The Instant Messaging (IM) feature of Lync and the capability to communicate with external companies using Federation expose our Lync deployment to a series of threats and compliance issues. In many companies, it is required (for compliance or organizational motivation) that not all people inside all departments are able to use IM to talk to each other. Also, if our company uses federation, there is an increased risk of improper or unprofessional use of Lync features that involve external connections. Talking about IM, the first tool we have for the purpose of mitigating the previously mentioned risks is the Intelligent IM Filter that enables us to block files and URLs in IM conversations. We will see some examples to create additional controls on features.
To disable inline images (pictures added to IM conversations), we can use the two filters proposed by Graham Cropley (http://www.lyncexch.co.uk/love-lync-26th-sept-2013/).
To block
.jpgfiles, use the following:Set-CsFileTransferFilterConfiguration -Identity <Site / Global> -Extensions @{Add=".jpg"}To disable Rich Text Format, use the following:
Set-CsClientPolicy -Identity <policy> -DisableRTFIm $true
Before we go to the next step, it is useful to know a list of file extensions that are prohibited from our policies. The cmdlet to use is:
Get-CsFileTransferFilterConfiguration -Identity global | Select-Object –ExpandProperty Extensions
According to Chris Norman (http://voipnorm.blogspot.it/p/about.html), we have three filters that we can use to enhance the security for our Lync Edge Server (we can pair them with the steps in the Deploying a secure Lync Edge recipe). The following scripts could be used respectively to block URL style links, to block the transfer of files with common extensions, or to block the transfer of all files:
New-CsImFilterconfiguration -Identity EdgePoolIdentity -BlockFileExtension $True -Action Block -Enabled $True New-CsFileTransferFilterConfiguration -Identity EdgePoolIdentity -BlockFileExtension $True -Action Block -Enabled $True New-CsFileTransferFilterConfiguration -Identity EdgePoolIdentity -BlockFileExtension $True -Action BlockAll -Enabled $True
By default, Lync tries to establish what kind of relationships we have with a specific person, and grants different rights to that person. This is called Privacy Relationships, and it gives control to every single user to establish what kind of information they want to share with a specific contact, varying from a complete opening with Friends and Family to a total exclusion for Blocked Contacts. In the following screenshot, we are able to see the Change Privacy Relationship menu inside the Lync desktop client:
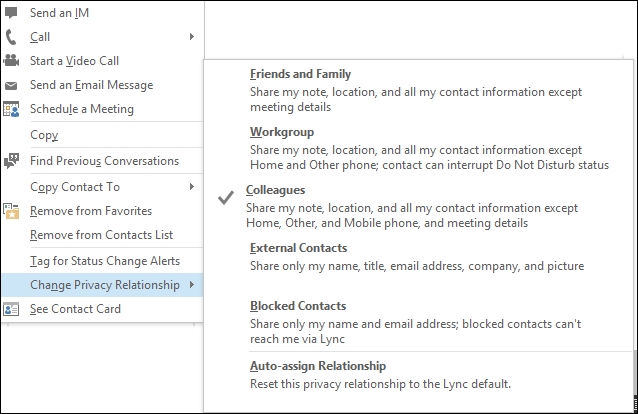
Tip
Downloading the example code
You can download the example code files from your account at http://www.packtpub.com for all the Packt Publishing books you have purchased. If you purchased this book elsewhere, you can visit http://www.packtpub.com/support and register to have the files e-mailed directly to you.
On the Microsoft Office pages (http://office.microsoft.com/en-us/communicator-help/control-access-to-your-presence-information-HA101850361.aspx), there is a handy table that shows the information available to contacts in the different privacy relationship groups. We can see a copy of it in the next screenshot:
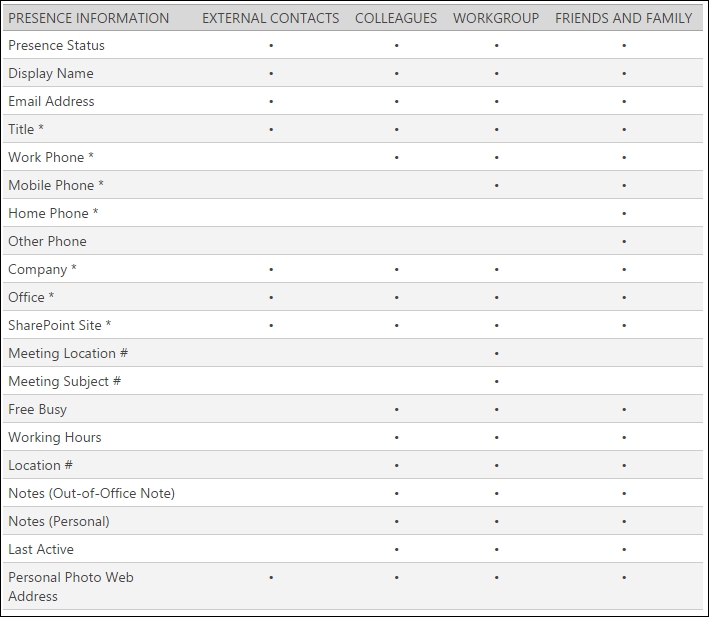
This kind of solution manages the problem at the user level and leaves out many scenarios. For example, if we need to apply more granular control (like issuing a warning to users that are typing sensitive data such as credit card numbers), we have no out-of-the-box tool. Segregating different groups of our users (or having a stricter control over companies that are going to federate with us) is also a problem. In the previously mentioned scenarios, what we need is a so-called ethical wall, usually adopting a solution developed by a third-party provider.



