Installing Kali Linux on Docker
I think a little about is justified here. Docker is a new open source container technology, released in March 2013 that automates the deployment of applications inside self-sufficient software containers. Docker (built on top of Linux containers) provides a much simpler way of managing multiple containers on a single machine. Think of it as a virtual machine but it is more lightweight and efficient.
The beauty of this is that you can install Kali Linux on almost any system, which can run Docker. Let's say, for example, you want to run Kali on Digital Ocean droplet but it does not let you spin-off a Kali Linux directly like it does for Ubuntu. But now, you can simply spin-off Ubuntu or centos on digital ocean and install Docker on it and pull the Kali Linux Docker image and you are good to go.
Since Docker provides another layer of abstraction, it is beneficial from security standpoint as well. Let's say, if you are running an apache server that is hosting an application, you can simply create a Docker container for this and run it. Even if your application gets compromised, the attacker would be self-contained within the Docker image only and will not be able to harm your host operating system.
Having said all that, now with installing Docker on your machine, for the purpose of demonstration we will be installing Docker on a Mac operating system.
For this recipe, you will need the following things:
- Connection to the Internet
- An installed Virtualbox
Perform the following steps for this recipe:
- To install Docker on Mac operating system, you need to download and install toolbox from
https://www.docker.com/docker-toolbox
. On running this installer on your mac, you will setup the Docker environment; the toolbox will install Docker Client, Machine, Compose (Mac only), Kitematic and VirtualBox.
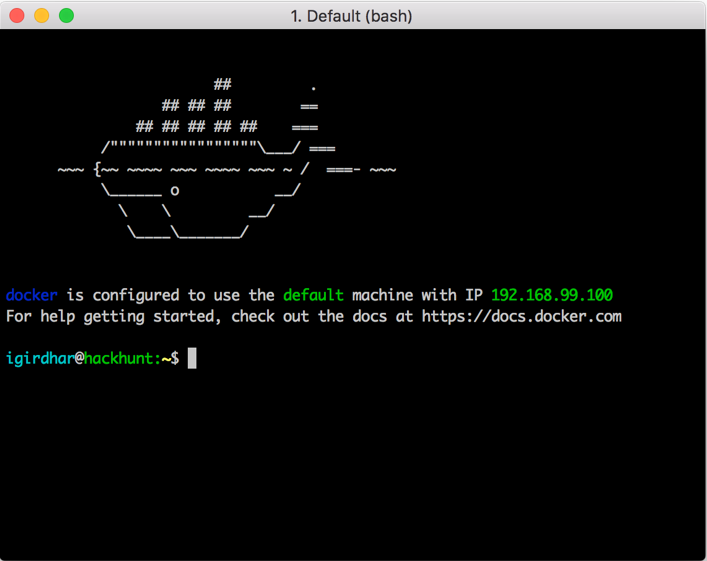
- Once the installation is done, go to
Applications | Docker | Docker Quickstart Terminal.app or open the Launchpad and click on Docker Quickstart, When you double-click on the application, you will see the terminal as shown in the following screenshot:
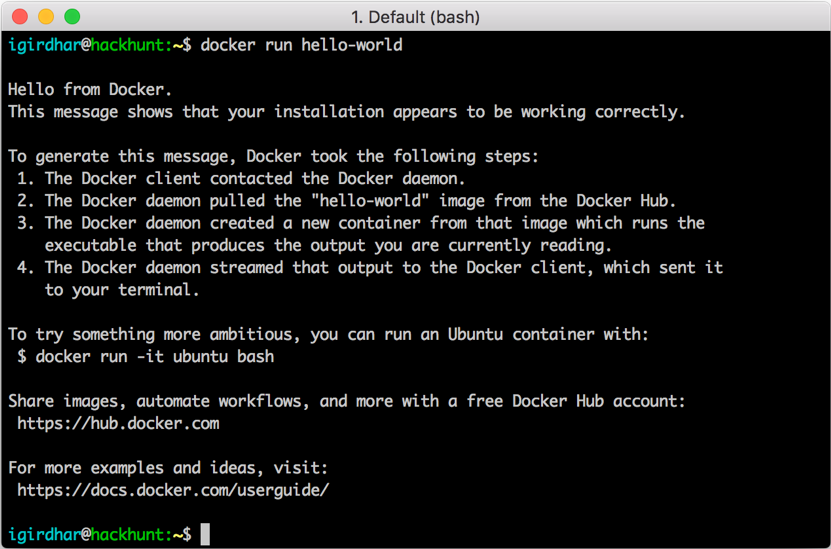
- To check your has succeeded, you can run the following command:
docker run hello-world
You will see the following output if your installation succeeded:
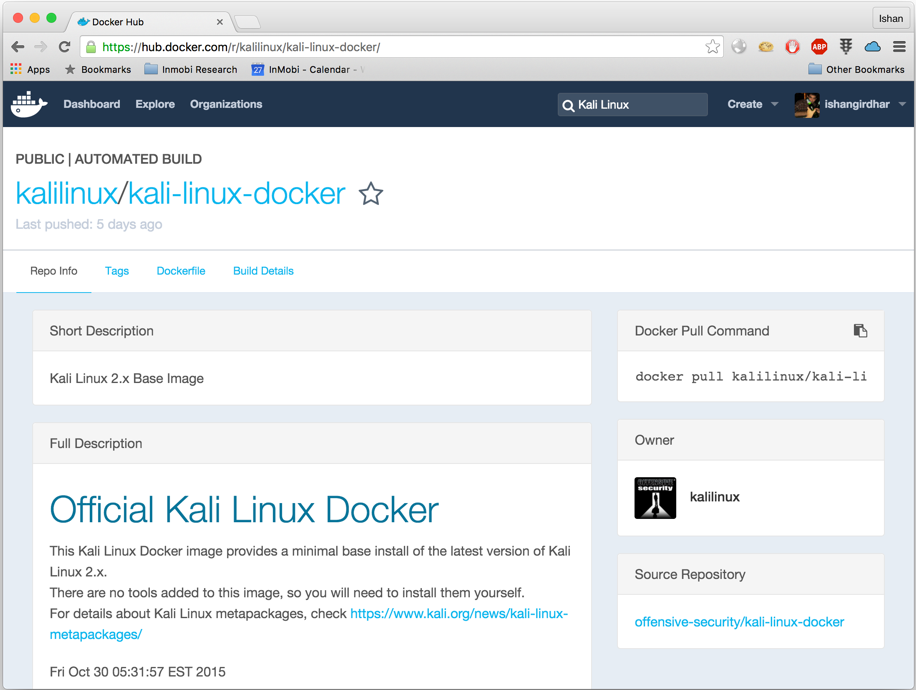
- As you can see, the official Kali image is available; we will use the following command to pull and run it in our Docker:
docker pull kalilinux/kali-linux-docker
docker run -t -i kalilinux/kali-linux-docker
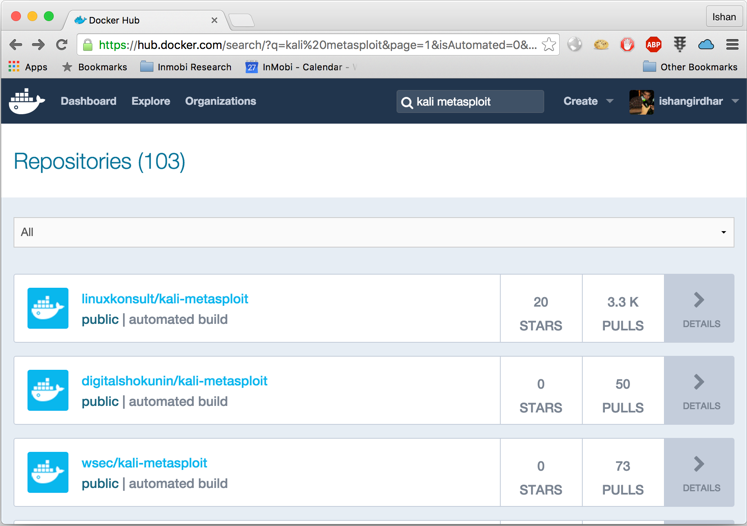
- Let's say, you just want to only Metasploit; for that you can search for
kali Metasploit image on the hub and install the one with the highest number of pulls so far, as shown in the screenshot:
- Pull the image using the following command; but before you do that, note that this is not an official image. Therefore, it is at your discretion whether you want to trust this image:
docker pull linuxkonsult/kali-metasploit
- Then, run the Docker image with the
docker run command as shown:
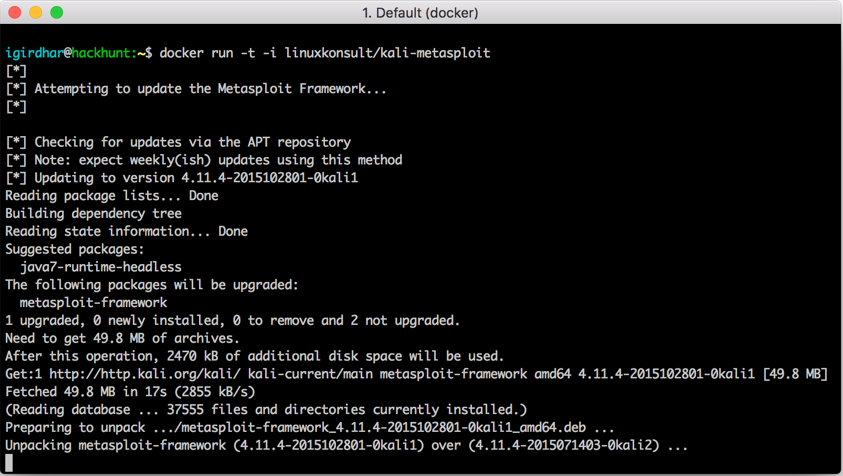
docker run -t -i linuxkonsult/kali-metasploit
The will be as shown in the screenshot:
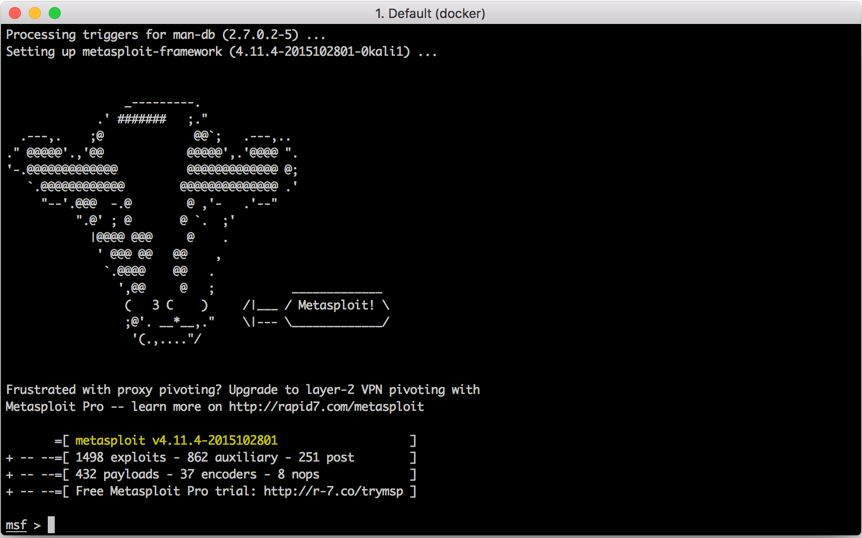
Once the framework is prepared it is unpacked and executed, it should look as follows:
As you can see, you have Metasploit updated and running. But this is not it; all the changes you have made are not permanent, until you commit the changes. Once you commit the changes, you can pick up next time from where you left off. To commit the changes, open another console window and type the command:
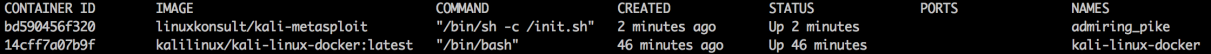
docker ps
- On running this command, you will see the output, as shown in the following screenshot:
- To commit the changes, you need to enter the command in the following format:
docker commit <docker-id> <docker-name>
docker commit bd590456f320 admiring_pike
On successful commit, you will see the following output:
b4a7745de59f9e106029c49a508c2f55b36be0e9487dbd32f6b5c58b24fcb57
In this recipe, we need Virtualbox already installed as a prerequisite, and we downloaded and installed the Docker toolbox. Once Docker toolbox is installed, simply open the Docker Quickstart Terminal.app and pull the image you want to run, you can search for the desired image from
https://hub.docker.com
and use the docker run command to run it. Once you have performed your operations, simply commit the changes with the docker commit command.
Here, we have used the -i and -t switches. For interactive processes (such as a shell), you must use -i
-t together in order to a teletype (TTY) for the container process. The-i
-t switches is often written -it.



 Free Chapter
Free Chapter