Talking about Lync Server 2013, we are interested in applying a defense-in-depth approach, using multiple defense layers against security threats. Various security solutions are applied to make bypassing of one of the layers more difficult. We are also able (at least) to buy time on the different layers before someone is able to access the next level of security. Our servers are the last layer before internal data and files of Lync are compromised. Hardening a Lync Server requires a series of steps, and we will see how to use the Security Configuration Wizard (SCW), a tool that makes it easier to fix some common misconfigurations and security flaws.
To increase the security of the operating system, we can use the SCW (if we are using Windows 2012 or Windows 2012 R2 SCW it is an integrated tool). In the previously mentioned OS, the Configuration Wizard is part of the Tools menu.
Note
While the following steps have been tested on a single installation Front End (Lync Server 2013 Standard Edition), we have to select the settings that best fit our specific security requirements, and verify them in a lab. Using SCW on a production environment without sufficient verification is a risky approach.
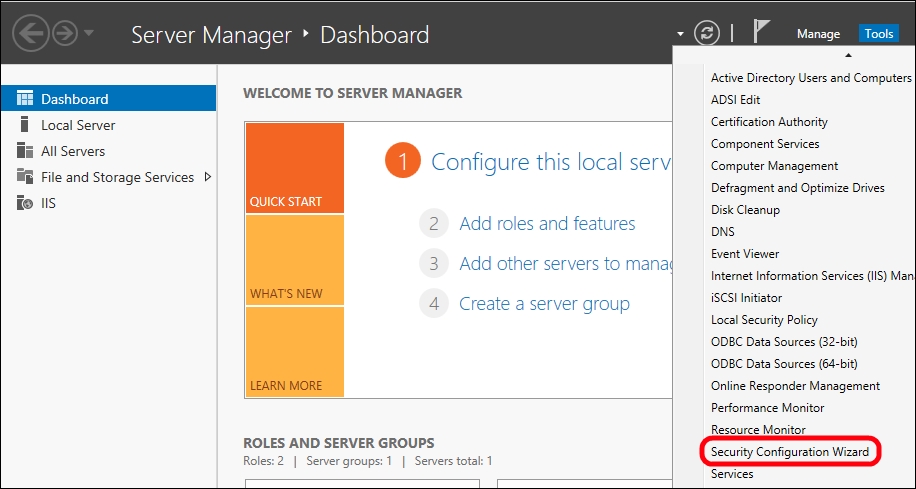
The Security Configuration Wizard option is accessible from the Tools menu in Server Manager, as we can see in the following screenshot:
In the first screen, we have to click on Next and then on Create a new security policy.
Select the name of the Lync Server that will act as a baseline (in our scenario, Madhatter).
We can select Next in the Role-Based Service configuration screen and again Next in the Select Server Roles screen until we arrive at Select client features. Flag all the options and select Next.
In the Select Administration and Other Options screen, select Background Intelligent Transfer Service BITs and Windows Audio.
In the Select Additional Services menu, flag all the services and click on Next.
Select Do not change the startup mode of the service and then select Next.
In the Confirm Service Change screen, accept the default value and select Next.
Flag the Skip this section in the Network Security screen (we have to leave the flag box clear if we want to use the Windows firewall too).
Click on Next in the Registry Settings screen (if we don't have a legacy operating system that needs to connect to the Lync Server).
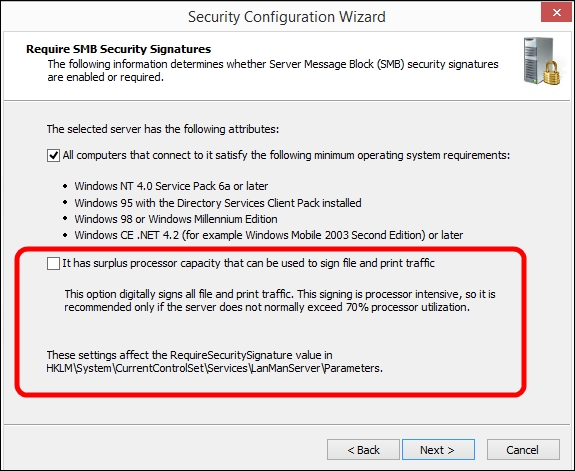
In the Require SMB Security Signatures screen, we can clear the second flag as shown in the following screenshot. If the server has enough unused processing resources, digital signature is a security option that we can consider:
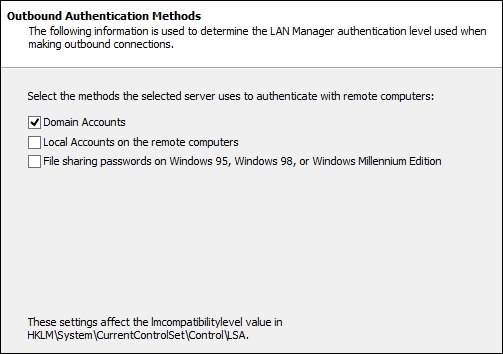
As we can see in the following screenshot, in the Outbound Authentication Methods screen, we can leave the default settings as is if we are not going to use local accounts to authenticate with other servers:
In the Outbound Authentication using Domain Accounts screen, we can leave the default settings as is and select Next with no changes also in Registry Settings Summary.
If we are not going to use auditing, we can select Skip this section in the Audit Policy screen, and then click on Next in the Save Security Policy screen.
Type a name for the policy (for example, LyncTemplate), optionally adding a description, and click on Next.
Select Apply Now, and then click on Next and Finish in the Completing the Security Configuration Wizard screen.
It is advisable to reboot the server in order to verify that the new settings have impacted the Lync Server startup phase.
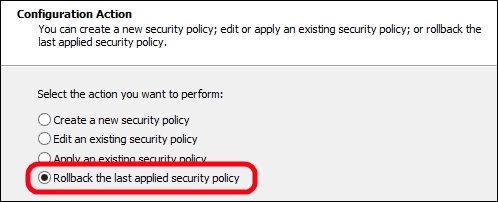
If any issue arises with the SCW, we are able to roll back to the previous configuration. If we don't have access to the local server, we can launch the SCW on another server and revert to the configuration remotely. The option is the one we can see in the following screenshot:
SCW can close TCP ports 8080 and 4443 on the Lync Front End. Running the Enable-CsComputer cmdlet, we are able to open again the required ports on the Windows Firewall. The same result can be obtained by using Lync Server Deployment Wizard or Bootstrapper.exe. For more details, see Re-activate server after Security Configuration Wizard closes ports in IIS (http://technet.microsoft.com/en-us/library/gg398851.aspx).
SCW can disable the RDP access. We are able to restore the feature with various solutions, for example, by selecting Remote Desktop from the Installed options list in the Select Administration and Other Options screen, as we can see in the following screenshot:

One of the obvious steps to enhance server security is the installation of an antivirus application. To avoid issues with Lync, we should follow the guidelines in this post Antivirus scanning exclusions for Lync Server 2013 post at http://technet.microsoft.com/en-us/library/dn440138.aspx.



