If you choose to install Splunk on a Linux machine, these are the instructions you need to follow. Take your time and do not rush the installation. For this Linux installation, the steps assume you will run Splunk in your user profile's home directory:
- Decompress the .tgz file you downloaded. The result of the decompression is a splunk folder and all the related Splunk files contained inside.
- Change the working directory to $SPLUNK_HOME/bin.
- Run the following command to start Splunk for the first time:
./splunk start
- Accept the Splunk license when prompted.
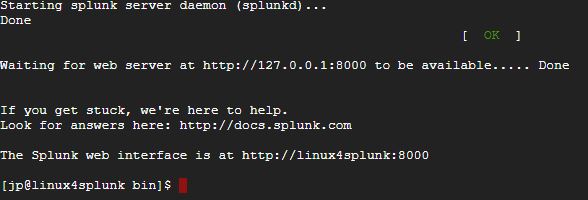
- Splunk will start successfully and the end results should appear like this: