The aim of cybersecurity is to ensure that the confidentiality, integrity, and availability of data and systems is preserved. This section discusses the different objectives of cybersecurity.
Cybersecurity objectives
Importance of cybersecurity and its impacts on the global economy
Cybersecurity has of vital importance today ever since the world was networked. Many processes in organizations are enabled by interlinked technologies. However, the penetration of technology into normal lives and organizational processes has introduced people to cyber threats. With every improvement in technology, the threat of cyber attacks increases. New technology, such as IoT, have met the harsh reality of cybercrime. However, current cybersecurity efforts ensure that the use of technology is not hindered by cyber criminals. There are several reasons why organizations and individuals are emphasizing cybersecurity; they are outlined here.
The number of cyber attacks is growing
With the rapid development of technology, the number of cyber attacks has been growing exponentially. Cybersecurity reports show that, each year, there is a rise in the number of threats that have been detected for the first time. There are specialists in underground markets that have focused on creating new types of malware that they sell to hackers. Cyber criminals are spending long hours doing background research on individuals and organizations to find weaknesses that they can target. Social engineers are perfecting their manipulation tactics to help them net more victims. At the same time, users have not significantly improved or taken individual responsibility for their own security or that of the companies they work for. The only hope in securing individuals' data, money, and systems lies in enhancing cybersecurity. With all the developments on the part of cyber criminals, cybersecurity is fast becoming a necessity.
Cyber attacks are getting worse
Cybercrime has evolved from what it used to be. The aftermath of a cyber attack today is often devastating, as can be seen from the companies that have fallen prey to cyber criminals. Yahoo lost its value after it was confirmed that cyber criminals had penetrated its systems and stolen the data of 3,000,000,000 users. Ubiquiti Networks lost over $40,000,000 to cyber criminals that executed a social-engineering attack on its employees. Many other top companies have lost sensitive data to hackers. Individuals are not spared either. The WannaCry ransomware indiscriminately encrypted individuals' and organization' computers in over 150 countries. In general, cybercrime is getting worse. More money is involved, and huge chunks of sensitive data are being stolen. The targets are not limited to small organizations, since big companies, such as Uber and Yahoo, have already fallen victim. Cybersecurity is therefore essential for organizations and individuals.
Impacts on the global economy
The economic implications of cyber attacks are being felt on a global scale. Organizations are losing billions of dollars to attacks every year. Forbes has estimated that with the current pattern, cybercrime will cost the globe $2,000,000,000,000,000,000 in 2019. In 2015, this number was only at $400,000,000. Prior to the estimate from 2015, early estimates done in 2013 reported that cybercrime only costs $100,000,000 globally. As can be seen, the pattern has been such that the cost keeps growing. The World Economic Forum has taken note of this, and with concern. It has warned that the figures could be higher since a large percentage of cybercrime goes undetected. It has identified industrial espionage as one crime where many victims don't even know that they're victims.
Estimation of financial losses related to cybercrime
The financial losses related to cybercrime are incomparable to the cost of cybersecurity. While cybersecurity costs remain almost constant, cybercrime costs increase every year. In 2017, it was estimated that annual breaches had increased by 27.4%.
Accenture has estimated the cost of cybersecurity for the year 2017, as follows:
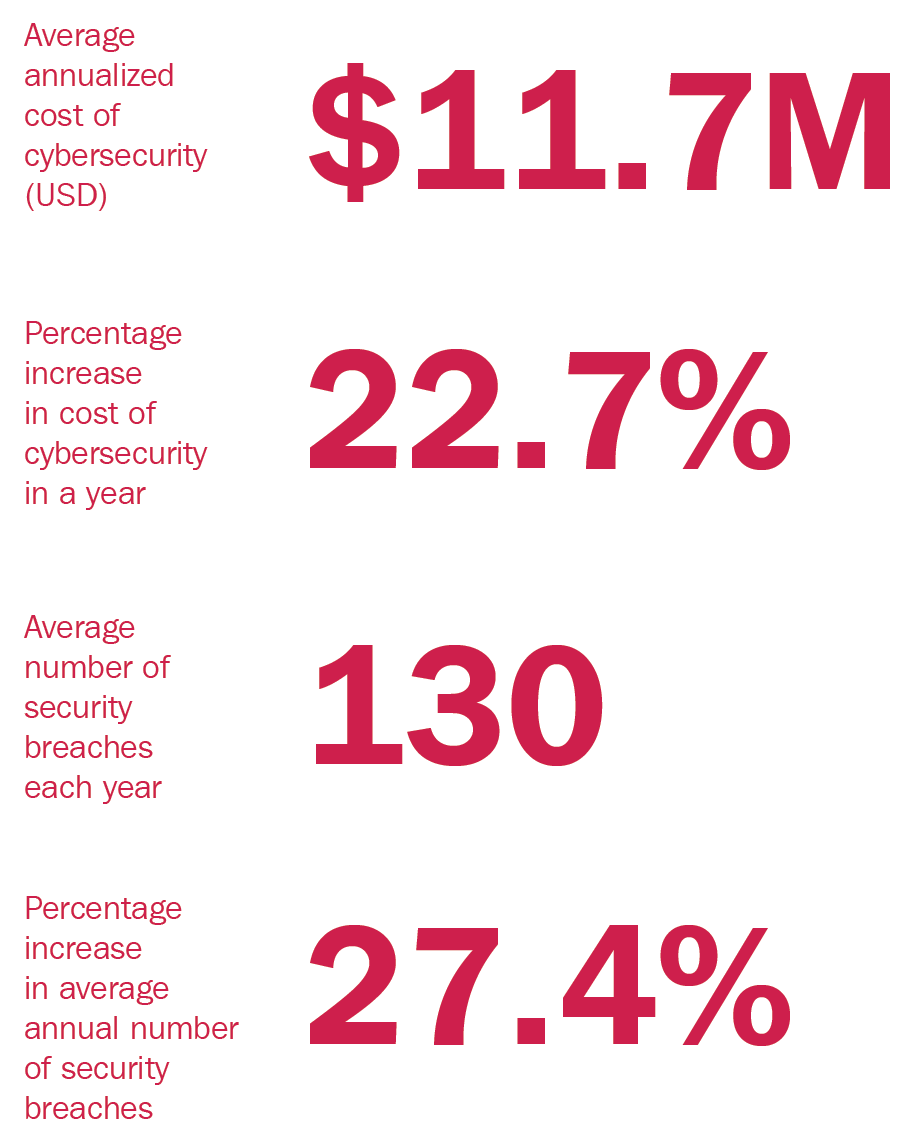
These numbers are more than just a statistic. It shows that more organizations will fall victim to cybercrime in 2018 than in 2017. The average cost of a breach or malware attack on an organization is currently at $2,400,000. However, this number is just an average. There are organizations that lose much more than that. Take, for instance, the Sony attack that happened in 2015: the organization lost a whopping $15,000,000 due to the attack; the Ubiquiti Networks case led to a $40,000,000 loss. Therefore, the average cost of a cyber crime should not be used to depict the reality, since some companies lose several times the average.
The time it takes to resolve a cyber attack is becoming longer than ever. It now takes an average of 23 days to recover from a ransomware attack. Insider threat attacks take up to 50 days to recover from. DDoS attacks take only a few days to recover from, but by then a lot of damage will have been done. In general, the attack duration has increased and that adds to the effects on the victims. The financial consequences can only go higher with more exposure time to an attacker.
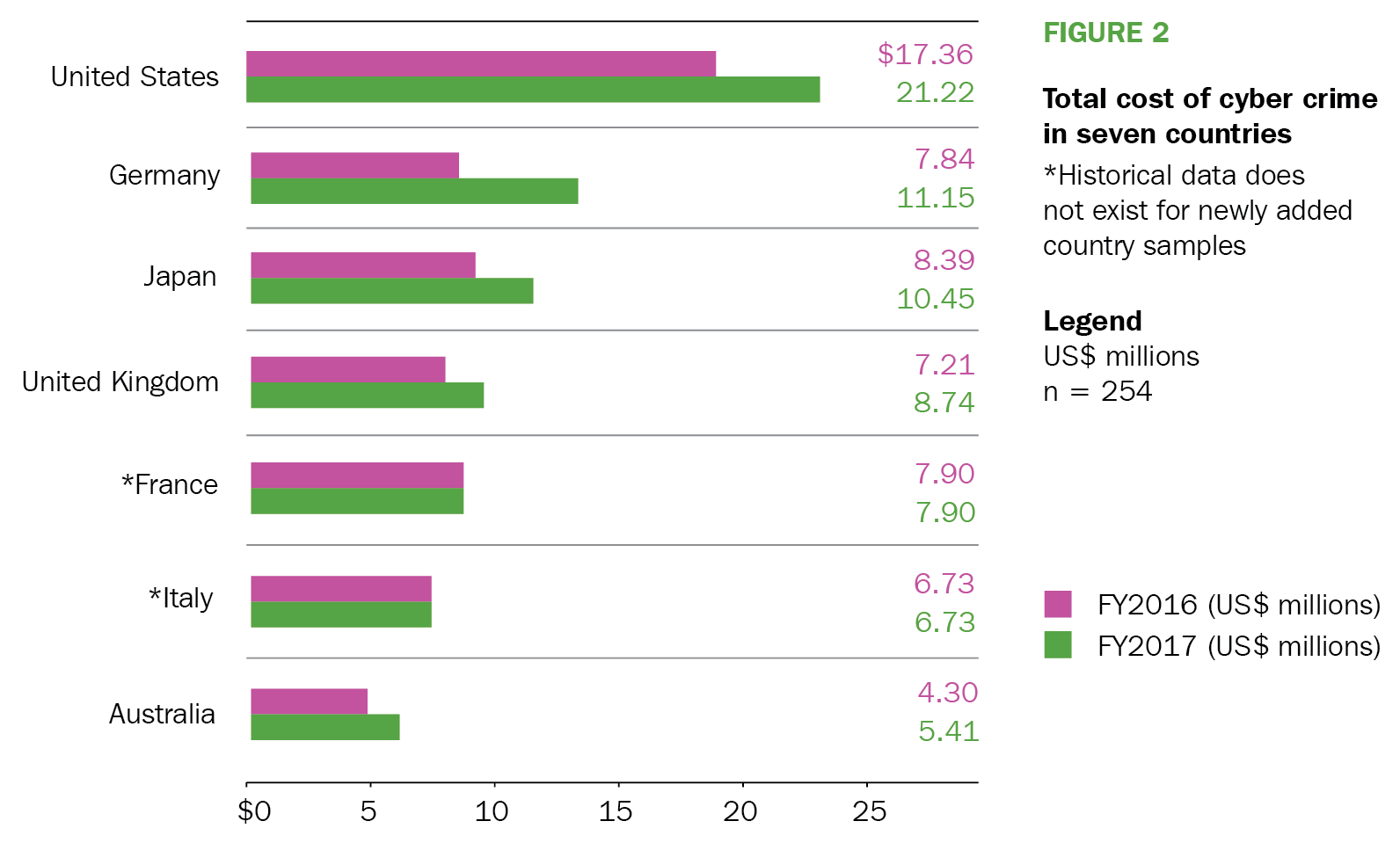
Globally, the US has witnessed the highest average cost of cyber attacks. The country's average has been higher than the global average since 2017, when it was estimated at $21,000,000. This estimate has grown from $17,000,000 in 2016. The second country in the ranking of those with the highest cost of cybercrime is Germany; it jumped from $7,800,000 in 2016 to $11,500,000 in 2017. Japan is third, with an estimated cybercrime cost of $10,000,000. The UK, France, and Italy follow with estimates of $8,000,000, $7,900,000, and $6,300,000, respectively.
The following screenshot estimates cybersecurity costs by Accenture:
There are also other financial losses that arise from cybercrime that cannot be directly estimated. The loss of customer loyalty is a hidden impact that can have financial consequences. Fewer customers directly translates to lower revenue. Lost reputation is another impact that leads to financial loss. Without a good reputation, very few clients will choose to do business with a company that's perceived to be unsecured. Legal fees from cases relating to loss of user data also add to the financial consequences of hacks that a company has to meet. These fees, therefore, make cybercrime very costly to organizations.
Finance and cybersecurity
There is a strong relationship between finance and cybersecurity. Finance can be viewed in two perspectives in line with cybersecurity. Finance is used to procure cybersecurity products that can be used to prevent cybercrime. Finance is also a direct victim of cyber attacks. Therefore, it continues to be linked to cybersecurity. There have been attacks targeted specifically at the finance departments in organizations. Other than this, Chief Finance Officers (CFOs) are having to work closely with Chief Information Security Officers (CISOs) in organizations to ensure that they adequately fund their cybersecurity endeavors. Today, the links between finance and IT are closer than ever.
Critical dependency of business, processes, and IT infrastructure
Today, business is run through computer systems that coordinate processes from different business lines, while making the individual processes more efficient and effective. For instance, in a production company, the supplies department has to be linked with the production department, which then has to be linked with the sales department. This type of chain will ensure that the supply department has already procured input before the production department depletes the ones it has. The production department will control its output depending on the sales such that there is no over-production. To ensure that these three departments continue to operate smoothly, the organization might acquire enterprise resource planning (ERP) systems that will be integrated. The ERPs will ensure that the supplies department automatically gets notified when the production department needs more input. The production department will get actual and forecasted sales to ensure that it doesn't overproduce products that may go to waste. The ERP solution will be the backbone of all this coordination between departments.
This hypothetical example is just a snapshot of what takes place in actual organizations. Different departments are linked using IT systems. When these systems are down, business processes in different business lines will be affected. Therefore, it's in the best interest of all organizations to ensure that IT systems are running as expected at all times. Another critical linkage between departments is the internal network. Organizations that have branches in different places normally want to ensure that data stored in different physical locations can easily be accessed. Therefore, a WAN is established to keep all branches connected. If this network goes down, many operations can't take place. There are other components of the IT infrastructure in an organization that are equally important for the functioning of day-to-day operations. If these components go offline, operations can't go on as usual. This is the current state in most organizations. To survive in the current business environment, it has become necessary to make IT a resource. There are some industries where competitiveness is only judged by the systems that an organization has.
With a good view of the current dependence of businesses on IT infrastructures, one can appreciate the consequences of having components of the infrastructure failing or being attacked. Without some critical components, such as ERP systems, networks, and computers, business operations can come to a halt. One of the main reasons IT systems go down is cyber attacks. There are other causes, such as natural disasters, human error, and normal failures. However, of major concern today is attackers targeting the IT infrastructure. Not only can they stop operations, attackers can purposefully destroy the infrastructure. This will in turn cripple the organization. Therefore, organizations resort to protecting their IT infrastructures, since they cannot afford to lose some of the functionalities that are supported by the different components of the infrastructure.
Economic loss
As a consequence of the increasing cost of cybercrime, there has been a resultant loss in global and local economies. Based on estimates from McAfee, it is expected that 2018 will see 0.8% of the global economy gross domestic product being lost to cybercrime. This is estimated at $600,000,000,000. Estimates for 2019 show that the economic loss will hit the trillion-dollar mark. This shows that the economic impact of cybercrime is only getting worse. In 2014, the estimated loss was at 0.7% of the global economy. The US has seen a relatively constant increase in the number of cybercrimes reported. Europe, however, has seen the highest rise in cybercrime. It might appear that cyber criminals were once not particularly focused outside the US market. With time, there has been an influx of hacking activity, and the hacks have sporadically grown in the previously-unexplored Europe region. Also, since the US has seen consistent cybercrime, organizations have been preparing themselves for the attacks. Europe is now facing the highest economic loss to cybercrime. An estimated 0.84% of its regional gross domestic product has been lost to cybercrime. In the US, the percentage is at 0.78%.
There are several reasons why the economic loss due to cybercrime seems to be going up. To begin with, there are more cybercrime tools being released. The new cybercrime tools are more effective. As was explained in the Hacking groups section, the most damaging ransomware attack thus far was successful due to the use of a three-month-old exploit that had been stolen from the NSA by a hacking group. Another reason for the increase of economic losses is because of the adoption of new technologies by threat actors. These technologies enable them to decrypt encrypted files, gain access to systems without causing alarms to be raised, and overwhelm security tools, among other things. Another driver for the increased economic loss is the growing sophistication of hacks. A good example is phishing. Phishing has evolved over time. Years ago, it was done through plaintext email, which narrated an unfortunate occurrence and asked the recipient to offer some assistance to the person in peril. Early phishing emails were characterized by grammatical errors and an outright feeling of vagueness. However, phishing has recently developed a new face. It's done through professionally-formatted HTML emails that resemble those of legitimate companies. Phishing emails contain links to cloned websites that have a similar look, feel, and interactive quality to legitimate websites. The targets don't know when they're handing over their information to hackers or sending money to them. This type of revolutionary development in attack techniques has also been witnessed in other types of attacks. This has led to a high number of successful attack. For example, the number of victims of the IRS scam of 2017 was around 170,000. This is a number that didn't exist five years ago since these types of phishing attacks hadn't been used.
Banking and financial systems – changes from a risk and security perspective
Banking and financial systems have been the targets of cyber criminals. There are listings on some underground economies of malware that can be used against automated teller machines to cause them to spit out cash. There are malware that can be used to intercept the communication between bank servers and customers to steal sessions or login information. There are malware that have been developed to spy on users once they visit certain banking websites. There are phishing scams that have been specifically targeted at customers of certain online banks and payment systems. These are just a few of the threats that are facing banks and have caused them to innovate their risk and security perspectives. The following is a screenshot of a PayPal phishing email:

Banks have had to upgrade their machines and operating systems used to control their ATMs to prevent malware attacks that can cause money to be stolen. They recognize that there are hackers conversant with the systems used by ATMs, who can easily break into these systems and steal money directly from the machines. Banks have also come to recognize that there are threats with the transmission of data on the internet in plaintext form. Therefore, they have switched to secured HTTP to ensure that data is encrypted from the source to the destination. Therefore, a user's input for logging in cannot be stolen while in transit. This is a risk that they didn't have to contend with in the past, but now are forced to. Antivirus companies are creating browser add-ons that can be integrated with common browsers to detect and remove spyware, or to prevent any spying activities from taking place during data entry into websites. Previously, spyware was not a risk but today security companies have to respond to it. As for the phishing scams, banks have been spreading user awareness to prevent users from falling for scams. There has been a PayPal scam doing the rounds, with emails and websites that are similar to the legitimate PayPal sites and they have caused many users to lose money. Years ago, these scams didn't exist, but today banks have to pay attention to them so as to keep their users secure. In short, there are many changes taking place in banking and financial systems to account for new risks and security threats that didn't exist or weren't as serious in the past.
Data breach means money
When an organization is breached, data is stolen, and then it is leaked, the end result is the exchange of money. Therefore, data leakage almost always translates to money. The beneficiary of a data leak is the hacker. The hacker has everything to gain from the leaked data. The hacker could hold the stolen data ransom and ask the victim to pay so that the data isn't released or sold in underground markets. This has happened several times. A Dubai bank was once threatened by a hacker that they would release bank records that had been hacked from the bank's website. The bank defied the orders to send a ransom amount to the hacker, and the end result was that sensitive information was released on Twitter by the hacker. Another way that a hacker can make money out of a data breach is by selling it to third parties. When Yahoo was hacked and data belonging to 3,000,000,000 users stolen, it was listed for sale in dark markets. Black markets on the darknet are almost always the place where stolen data is sold. There are willing buyers for stolen data even if it's encrypted. The buyers tend to either be advertisers or other cyber criminals. Advertisers will use the stolen data to create profiles of people that they can advertise to some products. Cyber criminals will, on the other hand, try to user details, such as login credentials, to hack the user whose data has been stolen.
The other cashflow in a data breach relates to the loss of money from the victim organization. When a data breach occurs, and either user data or personally identifiable information is lost, the victim organization can be sued by the users. It is the responsibility of the organization that collects user data to ensure that this data is secured at all times from theft. There have been cases where users have dragged some companies to court after a data breach. Courts often side with users as they are the most aggrieved parties when personal data has been stolen. Financial loss also occurs to the victim organization due to the loss of credibility, reliability, and trust that customers had in it.



