Let's discuss the three main categories of updates that determines how you keep your system up-to-date and working in optimum conditions. The three broad categories we will discuss here are security updates, kernel updates, and application updates.
It is recommended that server administrators install the security patch updates as soon as it becomes available. However, if a particular package isn't being used in the server, then you may skip the security update for that particular package. Depending on your need, you may choose and install the security updates.
Administrators can refer to Ubuntu Security Notices (USN) to understand the security updates available and if they should be installing a particular update. USN can be accessed at http://www.ubuntu.com/usn/. The admins can also subscribe to RSS feeds for these security updates.
It may seem like kernel updates are of the utmost importance and they should be applied as soon as the updates are available. But it is tricky, as updates to kernel can actually cause some programs not to function in a proper way. Kernel updates rectify the security issues but have to be updated only after considering and making sure that other applications' behavior won't be hampered with it.
By default, the package management tools such as apt-get, aptitude, and synaptic enable the kernel updates. For command-line tools, you can disable automatic kernel updates using the following command:
sudo aptitude hold linux-image-name
Admins need to be careful when installing the application updates. A case may arise wherein some of the functionality of other packages may not work after installing the update. Refer to USN and other Ubuntu related forums to keep yourself updated about the possible application updates and the issues faced by other users.
The unattended-upgrades package can be used to schedule and enforce rules on what packages to be updated and what packages should be restricted from upgrading itself. To use this, install the unattended-upgrades package using the following command:
sudo apt-get install unattended-upgrades
Once the package is installed, configure the unattended-upgrades package in the following file and make necessary changes as per your needs. I am opening the file in the Nano editor:
nano /etc/apt/apt.conf.d/50unattended-upgrades
The output of this command is shown in the following screenshot:
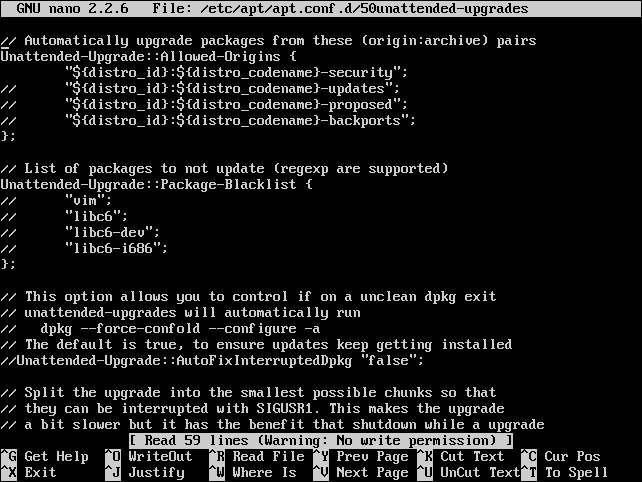
The first section is for the packages where you want to allow automatic upgrades. Here, the first line for security is enabled, so the security updates will be installed by default. The // symbol means the lines are commented and will not be evaluated, as shown here:
Unattended-Upgrade::Allowed-Origins { "Ubuntu precise-security"; // "Ubuntu precise-updates"; };The second section is for the blacklisted packages. You put the package names here for which you want to disable automatic updates. Again, // has the same meaning—those lines will not be evaluated. Add the packages in this section to blacklist them and disallow automatic updates:
Unattended-Upgrade::Package-Blacklist { // "vim"; // "libc6"; // "libc6-dev"; // "libc6-i686"; };One last step is to enable the automatic updates by setting the appropriate configuration in the /etc/apt/apt.conf.d/10periodic file, as shown in the following screenshot:

In this example, the interval is set to 1, which means the packages list will be updated, packages will be downloaded, and they will be upgraded every day.



