After understanding the problem and deciding to use Wireshark, the first step would be to decide where to locate it. For this purpose, we need to have a precise network diagram (at least the part of the network that is relevant to our test).
The principle is to locate the device that you want to monitor, connect your laptop to the same switch that it is connected to, and configure a port mirror or monitor to the monitored device. This operation enables you to see all traffic coming in and out of the monitored device.
You can monitor a LAN port, WAN port, server or router port, or any other device connected to the network.
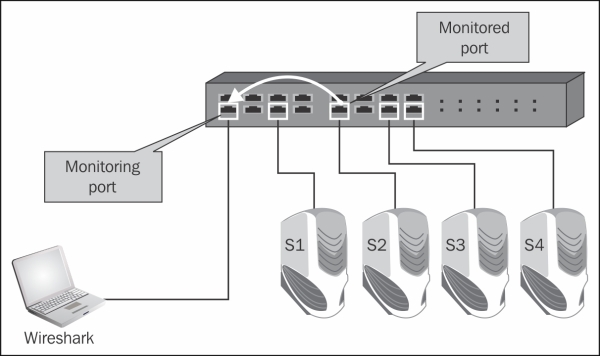
In the preceding diagram, the Wireshark software (installed on the PC on the left) and the port mirror, also called port monitor (configured on the switch in the direction as in the diagram), will monitor all the traffic coming in and out of server S2. Of course, we can also install Wireshark directly on the server itself, and by doing so, we will be able to watch the traffic directly on the server.
Some LAN switch vendors also enable other features such as:
Monitoring a whole VLAN: We can monitor a server's VLAN, Telephony VLAN, and so on. In this case you will see all the traffic on a specific VLAN.
Monitoring several ports to a single analyzer: We can monitor traffic on servers S1 and S2 together.
Filtering: Filtering means choosing and accordingly configuring whether to monitor incoming traffic, outgoing traffic, or both.
To start working with Wireshark, go to the the Wireshark website, and download the latest version of the tool.
An updated version of Wireshark can be found on the website at http://www.wireshark.org/, under the Download heading. Download the latest Wireshark stable release that is available at http://www.wireshark.org/download.html.
Each Wireshark Windows package comes with the latest stable release of WinPcap, which is required for live packet capture. The WinPcap driver is a Windows version of the UNIX Libpcap library for traffic capture.
Let's take a look at the typical network architecture and network devices, how they work, how to configure them when required, and where to locate Wireshark.
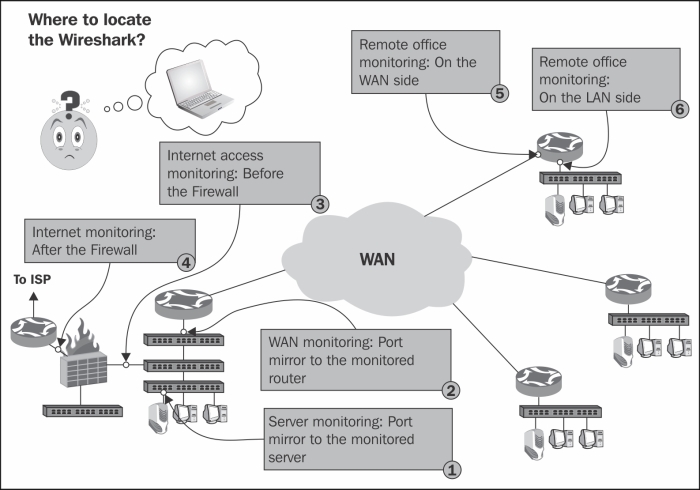
Let's have a look at the simple and common network architecture in the preceding diagram.
This will be one of the most common requirements that we will have. It can be done by either configuring the port monitor to the server (numbered as 1 in the preceding diagram), or installing Wireshark on the server itself.
In order to monitor a router, we can monitor a LAN port (numbered as 2 and 6 in the preceding diagram), or a WAN port (numbered as 5 in the preceding diagram). To monitor a LAN port is easy—simply configure the port monitor to the port you wish to monitor. In order to monitor a WAN port, you can connect a switch between the router port and the Service Provider (SP) network, and configure the port monitor on this switch, as in the following illustration.
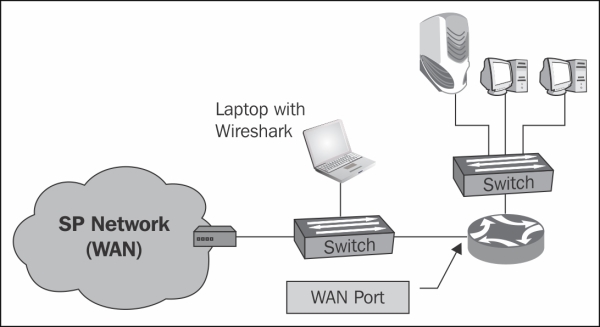
Connecting a switch between the router and the service provider is an operation that breaks the connection; however, when you prepare for it, it should take less than a minute.
When monitoring a router, don't forget—not all packets coming in to a router will be forwarded. Some packets can be lost, dropped on the router buffers, or routed back on the same port that they came in from.
Two additional devices that you can use are TAPs and Hubs.
TAPs: Instead of connecting a switch on the link you wish to monitor, you can connect a device called Test Access Point (TAP), which is a simple three-port device that, in this case, will play the same role as that of the switch. The advantage of a TAP over a switch is its simplicity and price. TAPs also forward errors that can be monitored on Wireshark, unlike a LAN switch that drops them. Switches, on the other hand, are much more expensive, take a few minutes to configure, but provide you with additional monitoring capabilities, for example, Simple Network Management Protocol (SNMP). When you troubleshoot a network, it is better to have an available managed LAN switch, even a simple one.
Hubs: You can simply connect a hub in parallel to the link you want to monitor, and since a hub is a half-duplex device, every packet sent between the router and the SP device will be watched on your Wireshark. The biggest con of this method is that the hub itself slows the traffic, and it therefore influences the test. In many cases you also want to monitor 1 Gbps ports, and since there is no hub available for this, you will have to reduce the speed to 100 Mbps, which again will influence the traffic. Therefore, hubs are not commonly used.
When monitoring a firewall, it differs depending on whether you monitor the internal port (numbered 3 in the diagram) or the external port (numbered 4 in the diagram). On the internal port you will see all the internal addresses and all traffic initiated by the users working in the internal network, while on the external port you will see the external addresses that we go out with (translated by NAT from the internal addresses); you will not see requests from the internal network that were blocked by the firewall. If someone is attacking the firewall from the Internet, you will see it (hopefully) only on the external port.
To understand how the port monitor works, it is first important to understand the way that a LAN switch works. A LAN switch forwards packets in the following way:
The LAN switch continuously learns about the MAC addresses of the devices connected to it.
Now, if a packet is sent to a destination MAC, it will be forwarded only to the physical port that the switch knows this MAC address is coming from.
If a broadcast is sent, it will be forwarded to all the ports of the switch.
If a multicast is sent and Cisco Group Management Protocol (CGMP) or Internet Group Management Protocol (IGMP) is disabled, it will be forwarded to all the ports of the switch (CGMP and IGMP are protocols that enable multicast packets to be forwarded only to devices on a specific multicast group).
If a packet is sent to a MAC address that the switch does not know about (which is a very rare case), it will be forwarded to all the ports of the switch.
Therefore, when you configure a port monitor to a specific port, you will see all the traffic coming in and out of it. If you connect your laptop to the network, without configuring anything, you will see only the traffic coming in and out of your laptop, along with broadcasts and multicasts from the network.
When capturing data, there are some tricky scenarios that you should be aware of.
One such scenario is monitoring a VLAN. When monitoring a VLAN, you should be aware of several important issues. The first issue is that even when you monitor a VLAN, the packet must physically be transferred through the switch you are connected to, in order to see it. If, for example, you monitor VLAN-10 that is configured across the network, and you are connected to your floor switch, you will not see the traffic that goes from other switches to the servers on the central switch.
This is because when building a network, the users are usually connected to floor switches in single or multiple locations in the floor, that are connected to the building central switch (or two redundant switches). For monitoring all traffic on a VLAN, you have to connect to a switch on which all traffic of the VLAN goes through, and this is usually the central switch.
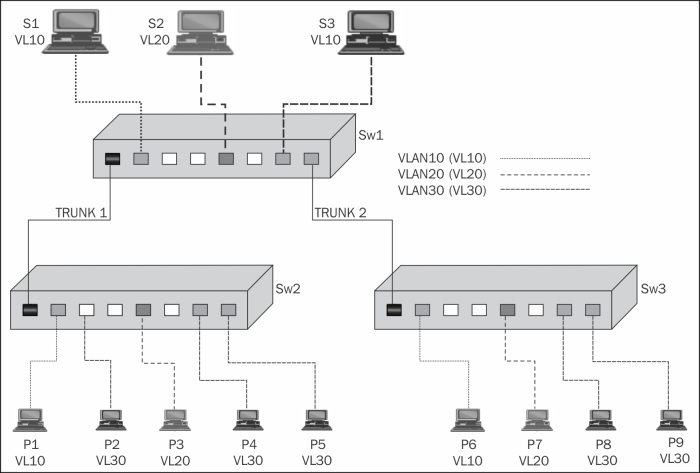
In the preceding diagram, if you connect Wireshark to Switch SW2, and configure a monitor to VLAN30, you will see all the packets coming in and out of P2, P4, and P5, inside or outside the switch. You will not see packets transferred between devices on SW3 and SW1, or packets between SW1 and SW3.
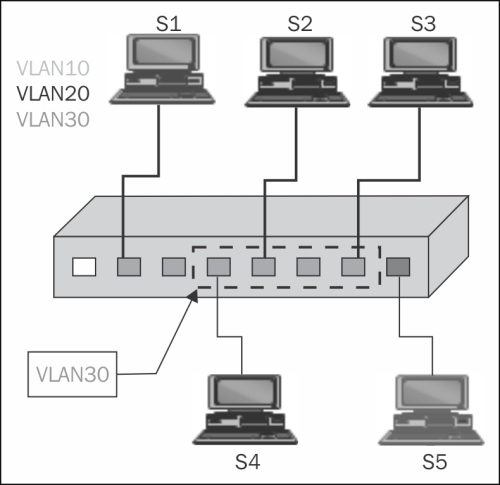
Another issue when monitoring a VLAN is that you might see duplicate packets. This is because when you monitor a VLAN, and packets are going in and out of the VLAN, you will see the same packet when it is comes in, and then when it goes out of the VLAN.
You can see the reason in the following illustration. When, for example, S4 sends a packet to S2, and you configure the port mirror to VLAN30, you will see the packet once when sent from S4 passing through the switch and entering the VLAN30, and then when leaving VLAN30 and coming to S2.
For information on how to configure the port mirror, refer to the vendor's instructions. It can be called port monitor, port mirror, or SPAN (Switched Port Analyzer from Cisco).
There are also advanced features such as remote monitoring (monitoring a port that is not directly connected to your switch), advanced filtering (such as filtering specific MAC addresses), and so on. There are also advanced switches that have capture and analysis capabilities on the switch itself. It is also possible to monitor virtual ports (for example, LAG or Ether channel groups). For all cases, refer to the vendor's specifications.



