In this recipe, we will configure Orchestrator with an external LDAP or Active Directory service. VMware best practice is to use Orchestrator together with SSO, which is described in the Integrating Orchestrator into SSO and vSphere Web Client recipe. This recipe doesn't work with the vRA-integrated Orchestrator.
You need a supported LDAP service configured and running. The following LDAP services are supported in vCO 5.5:
Windows Server 2008 Active Directory
Windows Server 2012 Active Directory
OpenLDAP
Novell eDirectory Server 8.8.3
Sun Java System Directory Server 6.3
We also need to create a group and a user in these services, so you should have access to these services.
You should be comfortable with using one of the methods described in the Two ways to configure Orchestrator recipe.
If your LDAP (AD) requires SSL (Kerberos), you will need to import the SSL certificate first (see the Important Orchestrator base configurations recipe in this chapter.
We will focus on linking Orchestrator to AD. Connecting Orchestrator to LDAP is pretty much the same procedure; for anyone who understands LDAP, this will be a breeze.
AD is basically the same as LDAP but most Windows administrators have problems with the LDAP representation of AD, which is why we focus on AD in this recipe.
We will configure SSO in the Integrating Orchestrator into SSO and vSphere Web Client recipe.
Before we can add an external LDAP, we need to configure at least one group and one user. To do this, perform the following steps:
Log in to your LDAP or AD.
Create an Orchestrator Administrator group and an Orchestrator Administrator user.
Make the Orchestrator Administrator user a member of the Orchestrator Administrator group.
For this example, I have created a user called vcoadmin as well as a group called vcoadmins in AD. The AD domain is called mylab.local.
Again, we will show both methods.
Click on the Authentication section.
In LDAP client, select Active Directory.
In the Primary LDAP host field, enter
mylab.localas the Active Domain DNS name.The standard port for Microsoft Active Directory LDAP is 389.
Enter
dc=mylab,dc=localas the root for your domain.If you have secured your AD with Kerberos, you need to activate SSL (don't forget to import the SSL certificate first).
The username can be entered in both formats: user@Domain or domain\user. The user can be any active user within the AD; however, its best to use Orchestrator Admin.
The user and group lookup base is easiest set to the root of your domain, for example,
dc=mylab,dc=local. However, if your AD or LDAP is large, performance-wise it might be better to choose a different root.The Orchestrator Admin group path can be easily found. Enter the name of the group (case-sensitive) and click on Search to the right.
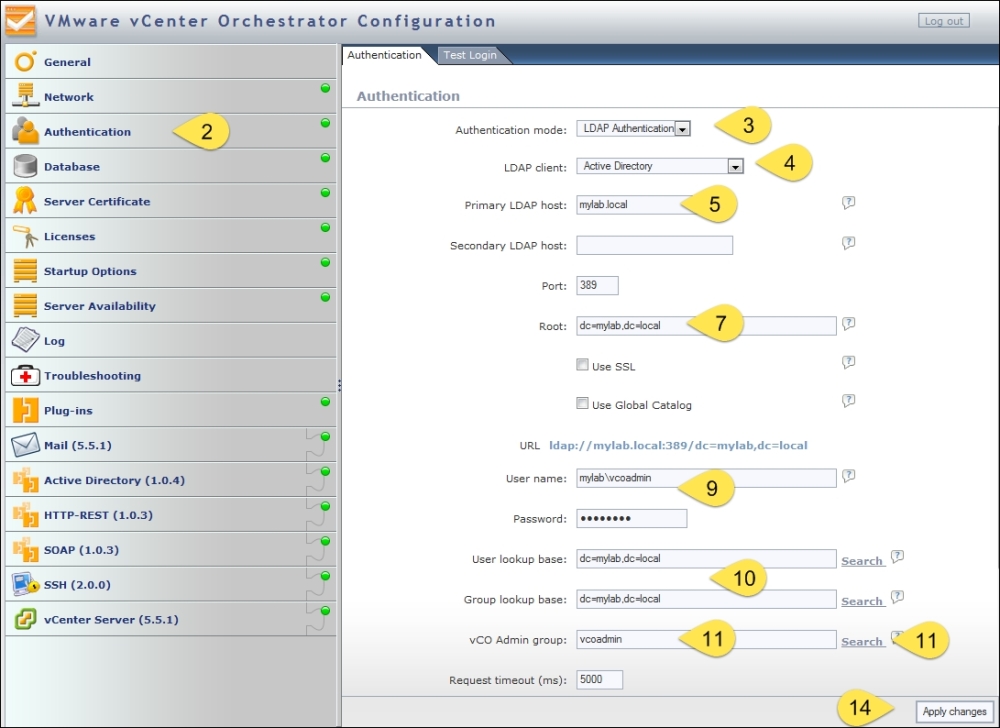
If the name has been entered correctly, the path should be shown. Click on the LDAP path. The path is now populated with the correct setting.

The rest of the settings can be left alone for most AD settings.
Click on Apply changes.
At this stage, you should try the test login described in the There's more... section of this recipe.
Click on Startup Options and then restart the Orchestrator Server.
Now, try to log in to the Orchestrator Client using the AD user.
Navigate to Library | Configuration | Authentication | LDAP.
Right-click on the workflow Configure Active Directory and select Start Workflow.
In the primary host, enter
mylab.localas the Active Domain DNS name.The standard port for AD LDAP is 389.
If you secured your AD with Kerberos, you need to activate SSL.
Click on Next.
Enter
dc=mylab,dc=localas the root for your domain.The username can be entered as [email protected] or domain\user. The user can be any active user in the AD; however, its best to use Orchestrator Admin.
The user and group lookup base is easiest set to the root of your domain, for example,
dc=mylab,dc=local. However, if your AD or LDAP is large, it might be performance-wise better to choose a different root.The Orchestrator Admin group needs to be constructed, but there is no automated tool for it. We use the
CN=vcoadmins,CN=Users,DC=MyLab,DC=localvalues.Click on Submit and wait until the workflow is successfully completed.

Sadly, there isn't a test to check whether your settings are correct as there is with the Configuration tool. Have a look at the test login described in the There's more... section of this recipe.
There is no workflow to restart Orchestrator Server, so you have to restart the Orchestrator Server another way:
In Windows, use services (vCenter Orchestrator Server)
In Linux, use the services command from the OS or use the Orchestrator Configurator (see the Tuning the appliance recipe in Chapter 2, Optimizing Orchestrator Configuration)
Reboot the Orchestrator Server
Now, try to log in to the Orchestrator Client using the AD user.
Configuring Orchestrator to work with an external authentication enables AD users to log in to the Orchestrator Client. The alternative would be either having only one user using it or adding users to the embedded LDAP. However, for a production Orchestrator, the embedded LDAP solution is not viable. As SSO is now a highly integrated part of vSphere, using Orchestrator with AD (or LDAP) isn't really such a good solution any longer. SSO can proxy multiple AD and/or LDAP domains and lets you integrate Orchestrator directly into vCenter as well as other corner pieces of VMware software offerings, making SSO integration the better choice for the future.
In the recipe above, we used the domain DNS address as the primary LDAP host rather than an individual AD server. The DNS entry for AD will forward the LDAP query to the next available AD server, which makes it a more reliable choice.
There are some things you should be aware of when working with LDAP.
In order to find out whether everything is working as it should, we need to test it. However, there is no workflow for this, so you have to trust your entries or use the Configuration tool.
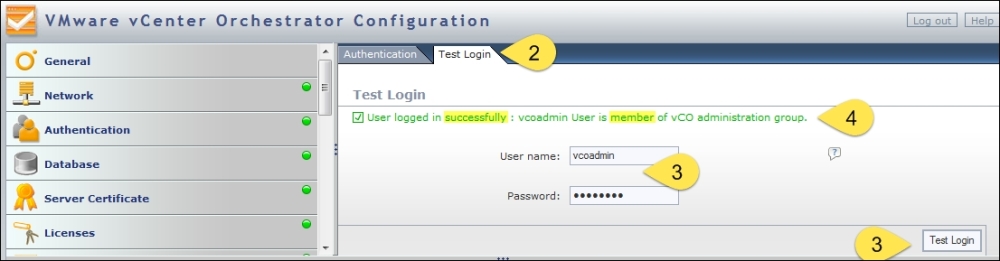
Using the Orchestrator Configuration tool, click on Authentication.
Click on the Test Login tab.
Enter the Orchestrator Admin username and its password and click on Test Login.
Read the message carefully. It should be green and confirm that you can log in and that the user is part of the Orchestrator Admin group.
A red message mostly indicates that the user provided isn't in the LDAP or that the password is wrong.
If the message doesn't confirm an Orchestrator Admin group membership, review the membership of the user account.
When you encounter a problem while setting up LDAP, you will get an error code. This table shows the most commonly encountered error codes:
|
Code |
Meaning |
What to do |
|---|---|---|
|
525 |
User not found |
The user for login isn't found; check whether you have written the domain correctly. |
|
52e |
Password is incorrect |
Change the password in the password field. |
|
530 531 |
The User is not allowed to log in |
Access LDAP or AD and make sure that the user is allowed to log in remotely and from Orchestrator Server. |
|
532 |
Password expired |
Access LDAP or AD and set a new password. |
|
533 |
Account disabled |
Access LDAP or AD and enable the account. |
|
701 |
Account expired |
Access LDAP or AD and create a new account or use a different user. |
|
773 |
Must reset password |
The User has to reset the password on login. Access LDAP or AD to set a new password or use other methods to set a new password. |
|
775 |
User locked |
Access LDAP or AD and unlock the user account. |



