Using Zscaler Private Access for secure application access
Employees of the enterprise primarily work on the company applications that generate revenue, support customers, and grow the company business. These company applications have traditionally been custom-designed for the enterprise and hosted in data centers. With the expansion of the internet and public cloud providers, many enterprises are migrating their applications to the cloud. Employees need to securely connect to these applications in an effortless manner. Here, we will introduce the concept of private access.
What is Private Access?
In the previous sections, we looked at the security needed when the users are accessing the public internet. Many enterprises host their core business applications in a private data center or in the public cloud. Most of the time, the employees work on these business applications as part of their daily work duties.
In the past, we saw that most company employees go to their corporate location, access the business applications using their internal LAN and desktops, and then go home at the end of the day. But as we explained in the workforce shift, the following happened:
- Business applications started to move to the cloud (web-based model).
- Employees wanted flexibility in terms of where and when they worked.
- The internet became the most popular and affordable transport platform.
Now, enterprises can't force their employees to go to a corporate location anymore. So, how do enterprises connect end users to the business applications without exposing either to the public internet? This is where Zscaler Private Access (ZPA) comes in.
How ZPA works
The primary use case for ZPA is to connect the end users and the business applications wherever they are, without even traversing the public internet. What ZPA does is use the internet as a transport medium and heavily leverages the Zscaler cloud.
While installing the service, an enterprise ZPA administrator does the following:
- End users are identified based on their department or location.
- Business applications that need to transition to ZPA are identified.
- The end user access policy to business applications is created using business needs.
- A small virtual machine called the App Connector is deployed near the business applications.
We can see this illustrated in the following diagram:
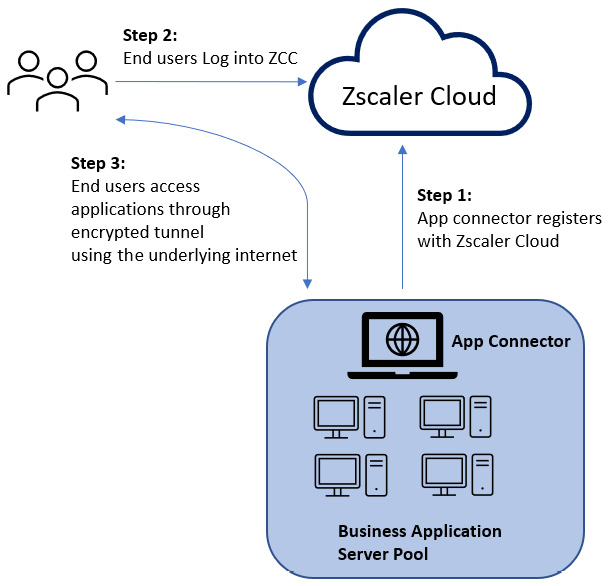
Figure 1.2 – Fundamental operation of ZPA ADD
When the App Connectors boot up, they discover the business applications and register with the Zscaler cloud, stating that they are ready to serve the end users to provide access to end users. This communication happens over secure tunnels using the internet as the underlying transport mechanism.
When users log into their corporate devices, they authenticate with the ZCC application, as described earlier. Based on Step 3, their application access is provisioned and ready upon authentication, and this happens in a transparent manner for the end user. The end users do not have to do anything special.
When the end users initiate the business application natively or using a web-based interface, their request is handled by the nearest Zscaler cloud. The Zscaler cloud already knows where that business application resides from App Connector registration. The Zscaler cloud then brokers the connection between the end user and the App Connector in the most optimum and secure manner.
As you can see, from an end user perspective, all they must do is log into ZCC, and everything just works! The end users or the applications are never exposed to the internet. You cannot attack what you cannot see!
ZCC
We saw ZCC mentioned in both the previous sections, so let's clarify things here. ZCC can be used for just ZIA, just ZPA, or both ZIA and ZPA. Ideally, the enterprise would use the same authentication mechanism so that their end users do not have to log into ZCC twice – once for ZIA and once for ZPA – which would be very confusing. ZCC is a central tool in most Zscaler implementations and as we will see in later chapters, ZCC offers a lot of different configurations that provide flexibility to each enterprise situation.



