Open Shortest Path First (OSPF) is an Interior Gateway Routing Protocol and uses the concept of Autonomous Systems (AS). AS is either a single network or a group of networks controlled by a common network administrator (or organization). Each router has an identical database that includes information on:
The single router
The current state of a router
The state of the router's interfaces
Reachable neighbors
The aforementioned database is called Link State Database (LSDB) and is built on each OSPF router receiving LSA (Link-state advertisement , the base communication of the router's local routing topology) from every other router in the same AS. To keep track of LSAs in the LSDB, each router is assigned a router ID. It is a 32-bit dotted decimal number that is unique to the AS. The router ID identifies the router in the AS and usually is the largest or smallest IP address assigned to the router. IP addresses are unique so this convention ensures that the OSPF router IDs are also unique.
To minimize the routing traffic and the amount of information required, OSPF allows to group networks into a set, called an area (identified through a 32-bit area ID expressed in dotted decimal notation). The topology of an area is hidden from the rest of the autonomous system. Routing takes place on two levels, entirely within an area (intra-area routing) or in another area (inter-area routing). To link together multiple areas and to allow inter-area routing, OSPF uses the concept of Backbone. An OSPF backbone is made by routers linking the other areas (that is, all the areas must have a direct or virtual connection to the backbone). Such connections are maintained by an interconnecting router, known as Area Border Router (ABR). An ABR maintains separate link state databases for each area it serves and maintains summarized routes for all areas in the network. An OSPF internetwork always has at least one backbone area. The backbone has the reserved area ID of 0.0.0.0 (and is also known as area 0). Inter-area traffic is routed to the backbone, then to the destination area, and finally to the destination host. Routers on the backbone also advertise the summarized routes within their areas to the other routers on the backbone.
A router configured with the OSPF protocol tries to find its neighbors (other routers using OSPF, connected to the same subnet, and that are part of the same area). As soon as their LSDB is synchronized, the two routers are said to be adjacent. Routing protocol packets are only passed between adjacent routers.
The last aspect to be discussed is that when routers are connected to the same broadcast segment (for example, same VLAN on the same switch) only one router maintains adjacencies with all other routers on the segment. This is the Designated Router (DR). Having a single router do all this reduces the network traffic and collisions. For redundancy purposes a Backup Designated Router (BDR) is also elected. An election chooses the DR and BDR from all the available routers. The election is based on the priority setting of the routers and (to resolve any tie) the router with the highest router ID is elected. We are able to configure the priority value so that a router is always or never elected (highest priority will always win on lowest values).
On each router that uses OSPF we will have to configure:
Router ID
Area
Network
Interfaces
Navigate to the Router | Dynamic | OSPF pane, router ID is defined here as we can see in the following screenshot:

The advanced options enable the router to redistribute directly connected networks, static routes configured on the device, and information coming from other routing process (RIP and BGP) using the OSPF routing updates. The metric of the aforementioned routes can be changed from the default value.
The redistribution of routes, at this level, is not selective, but works on an entire category (for example, re-transmit all the routes directly connected to the router). We'll probably filter some routes using access lists (ACLs). An ACL is a list of rules that are applied from the top of the list. Each rule in an access list consists of an IP address, a subnet mask, and an action (permit or deny). If no matching rule is found, the default action is always a deny. The ACLs are configured from the CLI with the config router access-list command. A more detailed explanation can be found in the FortiOS CLI Reference for FortiOS 5.0 at http://docs.fortinet.com/fgt/handbook/50/fortigate-cli-50.pdf.
In the aforementioned OSPF pane we are able to create one or more OSPF areas. The configuration screen is shown in the following screenshot:
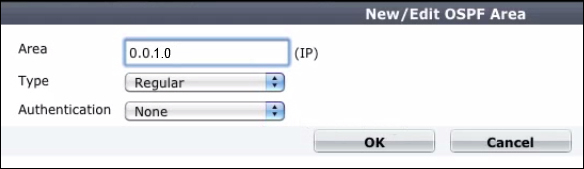
An OSPF area can be a:
Backbone Area (Area 0): This area is always required and is used to link together different areas. Sometimes this is the only OSPF area used.
Not-So-Stubby-Area (NSSA): Propagates external (not OSPF) routers presenting them to the other router as OSPF members.
Stub Area: Stub area can contain a single entry and exit point (a single ABR), or multiple ABRs when any of the ABRs can be used to reach external route destinations.
Regular Area: Area can be connected to the backbone by physical or virtual link. Regular area can contain both internal and external routes.
All OSPF packet traffic is authenticated and we have three options:
Null Authentication: There is no authentication being used (none option).
Simple Password Authentication: We will use a plain text string. It is not a strong form of security because passwords are exchanged in clear text on the network.
Cryptographic Authentication: Use a shared secret key based on the open MD5 (Message Digest type 5) standard encryption to authenticate all router traffic on a network.




