Let's revisit our example scenario. You have just signed up for the service GoodApp, and now GoodApp would like to suggest contacts for you to add by looking at your Facebook friends. In the last chapter, we looked at the old model, where GoodApp would ask you for your username and password and use them to access your Facebook friend list on your behalf. We then looked at the new, superior model that uses OAuth 2.0 to achieve the same thing, but in a much more secure and manageable way.
The (simplified) workflow looks like this:
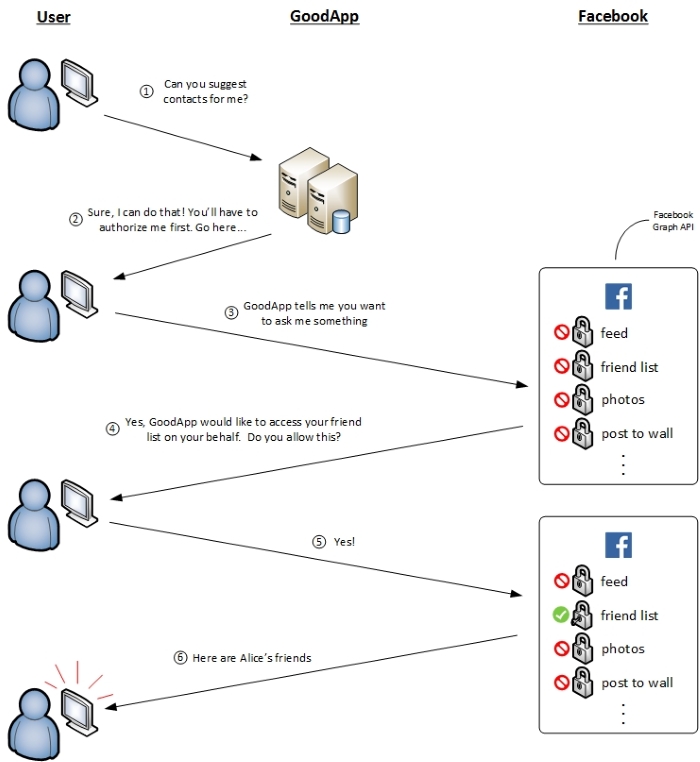
Here are the steps:
You ask GoodApp to suggest you contacts.
GoodApp says, "Sure! But you'll have to authorize me first. Go here…"
GoodApp sends you to Facebook to log in and authorize GoodApp.
Facebook asks you directly for authorization to see if GoodApp can access your friend list on your behalf.
You say "yes".
Facebook happily obliges, giving GoodApp your friend list. GoodApp then uses this information to tailor suggested contacts for you.
The image...



