In this recipe, we will learn about how to use rainbow tables with Kali. Rainbow tables are special dictionary tables that use hash values instead of standard dictionary passwords to achieve the attack. For our demonstration purposes, we will use RainbowCrack to generate our rainbow tables.
Open a terminal window and change directories to the directory of
rtgen:cd /usr/share/rainbowcrack/
Next we are going to run
rtgento generate an MD5-based rainbow table:./rtgen md5 loweralpha-numeric 1 5 0 3800 33554432 0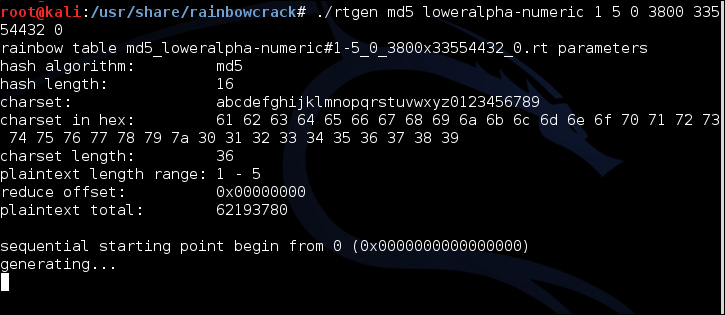
Once your tables have been generated—a process that depends on the number of processors being used to generate the hashes (2-7 hours)—your directory will contain
*.rtfiles.To begin the process of cracking the passwords, we will use the
rtsortprogram to sort the rainbow tables to make it an easy process.



