Cloud computing security refers to the set of techniques, protection controls, and security policy to secure the application, data, and related infrastructure components on the cloud infrastructure.
While the introduction of cloud computing and big data in organizations helps solve the maintenance overhead of on premise software, platform, and/or infrastructure, this model also reminds us of the security concerns as aforementioned are being maintained on third-party data centers. Even though the cloud application providers are coming up their own security features, application teams should ensure that their components are deployed with application security in the cloud practice.
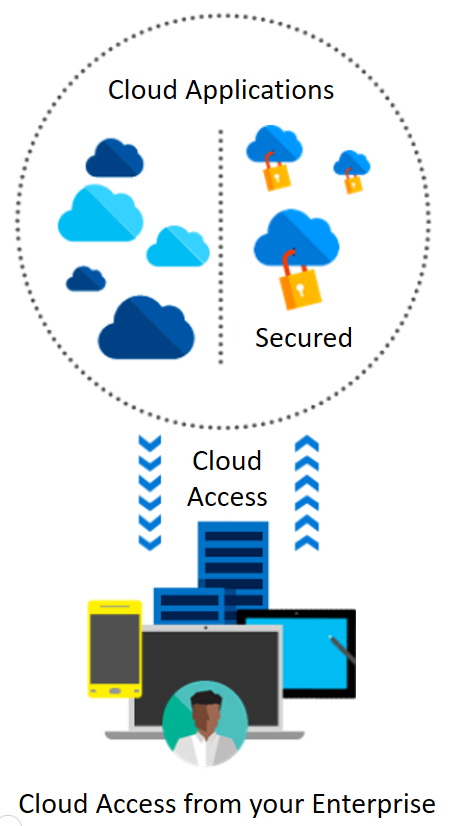
Cloud security controls such as deterrent, preventive, detective, and corrective controls are referred by security management to address the cloud security issues.
Different security policies such as identity management (SSO/CloudID) and the physical and privacy policy (data masking / encryption...



