Overview of this book
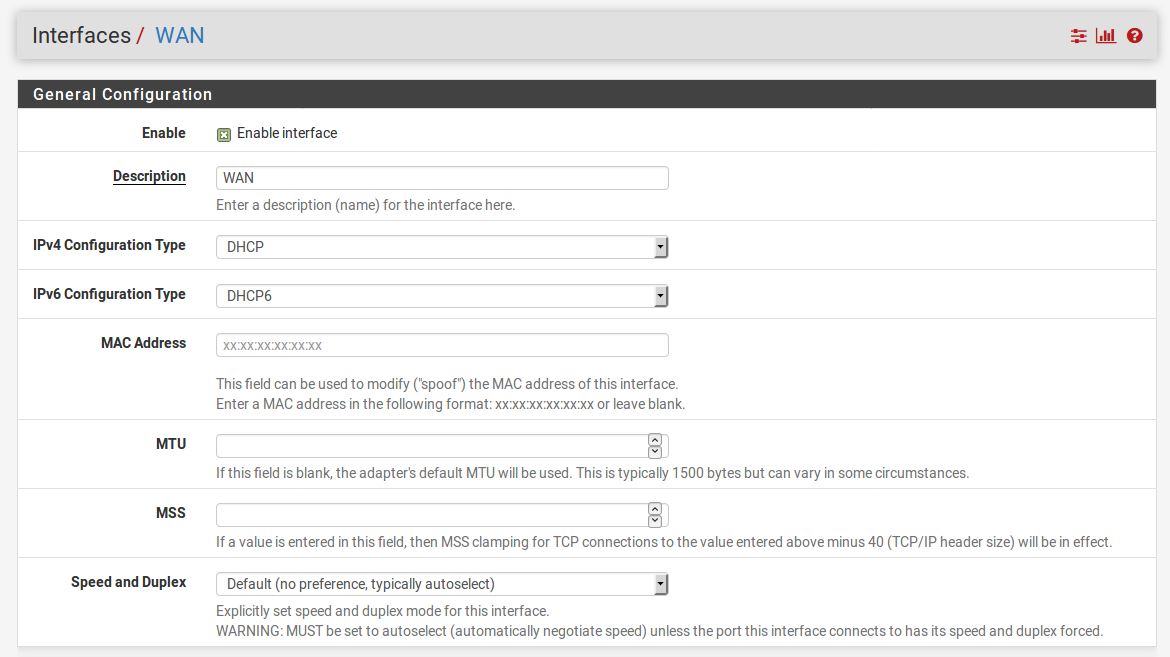
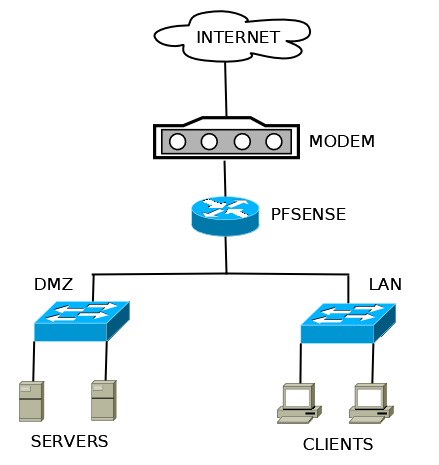
pfSense is an open source distribution of the FreeBSD-based firewall that provides a platform for ?exible and powerful routing and firewalling. The versatility of pfSense presents us with a wide array of configuration options, which makes determining requirements a little more difficult and a lot more important compared to other offerings.
pfSense 2.x Cookbook – Second Edition starts by providing you with an understanding of how to complete the basic steps needed to render a pfSense firewall operational. It starts by showing you how to set up different forms of NAT entries and firewall rules and use aliases and scheduling in firewall rules. Moving on, you will learn how to implement a captive portal set up in different ways (no authentication, user manager authentication, and RADIUS authentication), as well as NTP and SNMP configuration. You will then learn how to set up a VPN tunnel with pfSense. The book then focuses on setting up traffic shaping with pfSense, using either the built-in traffic shaping wizard, custom ?oating rules, or Snort. Toward the end, you will set up multiple WAN interfaces, load balancing and failover groups, and a CARP failover group. You will also learn how to bridge interfaces, add static routing entries, and use dynamic routing protocols via third-party packages.



 Free Chapter
Free Chapter