Similar to Android, iOS applications also come in a specific zipped format called IPA, or an iOS App Store Package. iOS application packages can also be renamed by changing the extension to ZIP and then the components can be extracted, though the components of an iOS application package differ from those of an Android one.
iOS apps are mainly built using Objective-C and Swift, both of which can be disassembled using a disassembler such as Hopper or Ghidra. In Objective-C applications, methods are called via dynamic function pointers, which are resolved by name during runtime. These names are stored intact in the binary, making the disassembled code more readable. Unlike Android, in iOS, the application code is compiled to machine code that can be analyzed using a disassembler.
The following are the major components of an iOS application package:
Info.plist: Similar to the Android manifest file in an APK, this information property list file contains key-value pairs that specify essential runtime-configuration information for the application. The iOS operating system relies on the presence of this file to identify relevant information about the application and related files.- Executable: The file that runs on the device, containing the application's main entry point and code that was statically linked to the application target.
- Resource files: Files that are required by the executable file, and are required for the application to properly run. This may contain images, nib files, string files, and configuration files.
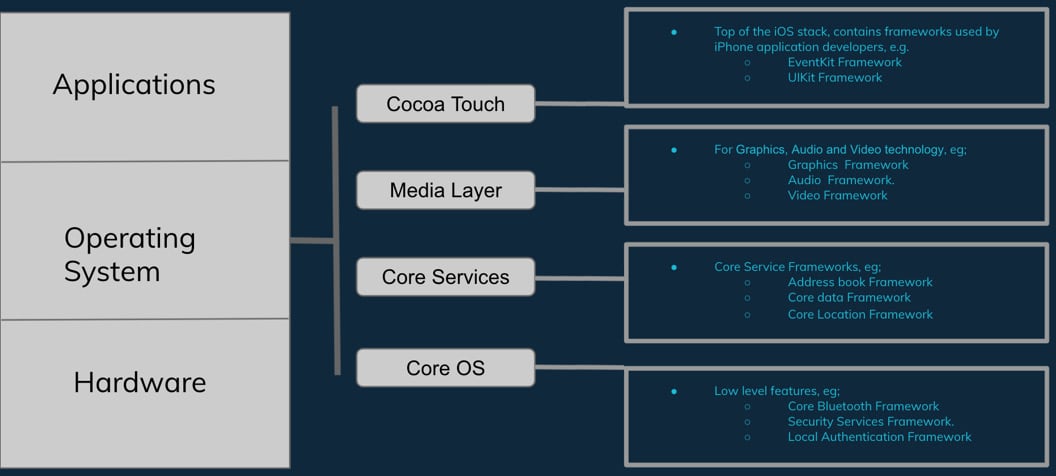
The following diagram illustrates the iOS architecture overview:
Figure 1.13 – iOS architecture
Let's see how to create a simple hello world application for iOS and then unzip it and look at its components:
- iOS apps are developed using Xcode. Download the latest version of Xcode from the App Store on Mac.
Figure 1.14 – Creating an Xcode project
- On the next screen, choose the default App template for your new project:
Figure 1.15 – Selecting the project template
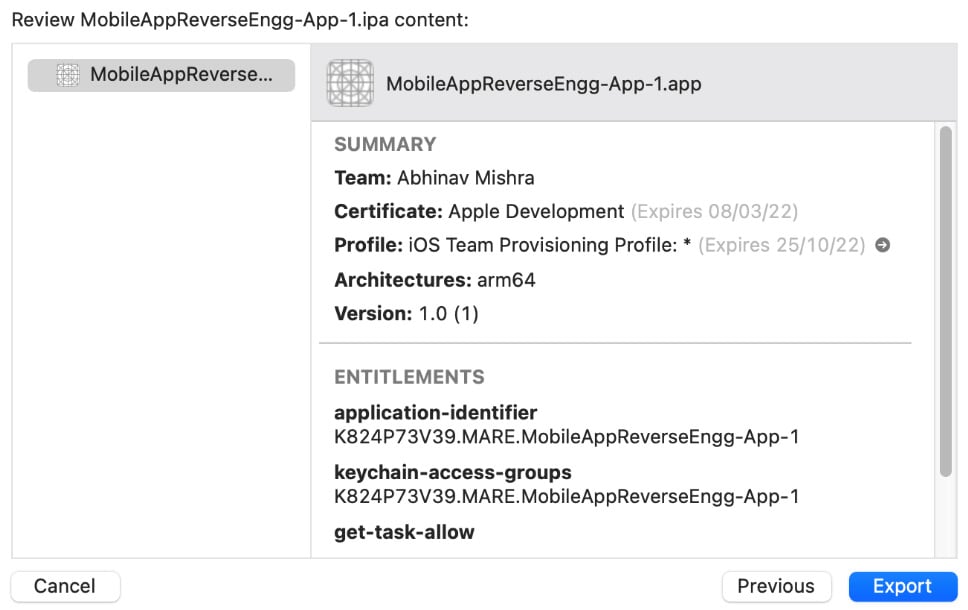
- On the next screen, provide a product name (any name you like), select a team, and provide an organization identifier. To create and export an IPA from Xcode, you need to have an Apple Developer license:
Figure 1.16 – Providing project details
- Select a location to save the project on your computer.
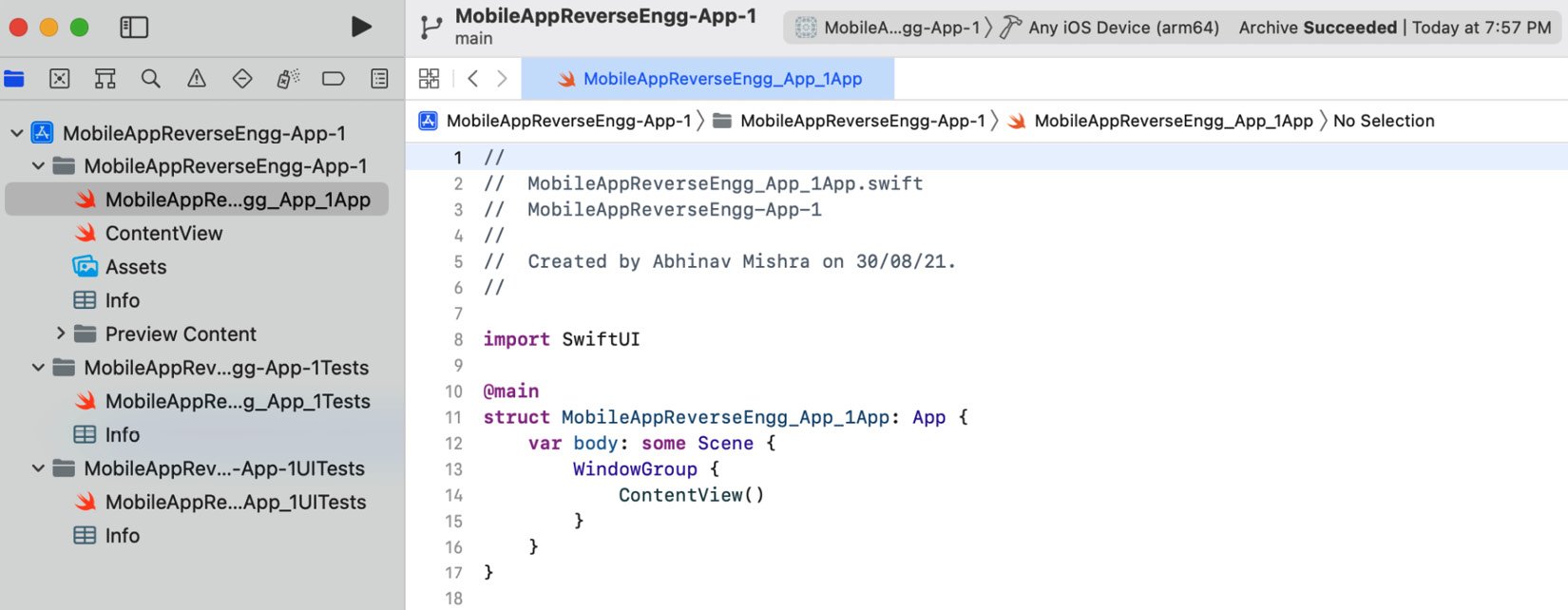
Xcode will now create a simple hello world application and you will see the following default code in the Xcode window:
Figure 1.17 – Project details
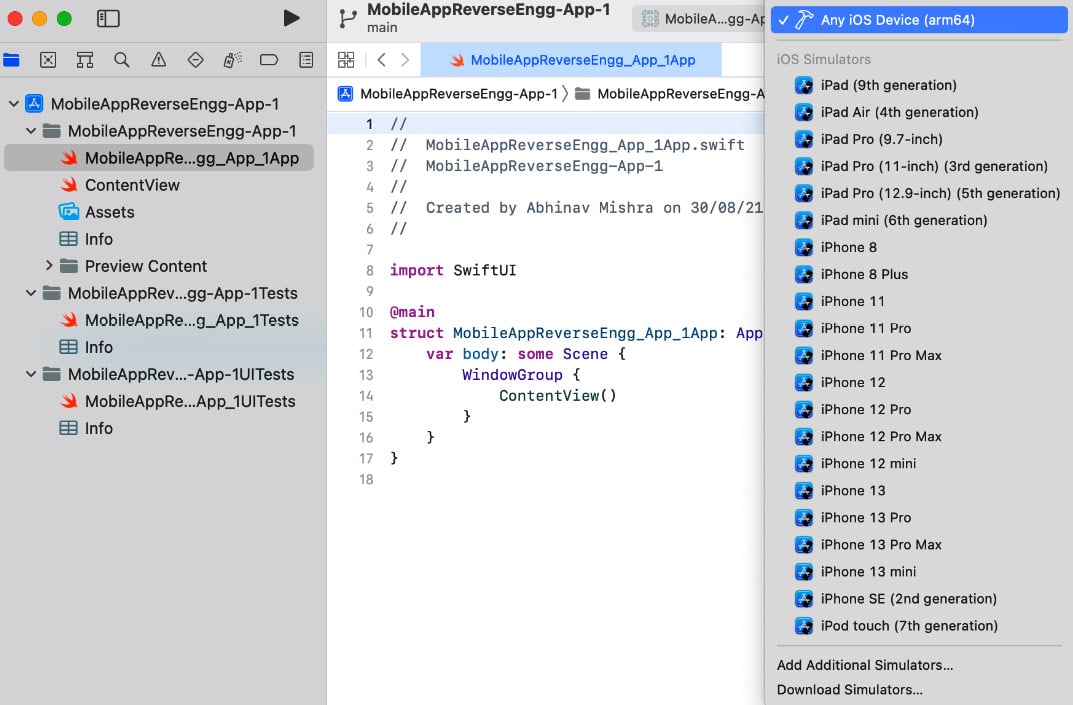
- Now you can try and run this app on one of the built-in iOS simulators. To do so, select one of the available simulators (just click on the name of simulator from top bar, and a list will open) as shown in the following screenshot:
Figure 1.18 – Selecting a simulator
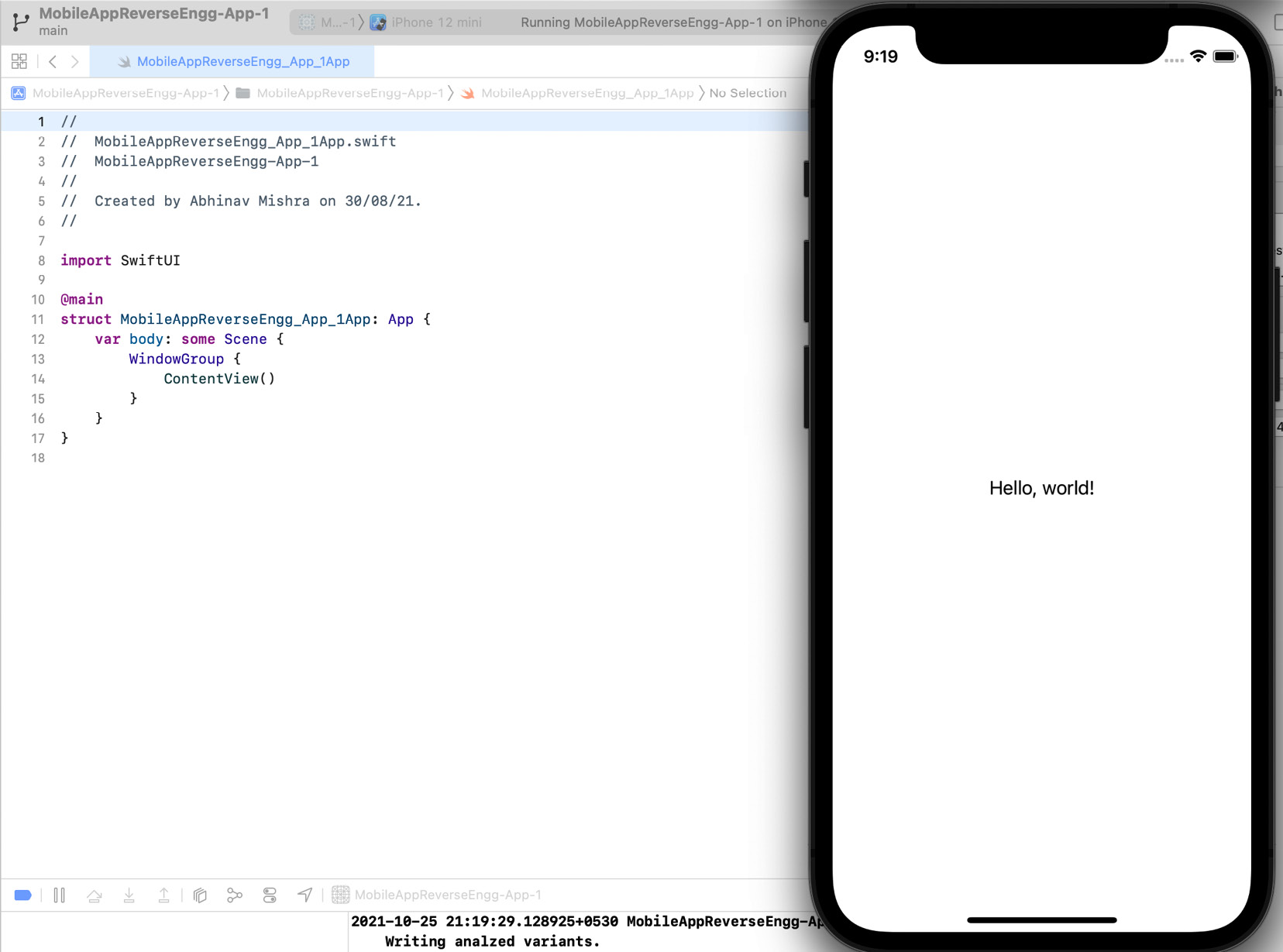
The app should run on the selected simulator:
Figure 1.19 – App running on the simulator
- Now, let's export the IPA from this Xcode project. To do so, select the Any iOS Device (arm64) option from the simulator options.
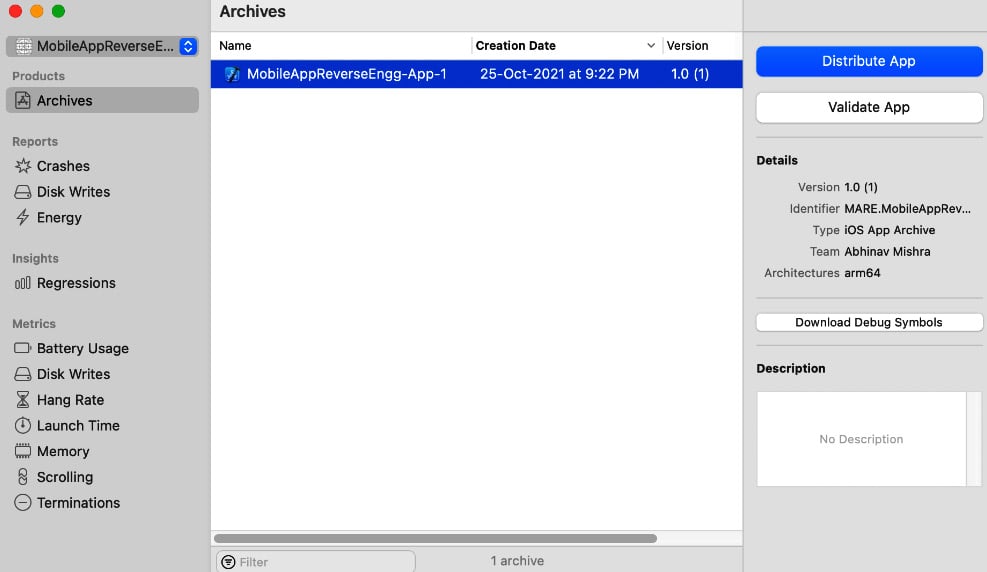
- Then, go to Product | Archive and select the Distribute App option:
Figure 1.20 – Exporting the application package
- On the next screen, select Development and leave the options on the subsequent screens at their defaults.
- Finally, you will be able to export the IPA together with some other compiled project files:
Figure 1.21 – Exporting the application package (cont.)
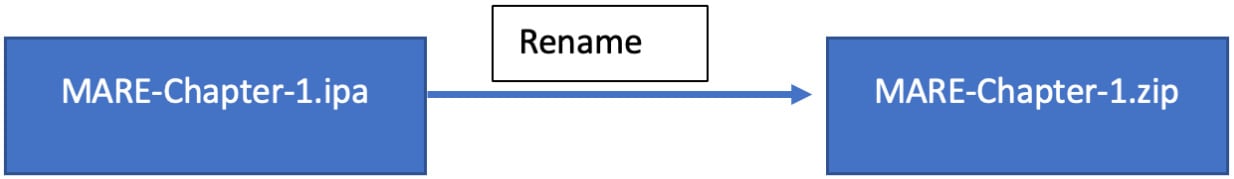
- Once the IPA is exported, simply change the extension of the file to
.zip:
Figure 1.22 – Diagram explaining the application (IPA) extraction process via renaming
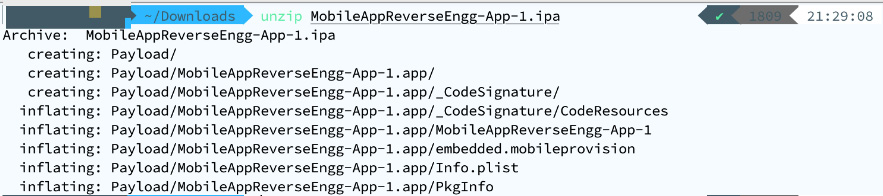
- Use any tool to unzip the file and extract its contents:
# unzip MARE-Chapter-1.zip
The following screenshot shows the results for reference:
Figure 1.23 – Extracting the content of the IPA after renaming it to ZIP
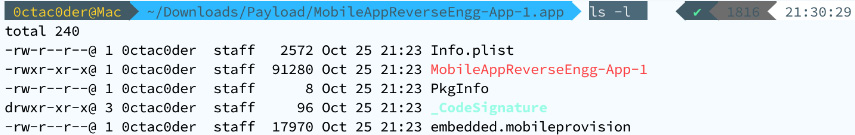
- Go into the
Payload directory and then inside the MobileAppReverseEngg-App-1.app file:# cd Payload
# cd MobileAppReverseEngg-App-1.app
- Let's analyze the components inside the IPA and compare it with the list here (iOS application fundamentals):
Figure 1.24 – Extracted content of the IPA
The following diagram illustrates the process of reverse engineering an iOS application:
Figure 1.25 – Overview of the reverse engineering process of an IPA
Have a look at Figure 1.3 to understand how a disassembled binary looks in Hopper disassembler.



 Free Chapter
Free Chapter