With wireless now supported with the inclusion of an IEEE 802.11n transceiver, we can now take advantage of the inherent support Kali offers for this. Many commercial tools, such as the Pineapple from HACK5®, take advantage of wireless hacks and we will see how many are possible with the Raspberry Pi 3 later in this book. Because Kali Linux supports it out of the box, we should be able to see that it's available without any effort on our part and can check settings and detection using the iwconfig command:
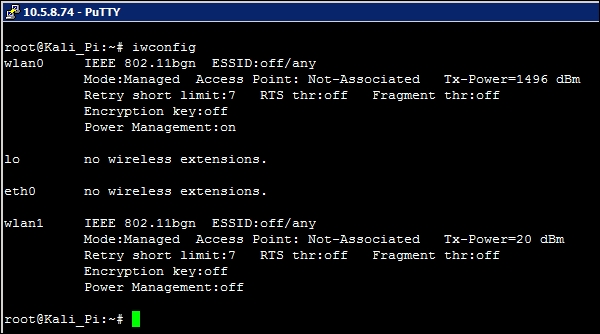
We did not pre-configure anything here. If we wanted to use this as our primary interface for connectivity, we could configure it with all of the default information we'd need to attach to and use a network, or if using the Xfce desktop (logged in locally or via RDP or VNC) we could use the Network Management tool to select a wireless network to attach to.
As we are penetration testing and wireless is a very likely means by which to exploit the target...



