adb is an essential tool for penetration testing Android apps. We will use this utility in multiple scenarios during our journey through this book. This tool comes preinstalled with the Android SDK and it is located in the "platform-tools" directory of the Android SDK. We added its path to the environment variables during the SDK installation process. Let us see some of the applications of this utility.
We can use adb to list the devices that are connected to the workstation using the following command:
adb devices
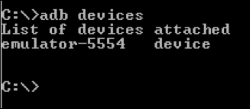
As we can see in the preceding screenshot, there is an emulator running on the laptop.
We can use adb to get a shell on the emulator or device using the following command:
adb shell
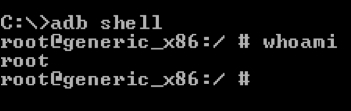
The preceding command will get a shell for the connected device.
The command to get a shell for an emulator when a real device and emulator are connected is as follows:
adb –e shell
The command to get a shell for a real device when a real device and emulator are connected is as follows:
adb –d shell
The command to get a shell for a specific target when multiple devices/emulators are connected is as follows:
adb –s [name of the device]
When you have access to a shell on an Android device using adb, you can interact with the device using tools available via the shell. "Listing the installed packages" is one such example that uses pm, which stands for package manager.
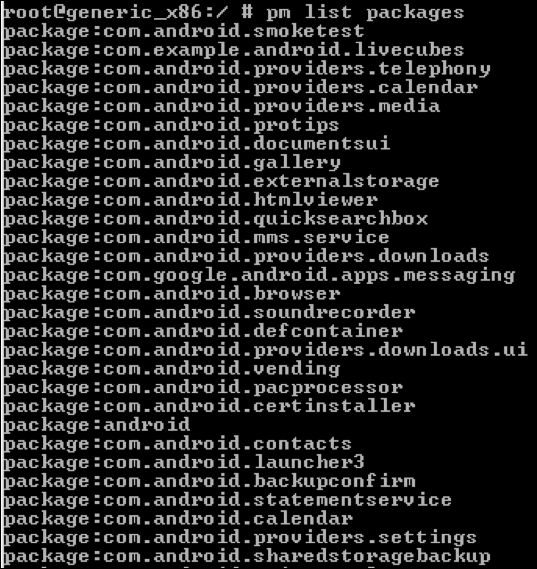
We can use the following command to list all the packages installed on the device:
pm list packages
We can push data from the workstation to the device using the following syntax:
adb push [file on the local machine] [location on the device]
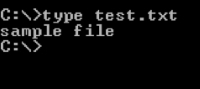
Let's see this in action. At the moment, I have a file called test.txt in my current directory:
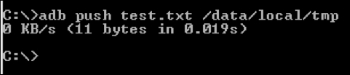
Let's move the test.txt file to the emulator. Type in the following command:
adb push test.txt /data/local/tmp
We can also use adb to pull files/data from the device to our workstation using the following syntax:
adb pull [file on the device]
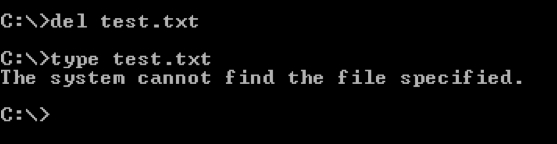
Let us first delete the test.txt file from the current directory:
Now, type in the following command to pull the file located at /data/local/tmp directory to the device:
adb pull /data/local/tmp/test.txt
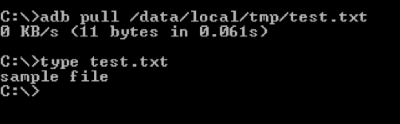
As we have seen in one of the previous sections of this chapter, we can also install apps using the following syntax:
adb install [filename.apk]
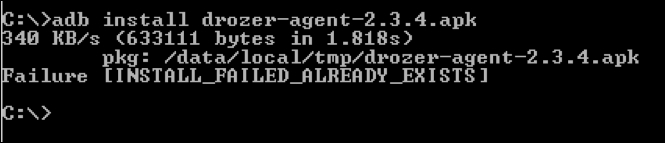
Let's install the Drozer agent app using the following command:
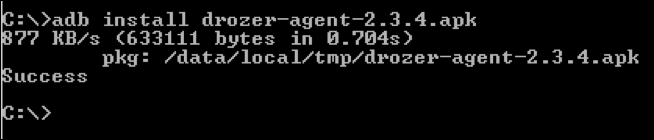
As we can see, we have successfully installed this app.
Note
Note: If we install an app that is already installed on the target device/emulator, adb throws a failure error as shown following. The existing app has to be deleted before we proceed to install the app again.