This recipe describes how to configure the Wide Area Network (WAN) on the external interface of our firewall.
The WAN interface is your connection to the outside world. You'll need a properly configured WAN interface (as described in the previous chapter) and an Internet connection. In this example, a cable modem provides the Internet connection from our local Internet Service Provider (ISP), but pfSense will support every other major connection method.
Browse to Interfaces | WAN.
Check Enable Interface.
Choose an address configuration Type.
Leave MAC address blank. Manually entering a MAC address here is known as "spoofing". Your ISP has no way of verifying MAC addresses, so you can simply make one up. This can be helpful if you're trying to force your ISP to hand you a new IP address or a different set of DNS servers.
Leave MTU, MSS, Hostname, and Alias IP address blank.

Check Block private networks. This setting is usually only checked on a WAN interface.
Check Block bogon networks. This setting is usually only checked on a WAN interface.
Save changes.

We must first establish our connection to the Internet before we can configure pfSense to allow our other networks to access it. The example we've performed is typical of many SOHO environments. By placing our firewall as the only machine with direct access to the Internet, we are securing our environment by establishing complete control over the traffic that flows in and out of our networks. All traffic must now pass through our firewall and abide by our rules.
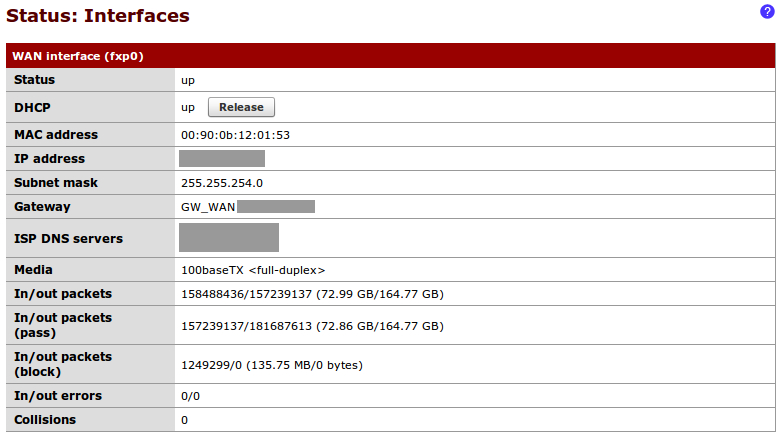
We can now connect our WAN device (cable modem) to the WAN Ethernet port we've defined on our pfSense box. Once the connection has been established, we can check the status of our WAN port from Status | Interfaces: