The bar across the top of the window contains information about where you are as well as quick links to preferences, other apps, and administration.
The current app is specified in the upper-left corner. The following screenshot shows the upper-left Splunk bar when using the Search & Reporting app:
Clicking on the text takes you to the default page for that app. In most apps, the text next to the logo is simply changed, but the whole block can be customized with logos and alternate text by modifying the app's CSS. We will cover this in Chapter 8, Working with Apps:
The upper-right corner of the window, as seen in the previous screenshot, contains action links that are almost always available:
The name of the user who is currently logged in appears first. In this case, the user is
Administrator. Previously, clicking on the username allowed you to selectEdit Account(which would take you to theYour accountpage) orLogout(of Splunk). In version 7.0, it's a bit different. The first option is now listed asAccount Settings, which opens a settings page similar to prior versions (below is the 7.0 page).Logoutis the other option, and, like prior versions, it ends the session and forces the user to log in again.
The following screenshot shows what the your account page looks like:
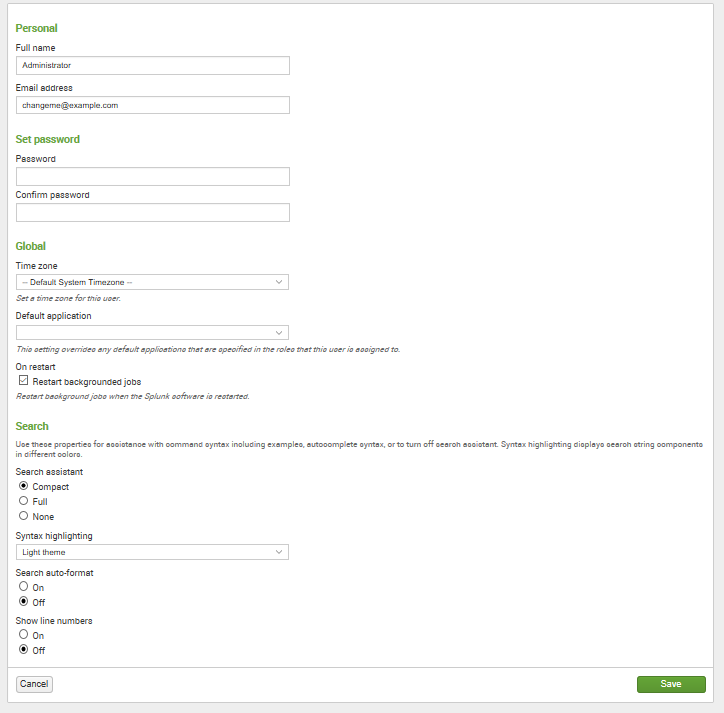
This form presents the global preferences that a user is allowed to change. Other settings that affect users are configured through permissions on objects and settings on roles. (Note that preferences can also be configured using the command-line interface or by modifying specific Splunk configuration files.) Preferences include the following:
Full nameandEmail addressare stored for the administrator's convenience.Set passwordallows you to change your password. This is relevant only if Splunk is configured to use internal authentication. For instance, if the system is configured to use Windows Active Directory via LDAP (a very common configuration), users must change their password in Windows.Global/Time zonecan be changed for the logged-in user.
Note
Setting the time zone only affects the time zone used to display the data. It is very important that the date is parsed properly when events are indexed. We will discuss this in detail in >Chapter 2, Understanding Search.
Default applicationcontrols where you first land after login. Most users will want to change this to search.Restart backgrounded jobscontrols whether unfinished queries should run again if Splunk is restarted.Search/Search assistant/Syntax highlighting/auto-format and Show line numbers: these properties are used for assistance with command syntax, including examples, autocomplete syntax, or to turn off search assistance. Syntax highlighting displays search string components in different colors.Messagesallows you to view any system-level error messages you may have pending. When there is a new message for you to review, a notification displays as a count next to theMessagesmenu. You can click on theXto remove a message.- The
Settingslink presents the user with the configuration pages for all SplunkKnowledgeobjects,Distributed environment,SystemandLicensing,Data, andUsers and Authenticationsettings. For any option that you are unable to see, you do not have the permissions to view or edit it:
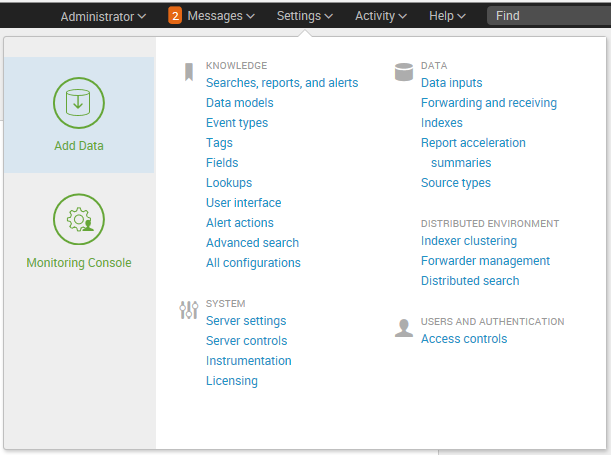
- The
Activitymenu lists shortcuts to SplunkJobs,Triggered Alerts, and (in previous versionsSystem Activity)views. - You can click on
Jobs(to open the search jobs manager window, where you can view and manage currently running searches) orTriggered Alerts(to view scheduled alerts that are triggered).
Note
Note: In version 7.0, System Activity (to see dashboards about user activity and status of the system) has been removed from under Activity. You can actually access all of this detailed information in Search!
Findcan be used to search for objects within your Splunk Enterprise instance. These saved objects includeReports,Dashboards,Alerts, and so on. Errors can be searched with theSearch & Reportingapp by clicking onOpen errorin search.




