There are three levels of security deployed within MicroStrategy. These levels are depicted in the following diagram:
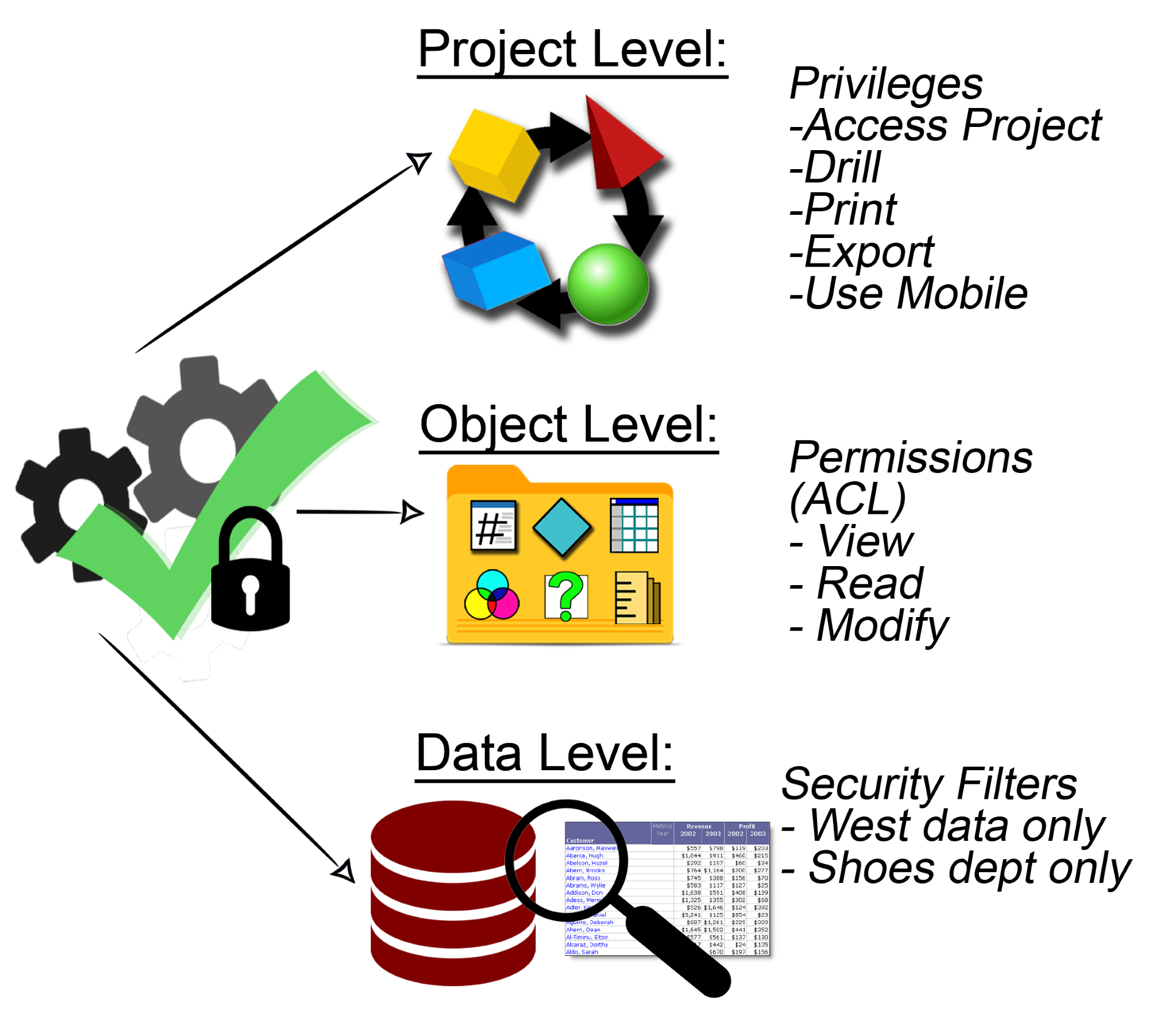
This level applies to an entire Project. The objects used to enforce Project-level security are:
- Users
- User Groups
- Security Roles
These three objects could grant or constrain functionality within a Project.
It is key to understand the difference between a MicroStrategy privilege and a permission. The privilege is always tied to functionality. That is, what a user can or can't do on a given Project and with a given client application. Examples of privileges are report manipulations such as sort, drill, print, and export; use of object editors for developing purposes such as the use of Document or Intelligent Cube editors; and use of certain client applications such as Integrity Manager, Object Manager, and MicroStrategy Mobile, to mention a few. The permissions, on the other hand, are tied to access to objects and folders within...



