that covers the following aspects:
- A logical network security architecture
- A physical network security architecture
- An integration architecture for network management, monitoring, and Authentication, Authorization, and Accounting) (AAA)
- Network access control
- Communications security
The objectives of this phase focus on the following activities:
- Designing logical and physical security domains/zones separation (Air-gap, VLAN, VRF, MPLS, VPN)
- Designing logical and physical perimeters (Firewalls, NAT, Proxies, VPN Concentrators, IDS/IPS, App FW)
- Designing management and control (in-band, out-of-band, NCM, Backup and Restore, Fail-open/Fail-close)
- Designing AAA (Ops Model, Roles, Groups, Multi-Factor Authentication, Access Control, IAM Integration)
- Designing monitoring and response (Logging, IDS/IPS, SIEM Integration, Audit, Ops Model)
- Designing comms security (SSL Offload, VPN Concentrators, IPsec, MACsec, WPA2, Key Management)
- Designing Network access control (802.1x, TNC, Quarantine, Guests/Contractors, Remote VPN, Wi-Fi)
There can also be additional activities, such as the following:
- Building a Proof-of-Concept (POC)/model/lab environment
- Refining activity estimates (cost/time), getting management/stakeholder sign-off and obtaining funding
- Procurement
The following are the inputs and outputs of this phase:
|
Inputs |
Outputs |
|
|
Once the designing phase has been completed and an outline of the network architecture is formed, we can move on to the next phase, which is the building phase.
Building
In the building phase, we focus on developing the network components that were identified in the first phase of planning and analysis, as well as the second phase, where we created an outline design of how we envision the network to be formed. This covers the following broad aspects:
- Building a core network and integration architecture
- Developing an asset inventory with equipment configuration (CMDB)
- Developing firewall rules
- Documenting a test plan
- Executing the component test
- Developing a deployment execution plan
- Developing standard operating procedures
The objectives of this phase focus on the following activities:
- Deploying, configuring, hardening, and testing equipment
- Developing and optimizing firewall rules and network security policies (IPv4, IPv6, 6in4 tunnels, and so on)
- Developing installation/configuration guides and operational procedures
- Performing a network security component test
- Developing a deployment execution plan (including a go-live support plan)
There can also be additional activities, such as the following:
- Completing asset and cable labeling and tracking registers
- Creating, installing, securing, and tracking cryptographic keys/certificates
- Changing/replacing default usernames, passwords, and cryptographic keys/certificates
The following are the inputs and outputs of this phase:
|
Inputs |
Outputs |
|
|
Once the building phase has been completed and the major components of the network architecture have been put in place, we can move on to the next phase, which is the testing phase.
Testing
The testing phase focuses on validating the implementations that have been done in the previous phase. It also accounts for how effective and efficient they are in their intended operational capability. This includes the following:
- Auditing equipment labels and their location against the asset register
- Auditing cable labels against the cable register
- Auditing network configuration and labels
- Auditing cryptographic keys against the key register
- Performing a network scan for discovery and mapping
- Performing vulnerability analysis and penetration testing scans
- Auditing logging functionality
- Performing integration and acceptance tests
The objectives of this phase focus on the following activities:
- Auditing all networked equipment and cabling labels against asset and cable registers
- Auditing equipment configuration against a documented baseline
- Auditing default/system account passwords and cryptographic keys/certificates
- Performing discovery network scans and firewall scans
- Performing vulnerability scans for management purposes, as well as the control planes and systems (in-band and out-of-band)
- Verifying that password audits and network scans have been captured by the appropriate audit logs
- Testing integration with the management, AAA, and monitoring systems
- Performing performance and scalability testing
- Performing user acceptance testing against requirements
There can also be additional activities, such as the following:
- Validating scan results against the documented design, configuration, and registers
- Validating the naming conventions for network devices that don't reveal the device's type, version, or model
The following are the inputs and outputs of this phase:
|
Inputs |
Outputs |
|
|
After completing the testing phase, where we document our findings from the various tests and audits we've performed, we can move on to the next phase, which is the deployment phase.
Deployment
The major focus of the deployment phase is to ensure that the deployment and go-live plans are in place and that the operation teams are equipped to take over the operations for the network. This includes the following:
- Conducting training with operations staff
- Confirming and communicating deployment readiness
- Rolling out new capabilities
- Monitoring deployment and operations
- Operational handover and acceptance
- Closure and signoff
The objectives of this phase focus on the following activities:
- Conducting training sessions with operations staff
- Confirming a participant's and environment's readiness and communicating rollout dates and details
- Coordinating a rollout for a new capability to the deployment groups
- Monitoring deployment delivery and operations
- Handing over and signing off operational responsibility to the network/security operations teams
- Creating a summary report and acceptance checklist
There can also be additional activities, such as the following:
- Performing a pilot deployment on a less-critical subset of participants/environments
- Supporting security operations and network operations teams
- Updating network security/compliance and gap analysis
The following are the inputs and outputs of this phase:
|
Inputs |
Outputs |
|
|
Once the deployment phase has been completed, along with the required signoffs from the operation teams and the executive leadership, we can move on to the last phase, which is the post-deployment phase.
Post-deployment
The post-deployment phase focuses on the activities that will be used to monitor the performance of the network, as anticipated, and inculcate strategies and methods to uplift the network's performance. This includes the following:
- Reporting: Establish regular KPI and KRI reporting (for example, for compliance)
- Continuous improvement: Perform regular vulnerability assessments
- Regular audits: Perform regular audits against known configuration and registers
This concludes our discussion on the network security architecture approach. This gave you a detailed deep dive into the mindset and procedures that you should take into account when planning for a network security exercise for an organization. However, most organizations might already have a network in place.
The approach we use might take a slight diversion in this case, such as starting with a security audit, which investigates their network security policies and verifies the network assets for potential deficiencies. This will give you a clear picture of what needs to be addressed and the prioritization. Findings may result in restrict user access privileges and implementing the least privileges across the environment in an iterative process. You may also need to review your security controls and platforms in use for detection, prevention, response, and so on based on their effectiveness and how they are used (the way they are used and the team's ability to use them appropriately).
Now that we've completed the basic groundwork, we will look at the various best practices of network security and how they help us build a more resilient environment.
Network security best practices and guidelines
Network security does not just end when we implement security products or processes. A network is like a living and breathing organism that evolves with time, but sometimes breaks down and needs maintenance. Apart from security issues, there are many common issues that can occur, including network connectivity issues, power outages, network crashes, and black holes in routing.
Typically, a Security Operations Center (SOC) is something that is at the center of security monitoring and operations, but at the same time, a Network Operations Center (NOC) can play a very important role in network resilience and optimal performance. In this section, we'll take a look at some of the key attributes of the NOC.
Network Operations Center overview
An NOC is a central entity for an organization's network monitoring endeavor. This encompasses technology and processes essential to actively managing and responding to networking-related issues. A typical NOC consists of engineers and analysts monitoring the network, ensuring smooth operations, and ensuring network/infrastructure uptime. This includes, but is not limited to, the following:
- Network device, server, application, and endpoint monitoring
- Hardware and software installation concerning network devices
- Network analysis (discovery and assessments) and troubleshooting
- Monitoring common threats, viruses, and DOS attacks
- Alarm handling and performance improvement (including QoS)
- Monitoring power failures and system backups
- Application, email, policy, backup and storage, and patch management
- Service optimization and performance reporting
- Threat analysis
NOCs often encounter complex networking issues that might need troubleshooting and collaboration between different IT teams to investigate and resolve the issue. To increase the overall effectiveness of an NOC, organizations focus on a few areas, as discussed in the following subsections.
Proper incident management
This will include identifying an incident, investigating the root cause, resolving the incident, and preventing its recurrence to avoid business disruption. For a more evolved look at the best practices for incident management, the organization should review and analyze their adherence to the ITIL incident management framework. This includes the following:
- Prioritizing incidents based on their impact.
- Accurately reflecting on the current status and documentation of all artifacts.
- Implementing a streamlined process to ensure the effective handling of incidents that's in line with the organization policy.
- Automating elementary manual iterative tasks and escalations.
- Implementing an effective communication mechanism for sharing real-time updates with the required stakeholders.
- Integrating third-party applications such as ticketing systems, monitoring dashboards, a knowledge base, threat intelligence, and so on to make the analyst more empowered.
- Establishing key performance indicators and driving continuous improvement by reporting on them. This helps the organization continuously improve and innovate on its performance metrics and key deliverables, such as higher performance quality, lower costs to serve them, and their mean time to resolve.
An incident response team should consist of a hierarchical team structure, where each level is accountable and responsible for certain activities, as shown here:

Let's take a quick look at each layer:
- Tier 1 Analyst: Acts as the first point of contact in the incident response process. They areresponsible for recording, classification, and first-line investigation.
- Tier 2 Analyst: Acts as an escalation point for Tier 1. Also acts as an SME for deeper investigation and the creation of knowledge articles. They are also required to escalate major incidents to Tier 3.
- Tier 3 Analyst: Acts as an escalation point for Tier 2 and is responsible for restoring an impacted service. They escalate unresolved incidents to the relevant vendor or team for resolution. They also act as a liaison between internal and vendor teams.
- Incident Coordinator: Acts as the administrative authority ensuring that the process is being followed and that quality is maintained. They are responsible for assigning an incident within a group, maintaining communication with the incident manager, and providing trend analysis for iterative incidents.
- Incident Manager: Manages the entire process until normal service is restored. They are primarily responsible for planning and coordinating activities such as monitoring, resolution, and reporting. They act as a point for major escalations, monitor the workload and SLA adherence, conduct incident reviews, provide guidance to the team, and ensure continuous improvement and process excellence.
In some organizations, there are other roles such as incident assignment group manager and incident process owner (who is accountable for designing, maintaining, and improving the process) who ensure the efficiency and effectiveness of the service's delivery.
Functional ticketing system and knowledge base
A ticketing system encompasses all technical and related details of an incident. This includes the incident number, status, priority, affected user base, assigned group and resource name, time of incident response, resolution, and the type of incident, among other details. It's also important to maintain a centralized knowledge base that encompasses various process documents, structured and unstructured information, learnings, and process practices.

The preceding screenshot is from ServiceNow, which is a leading ITSM platform, often used by SOC/NOC as a ticketing system.
Monitoring policy
The NOC establishes and implements standard monitoring policies and procedures for performance benchmarking and capacity monitoring for organization infrastructure. To rule out false positives at the beginning of an implementation, it is imperative to set a baseline of normal activities, traffic patterns, network spikes, and other behaviors by studying the network for an initial period. It is also important to have visibility into the network at all levels and be able to detect the root cause in a short amount of time.
A well-defined investigation process
To have a robust and dependable investigation process, it is important to have a well-defined and documented process flow that utilizes the best practices and standards. A good Root Cause Analysis (RCA) is the keyto uncovering the root problems and enhancing performance and connectivity.
Reporting and dashboards
For regulatory and compliance requirements, as well as to adhere to business goals and performance metrics, it is important to have explicit reporting and dashboards for real-time visibility and situational awareness. The following screenshot shows the dashboard of ServiceNow, a leading platform that I mentioned earlier:

These reporting dashboards allow us to be aware of the current situation of the SOC/NOC and help in identifying and responding to any issues that might arise.
Escalation
A streamlined, time-sensitive escalation process with an accurate reflection of artifacts is one of the most important factors for smoothly running operations and timely responses. Analysts are told to escalate issues if they do not have the relevant reaction plan or playbook in place for the said incident, so as to get insights from the next level for the appropriate resolution.
High availability and failover
Due to the implementation setup, our monitoring capabilities might suffer as part of a network disruption. In this case, your network and security teams will be flying blind. Hence, steps should be taken to ensure that the monitoring system is up at all times and has a documented and tested BCP/DR process in place.
Apart from the ones discussed in the preceding subsections, there are several other important procedures that play a role in the overall service delivery process and incident management best practices, such as change management, problem management, and capacity and vendor management. These can be studied in detail in ITIL as part of larger ITSM practices.
Most NOCs today are innovating for better performance by including analytics for deriving insights and correlation, from AI for predicting issues and recommending best fixes, to automation and orchestration for reducing the time to respond and human errors. Today, a lot of Managed Service Providers (MSPs) are coming into the picture of managing an NOC. The reason for this is that a lot of organizations are leaning toward outsourcing their NOC operations due to perceived benefits such as improved efficiency, better reliability, less downtime, enhanced security and compliance, improved ROI, cost savings, and risk transfer. The other major benefit of outsourcing is the skilled resource and industry expertise that comes with an MSP.
Now that we know how an NOC operates and the different segments that make it operational for effective network security monitoring, let's discuss how to assess the network security's effectiveness and the efficiency of an organization.
Assessing network security effectiveness
Network security assessment addresses the broader aspects of the security functionality of a network. This should involve exploring the network infrastructure to identify the different components present in the environment and cataloging them. Ideally, this should be followed by assessing the technical architecture, technological configurations, and vulnerabilities and threats that might have been identified as part of the first step. Following this, we should focus on the ability to exploit these identified threats to validate their impact and risk factor, which may be based on a qualitative or quantitative approach. This helps us in driving accurate prioritization and business contexts, as well as the corresponding remediation plan.
Key attributes to be considered
Some of the key concepts that we will be covering in this book as part of network security will form the foundational capabilities that enable us to check the right boxes and derive an appropriate value for each. In this section, we will investigate the major domains that can help us assess the maturity of the network:
- Static analysis: This focuses on auditing application code, network and server configuration, and providing an architecture review of the network. This is exhaustive and is work and time-intensive but derives a lot of valuable insight into the inner workings of the various components and the configuration errors and vulnerabilities that may persist in the environment as they are conducted at runtime. Therefore, we need to break this into small, actionable steps such as design review, configuration review, and static code analysis.
- Dynamic analysis: This focuses on the threat actor's perspective, who aims to exploit services and threat vectors that can result in the loss of Confidentiality, Integrity, and Availability (CIA). This can be inclusive of network infrastructure testing, web application and services testing, and dynamic code analysis.
- Configuration review: This focuses on the auditing network components at a low level, such as firewalls, routers, switches, storage, and virtualization infrastructure, server and appliance operating system configuration, and application configurations. You can leverage configuration reviews to perform gap analysis and document possible flaws in the configuration and harden/mitigate the identified ones. You can also prioritize the recommended actions based on their severity and impact. The low-hanging ones should be addressed quickly.
- Design review: This concentrates on implementing security controls and evaluating their effectiveness and applicability. ISO/IEC 15408-1:2009 is an industry-recognized certification that accounts for general concepts and principles of IT security evaluation. It captures a variety of operations. The functional and assurance components are given in ISO/IEC 15408-2 and ISO/IEC 15408-3, and can be tailored for the relevant operations.
- Network infrastructure testing: This segregates network testing in the form of vulnerability assessment and penetration testing. There is a wide range of tools and platforms that can be utilized for the same that will scan the network infrastructure for potential vulnerabilities and provide a base for manual or automated testing of the explored vulnerabilities or flaws.
- Web application testing: Web application testing involves assessing an application from various approaches to test for weakness in the source code, application and business logic, authenticated and unauthenticated application processing, and configuring and implementing flaws. OWASP is a brilliant resource for digging deeper into the application security practice.
So far, we have explored the various major aspects that should form the basic building blocks of a good network security architecture. Next, we will take a look at some techno-management aspects.
The action priority matrix
The action priority matrix is an approach that helps us prioritize the findings from each of these phases and processes. This helps us identify the most important activities, along with their complexity and required time and effort. This is used by all organizations in one form or another to showcase and plan for execution.
The overall consensus reflects the following path once all the activities have been mapped:
- Quick Wins: These are activities that take less time/effort yet have a high impact.
- Major Projects: These are activities that require more time and effort and have a high impact.
- Fill-Ins: These are activities that take less time but have less impact.
- Thankless Tasks: These are activities that take a huge amount of time/effort yet don't have a sizable impact.
An example of this matrix can be seen in the following graph:
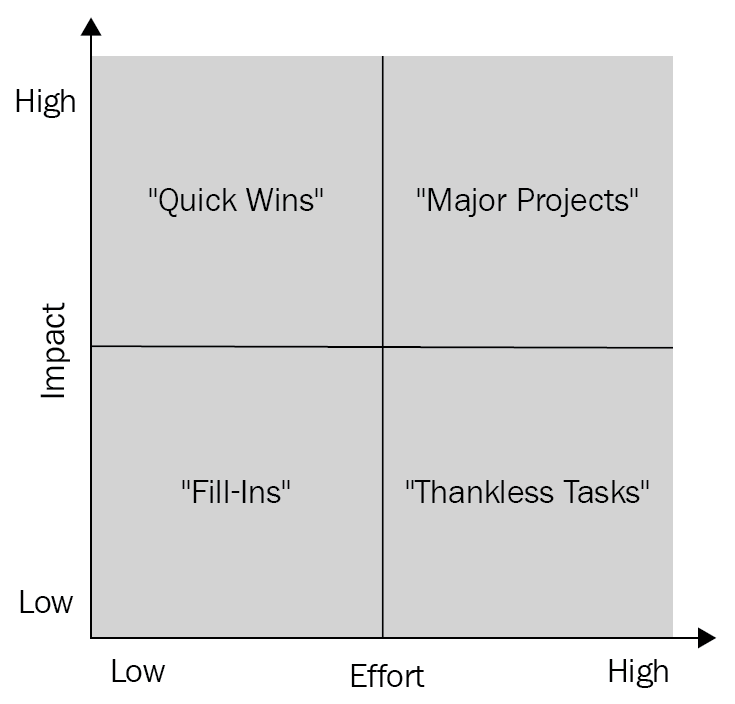
This approach provides a strategic outline to the team and helps them decide how and what to prioritize with respect to the timelines. Generally, it's recommended to aim for Quick Wins first as they provide the momentum for achieving goals in a short span of time. Then, you should focus on the major projects.
Threat modeling
This is a structured approach toward (network) security that assesses the potential threat landscape concerning the point of view of an attacker. This takes into consideration the attacker's motives, threat profile (their capability and skill), key assets of interest, and the most likely attack vector to be used, among other attributes, to understand which threats are most likely to materialize and how they will unfold in the environment. The idea behind this is to understand the environment better by reviewing all the components and processes.
Today, most threat modeling methodologies focus on one of the following approaches: asset-centric, attacker-centric, and software-centric. The following diagram shows what risk inherently means. Risk is when we have an asset that is vulnerable to a certain flaw or loophole, and we have a threat vector that can exploit the vulnerability. Ultimately, this impacts the asset and Confidentiality, Integrity, and Availability (CIA).
A + T + V = R
Here A is Asset, T is Threat, V is Vulnerability, and R is Risk:

The following steps explain the threat modeling process:
- First, the scope of the analysis is defined and each component of the application and its infrastructure is documented.
- This is followed by developing a data flow diagram that shows how each of these components interacts. This helps us assess the control mechanism. Privileges are verified for data movement.
- Then, potential threats are mapped to these components and their risk impact is quantified.
- Finally, various security mitigation steps are evaluated that might already be in place to mitigate such threats. Here, we document the requirements for additional security controls (if applicable).
On the flip side, an attacker might conduct an exercise similar to the following threat modeling:
- They would start by evaluating all possible entry points into the network/application/infrastructure.
- The next step would be to focus on the dataset or assets that would be accessible to them via these access points and then evaluate the value or possibility of using these as a pivot point.
- Post this, the attacker crafts the exploit and executes it.
Now that we have a basic understanding of the threats that we may face, it is important to have standardized frameworks that can be referred to by professionals to assess the nature of these threats and the impact they may have.
Assessing the nature of threats
You, as a security professional, can use various industrialized risk frameworks and methodologies to assess and quantify the nature of threats. Some of the prominent ones will be discussed in the following subsections.
STRIDE
STRIDE is a security framework that classifies security threats into six categories, as follows:
- Spoofing of user identity
- Tampering
- Repudiation
- Information disclosure (privacy breach or data leak)
- Denial-of-service (DoS)
- Elevation of privilege
This was developed by Microsoft to verify security concepts such as authenticity, integrity, known reputability, confidentiality, availability, and authorization.
PASTA
Process for Attack Simulation and Threat Analysis (PASTA) is a risk-centric approach focused on identifying potential threat patterns. This is an integrated application threat analysis that focuses on an attacker-centric view that security analysts can leverage to develop an asset-centric defense strategy.
It has seven stages that build up to the impact of a threat. These stages are as follows:
- Definition of the Objectives for the Treatment of Risks
- Definition of the Technical Scope
- Application Decomposition and Assertion
- Threat Analysis
- Weakness and Vulnerability Analysis
- Attack Modeling and Simulation
- Risk Analysis and Management
Next, we will take a look at the Trike framework and see how it's used for security auditing for risk management.
Trike
Trike is a framework for security auditing from a risk management outlook perspective. The process starts with defining the requirement model that the threat models are based on. The requirement model outlines the acceptable level of risk, which is associated with each asset class (the actor-asset-action matrix):

This matrix is further broken down into actions such as creating, reading, updating, and deleting, along with associated privileges such as allowed, restricted, and conditional. By following this, possible threats are specified/mapped alongside a risk value, which is based on a five-point scale for each action based on its probability.
VAST
Visual, agile, and simple threat modeling (VAST) is an agile software development methodology with a focus on scaling the process across infrastructure and SDLC. VAST aims to provide actionable outputs for various stakeholders and its scalability and usability is a key factor for its adaptability in larger organizations. The following diagram illustrates a VAST model:
VAST utilizes two threat models – the application threat model and the operational threat model. The application threat model uses process flow diagrams to represent the architectural viewpoint, whereas the operational threat model uses data flow diagrams to represent the attacker's viewpoint.
OCTAVE
Operationally critical threat, asset, and vulnerability evaluation (OCTAVE) is a security framework that's utilized for assessing risk levels and planning countermeasures against them. The focus is to reduce risk exposure to potential threats and determine the likelihood of an attack and its impact. It has three broad stages, as follows:
- Building asset-based threat profiles
- Classification of infrastructure vulnerabilities
- Creation of an overall security strategy and an activity plan for the successive exercises
It has two known formats – OCTAVE-S, which is a simplified format suitable for smaller organizations, and OCTAVE Allegro, which is a more comprehensive format suitable for large organizations.
Summary
In this chapter, we have taken a look at the foundational network security concepts and components that form the strong base that's required for a secure network implementation. Post this, we took a step-by-step dive into the various phases of building network security, which are planning and analysis, designing, building, testing, and deployment. In the second half of this chapter, we looked at an optimal NOC setup and its various attributes, such as incident management, monitoring, escalation, and reporting. Lastly, we dug into network security assessments and discussed threat modeling.
By completing this chapter, you now understand that network security is a vast domain that requires a bottom-up approach if we wish to fully understand the minute mechanisms that make it tick. As a security professional, you must have good exposure to the fundamentals of the network and the models and frameworks explained in this chapter while, at the same time, be able to identify and remediate deep-seated technical issues. I highly recommend doing a foundational assessment of the network configuration and reviewing policies and procedures in place in order to incorporate security from the inside out.
In the next chapter, we will take a look at the security concepts of cloud environments and wireless networks. We will look at the major security concerns and the industry best practices that can be considered while building or assessing a cloud environment or wireless networks for an organization.
Questions
As we conclude this chapter, here is a list of questions for you to test your knowledge regarding this chapter's content. You will find the answers in the Assessments section of the Appendix:
- Which of the following devices functions at layer 3 of the OSI model?
- Hub
- Firewall
- Switch
- Router
- Which authentication protocol uses the three-way authentication handshake?
- Kerberos
- CHAP
- PAP
- EAP
- Which of the following is not a property of STRIDE?
- Integrity
- Authentication
- Spoofing
- Authorization
- Which of these is a known OCTAVE format?
- OCTAVE - A
- OCTAVE - S
- OCTAVE - C
- OCTAVE - T
- Which of the following is not a valid phase of the network security architecture?
- Deploying
- Testing
- Scripting
- Analyzing
- The go-live support plan originates from which phase of the network security architecture?
- Deploy
- Test
- Analyze
- Build
- What component of a web application would not be part of a threat model?
- Mobile user interface
- An application's database
- Whether the website is vulnerable to hacking
- A physical threat to a company's data center
Further reading
- Network Security Overview: https://www.packtpub.com/networking-and-servers/network-security-video
- Some great books on network security:
- Applied Network Security: https://prod.packtpub.com/in/networking-and-servers/applied-network-security
- Network Security with pfSense: https://prod.packtpub.com/in/networking-and-servers/network-security-pfsense
- ISO Model: https://www.geeksforgeeks.org/layers-osi-model/
- Awake Security: Advanced Network Traffic Analysis Solution: https://awakesecurity.com/product/
- SolarWinds Network Performance Monitor: https://www.solarwinds.com/network-performance-monitor
- ManageEngine OpManager: https://www.manageengine.com/network-monitoring/
- Paessler PRTG Network Monitor: https://www.manageengine.com/network-monitoring/
- ServiceNow - NOC: IT Operations Management: https://www.servicenow.com/products/it-service-management.html
- Top Alternative to ServiceNow: https://freshdesk.com/ and https://www.spiceworks.com/
- Open Source Alternatives: https://osticket.com/, https://www.bugzilla.org/, and https://www.mantisbt.org
- Videos for learning more about PASTA and its implementation: https://www.owasp.org/images/a/aa/AppSecEU2012_PASTA.pdf
- Understanding more about various threat modeling approaches: https://insights.sei.cmu.edu/sei_blog/2018/12/threat-modeling-12-available-methods.html
- Source Code Analysis Tools: https://www.owasp.org/index.php/Source_Code_Analysis_Tools
- CIS Critical Security Controls: https://www.cisecurity.org/controls/cis-controls-list/
- Microsoft Threat Modeling Tool 2016: https://www.microsoft.com/en-us/download/details.aspx?id=49168


























