So how does all this tie together? What makes for a solid ICS architecture? To answer this question, we should first discuss the Purdue reference model, or Purdue model for short. As shown in the following figure, Purdue model was adopted from the Purdue Enterprise Reference Architecture (PERA) model by ISA-99 and used as a concept model for ICS network segmentation. It is an industry adopted reference model that shows the interconnections and interdependencies of all the main components of a typical ICS.
The model is a great resource to start the process of figuring out a typical modern ICS architecture:

The Purdue model will be discussed in more detail in a later chapter, but for now, to support our architecture discussion, let's look at a high-level overview. The following sections are based on the complete ICS architecture shown at the beginning of the chapter.
The Purdue model divides this ICS architecture into three zones and six levels. Starting from the top, these are:
- Enterprise:
- Level 5: Enterprise network
- Level 4: Site business and logistics
- Industrial Demilitarized zone.
- Manufacturing zone (also called the Industrial zone):
- Level 3: Site operations
- Level 2: Area supervisory control
- Level 1: Basic control
- Level 0: The process
The enterprise zone is the part of the ICS where business systems such as ERP and SAP typically live. Here, tasks such as scheduling and supply chain management are performed.

The enterprise zone can be subdivided into two levels:
- Level 5: Enterprise network
- Level 4: Site business and logistics
The systems on the enterprise network normally sit at a corporate level and span multiple facilities or plants. They take data from subordinate systems out in the individual plants and use the accumulated data to report on the overall production status, inventory, and demand. Technically not part of the ICS, the enterprise zone relies on connectivity with the ICS networks to feed the data that drives the business decisions.
Level 4 is home to all the Information Technology (IT) systems that support the production process in a plant of a facility. These systems report production statistics such as uptime and units produced for corporate systems and take orders and business data from the corporate systems to be distributed among the Operation Technology (OT) or ICS systems.
Systems typically found in level 4 include database servers, application servers (web, report, MES), file servers, email clients, supervisor desktops, and so on.
The following figure explains the Industrial Demilitarized Zone in detail:
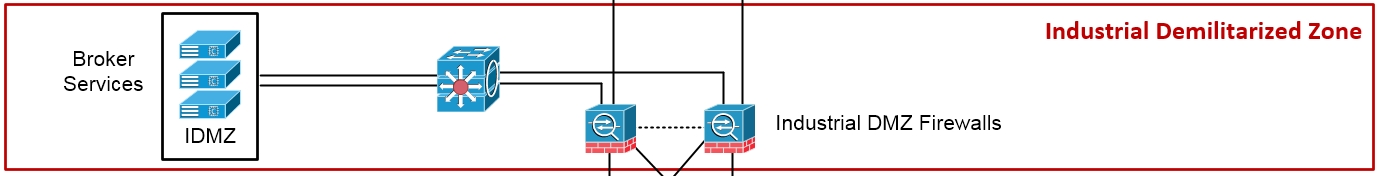
In between the enterprise zone and systems and the Industrial zone lies the Industrial Demilitarized Zone or IDMZ. Much like a traditional (IT) DMZ, the OT-oriented IDMZ allows you to securely connect networks with different security requirements.
The IDMZ is the result of the efforts taken to create security standards such as the NIST Cybersecurity Framework and NERC CIP. The IDMZ is an information sharing layer between the business or IT systems in levels 4 and 5 and the production or OT systems in levels 3 and lower. By preventing direct communication between IT and OT systems and having a broker service in the IDMZ relay the communications, an extra layer of separation and inspection is added to the overall architecture. Systems in the lower layers are not directly exposed to attacks or compromise. If something were to compromise a system at some point in the IDMZ, the IDMZ could be shut down, the compromise could be contained, and production could continue.
Systems typically found in the Industrial Demilitarized Zone include (web) proxy servers, database replication servers, Microsoft domain controllers, and so on.
The following figure explains the various manufacturing zones:

The manufacturing zone is where the action is; it is the zone where the process lives, by all means, this is the core of the. The manufacturing zone is subdivided into four levels:
- Level 3: Site operations
- Level 2: Area supervisory control
- Level 1: Basic control
- Level 0: The process
Level 3 is where systems that support plant wide control and monitoring functions reside. At this level, the operator is interacting with the overall production systems. Think of centralized control rooms with HMIs and operator terminals that provide an overview of all the systems that run the processes in a plant or facility. The operator uses these HMI systems to perform tasks such as quality control checks, managing uptime, and monitoring alarms, events, and trends.
Level 3, site operations, is also where the OT systems that report back up to IT systems in level 4 live. Systems in lower levels send production data to data collection and aggregation servers in this level, which can then send the data to higher levels or can be queried by systems in higher levels (push versus pull operations).
Systems typically found in level 3 include database servers, application servers (web and report), file servers, Microsoft domain controllers, HMI servers engineering workstations, and so on.
Many of the functions and systems in level 2 are the same as for level 3 but targeted more toward a smaller part or area of the overall system. In this level, specific parts of the system are monitored and managed with HMI systems. Think along the lines of a single machine or skid with a touch screen HMI to start or stop the machine or skid and see some basic running values and manipulate machine or skid-specific thresholds and set points.
Systems typically found in level 2 include HMIs (standalone or system clients), supervisory control systems such as a line control PLC, engineering workstations, and so on.
Level 1 is where all the controlling equipment lives. The main purpose of the devices in this level is to open valves, move actuators, start motors, and so on. Typically found in level 1 are PLCs, Variable Frequency Drives (VFDs), dedicated proportional-integral-derivative (PID) controllers, and so on. Although you could find a PLC in level 2, its function there is of supervisory nature instead of controlling.
Level 0 is where the actual process equipment that we are controlling and monitoring from the higher levels lives. Also known as Equipment Under Control (EUC), level 1 is where we can find devices such as motors, pumps, valves, and sensors that measure speed, temperature, or pressure. As level 0 is where the actual process is performed and where the product is made, it is imperative that things run smoothly and uninterrupted. The slightest disruption in a single device can cause mayhem for all operations.



