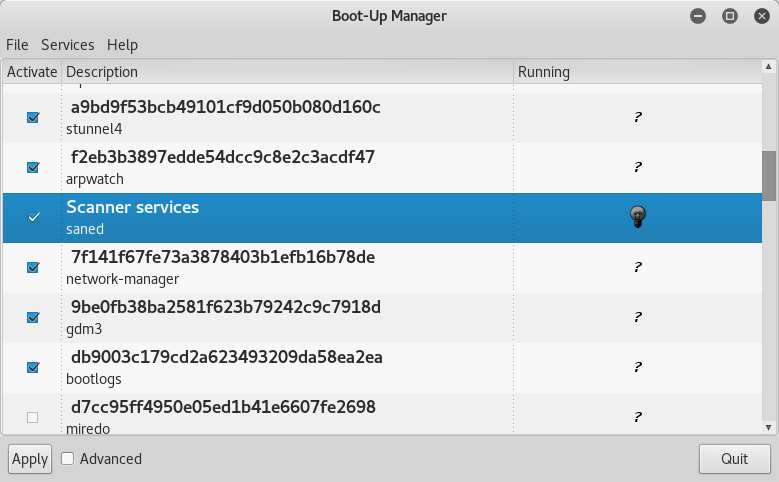
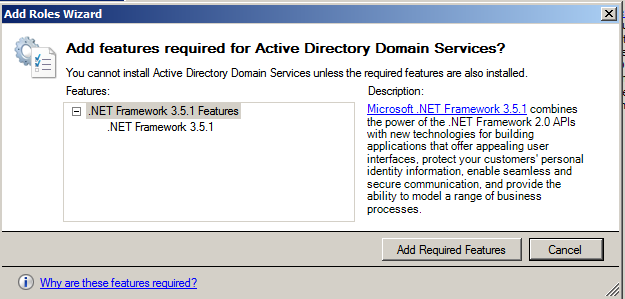
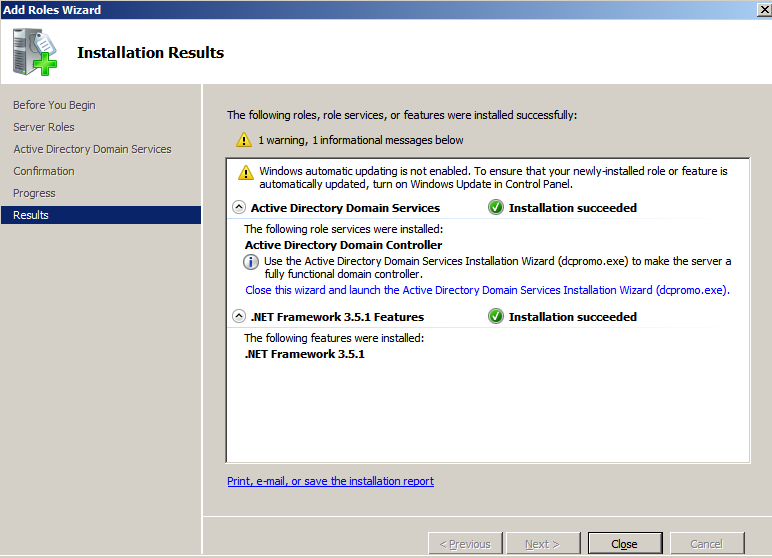
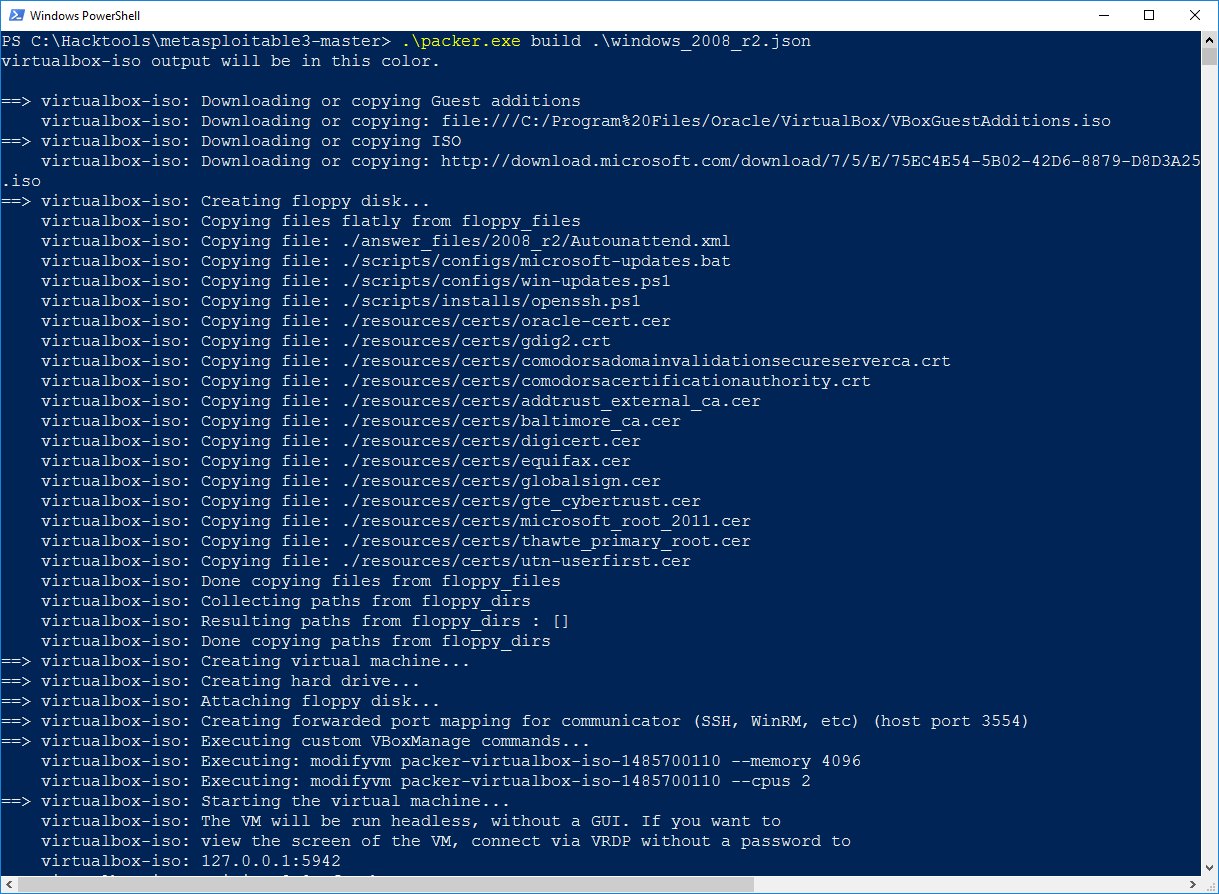
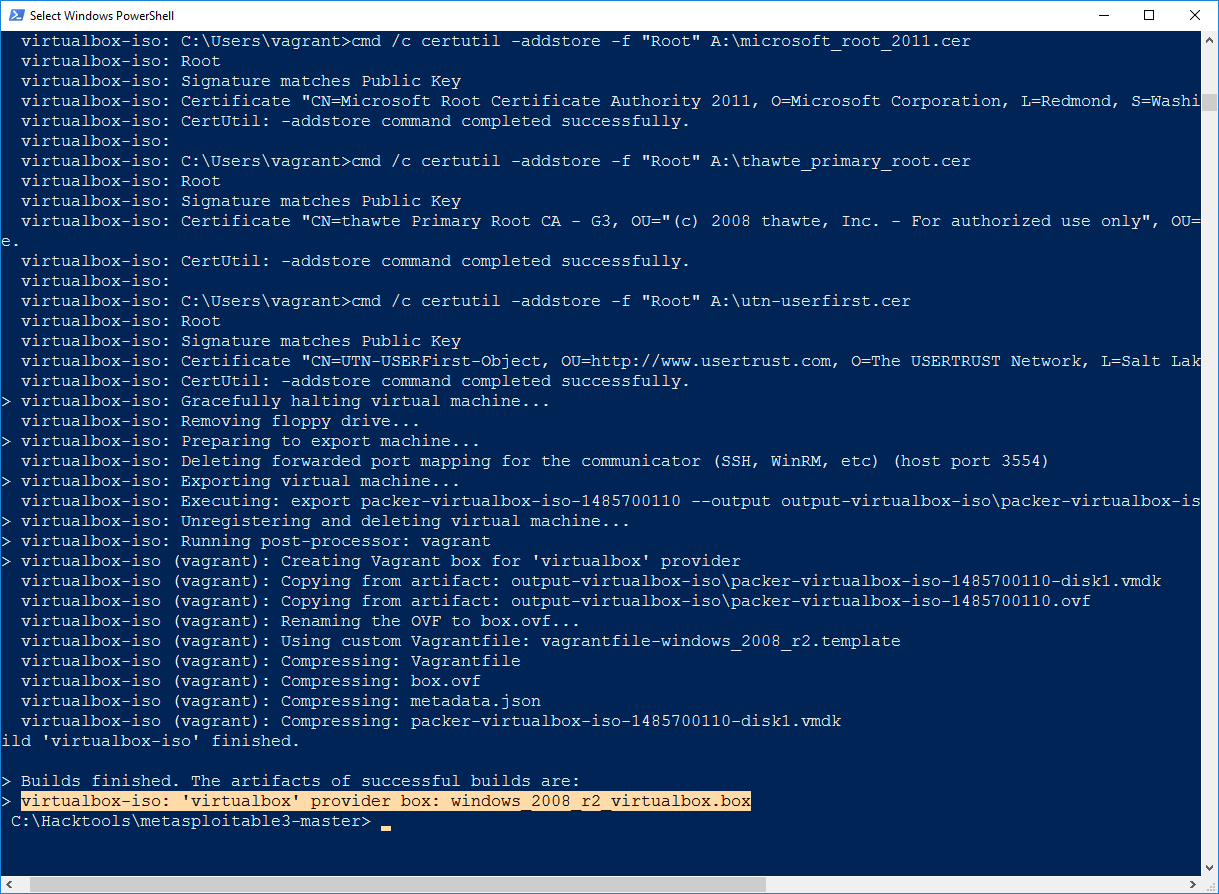
One of the most difficult aspects of penetration testing is remembering to test all of the relevant parts of the network or system target, or trying to remember whether the target was actually tested. In some cases, a single client may have multiple penetration testers performing scanning activities from multiple locations and management would like to have a single view. Faraday can provide a single view, assuming all the penetration testers are able to ping each other on the same network, or on the internet for external assessment.
Faraday is a multiuser penetration test Integrated Development Environment (IDE). It is designed for testers to distribute, index, and analyze all the data that is generated during the process of a penetration testing or technical security audit to provide different views such as management, executive summary, and an overall issues list.
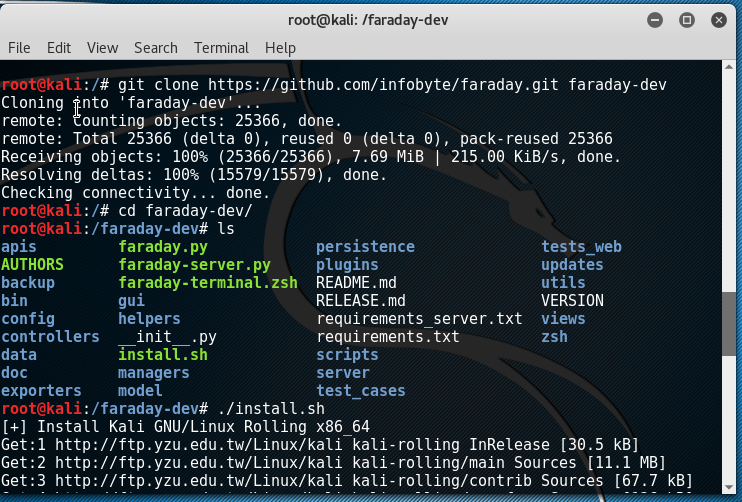
This IDE platform is developed in Python by InfoByte. Download the application from https://github.com/infobyte/faraday/wiki or directly git clone the link, as shown in the following screenshot:
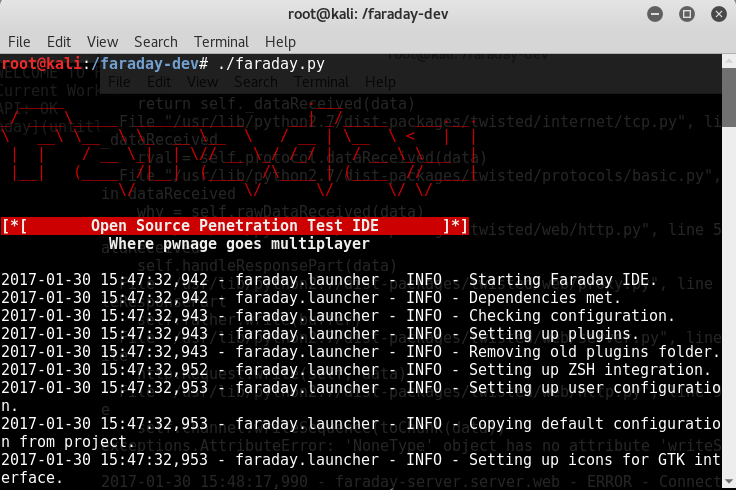
Once the folder is cloned to your Kali, run ./install.sh to install any dependencies. Do not forget to start the CouchDB service, as Faraday utilizes CouchDB as its database for storage. Finally, we run faraday-server.py to launch the Faraday server for an integrated platform, and then as the client, we should be able to launch Faraday by running faraday.py, as shown in the following screenshot:
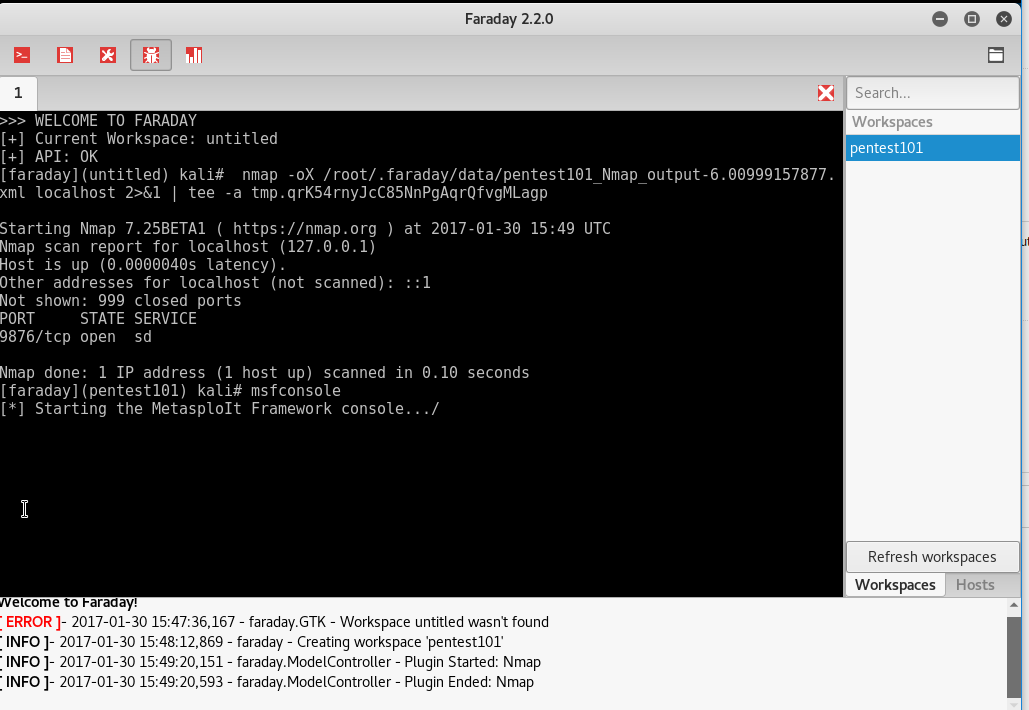
Launching Faraday should open up the Faraday shell console to us, as shown in the following screenshot:
One positive aspect of the application is that you will be able to visualize the information from any scanning that you do, or that any other penetration tester does, by clicking on Faraday web, as shown in the following screenshot:
There is a limitation on the free version of Faraday for the community, which can be utilized to visualize all the lists of issues in a single place.