In today’s hyper-connected world, where global communication, commerce, and innovation are inseparable from digital infrastructure, cybersecurity is the critical guardian of our digital lives. Its role extends far beyond protecting personal data—cybersecurity is now fundamental to safeguarding industries, economies, and national security. As cyber threats evolve, cybersecurity’s responsibilities have expanded dramatically, encompassing everything from securing sensitive information to defending the critical infrastructure that sustains entire nations.
At the forefront of this defense is cybersecurity, acting as a shield against a range of threat actor—cybercriminals, hacktivists, and state-sponsored entities—all intent on exploiting vulnerabilities for their gain. As the complexity and frequency of cyberattacks increase, the consequences of inadequate security measures grow more severe. The stakes of cybersecurity failures are higher than ever, from disruptions to essential services and catastrophic financial losses to heightened threats to national security. In today’s digital age, robust cybersecurity is not just a priority; it is imperative for ensuring the stability and safety of our interconnected global systems. Every individual plays a crucial role in this collective defense.
The digital revolution has brought an era of unparalleled convenience and connectivity. We can now connect instantly with individuals across the globe, access vast amounts of information with a single click, and conduct business more efficiently than ever. However, this same interconnectedness has also introduced many risks and vulnerabilities.
Our growing dependence on interconnected devices, networks, and software has created a vast attack surface for cybercriminals to exploit. While the benefits of this connectivity are undeniable, it demands constant vigilance and proactive defense against the ever-evolving threats that target our digital world. In this ongoing battle, your vigilance is not just necessary—it’s indispensable.
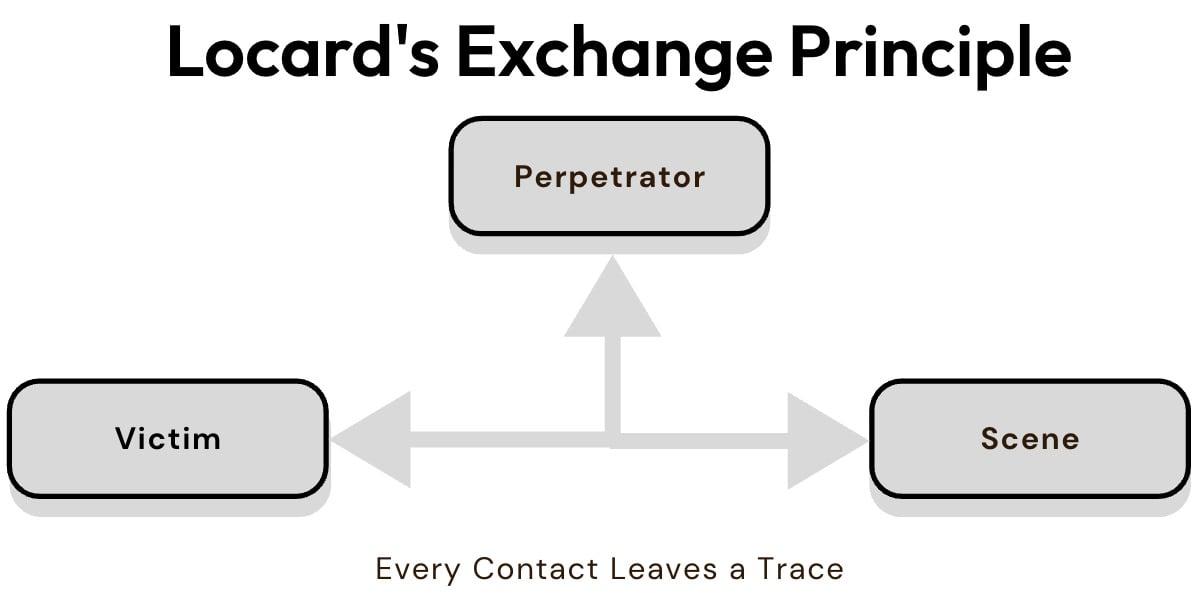
As cybersecurity professionals contend with various threat actors, from nation-states to hacktivists, understanding how to track and mitigate these threats is paramount. One guiding principle in this effort is Locard’s Exchange principle from forensic science, which posits that any interaction leaves behind traces. In the cyber world, attackers inevitably leave behind digital footprints—whether in network logs, metadata, or files. This inevitability reassures us that we can predict and identify their actions. This forensic approach is critical when investigating breaches, tracing threat actors’ movements, and implementing defensive strategies based on the evidence left behind.
Figure 1.1 – Locard's Exchange Principle
Data is the lifeblood of the modern world, with everything from personal information and intellectual property to critical infrastructure being stored and transmitted electronically. This wealth of data, while immensely valuable, has become a prime target for cybercriminals motivated by financial gain, political leverage, or the challenge of breaching security measures. As cyber threats intensify, cybersecurity emerges as a critical defense, employing various strategies, practices, and technologies to safeguard our digital assets and systems from relentless attacks.
Cybersecurity is proactive and adaptive at its core, continuously evolving to counter new threats and vulnerabilities. Security experts leverage their knowledge, advanced tools, and deep understanding of adversary tactics to stay ahead of malicious actors. The vast scope of cybersecurity encompasses various domains, including network security, which protects the flow of data; application security, which shields software from vulnerabilities; and information security, which ensures data confidentiality, integrity, and availability. Together, these disciplines form an essential defense in the digital age.
Cybersecurity extends its reach to mobile devices, the Internet of Things (IoT), cloud services, and emerging technologies such as artificial intelligence and quantum computing. Each new technological advancement presents opportunities and challenges, demanding innovative security solutions.
Hacktivism, driven by political or ideological motives, often leverages the vulnerabilities found in IoT devices and human error to disrupt systems. A significant example of this is the 2016 Mirai botnet attack, where thousands of unsecured IoT devices were hijacked to launch a massive Distributed Denial of Service (DDoS) attack, crippling websites and online services globally. This demonstrated how the interconnected nature of IoT devices can be weaponized.
In parallel, the human element remains a persistent risk in cybersecurity. Hacktivist groups such as Anonymous have frequently exploited human vulnerabilities, such as weak passwords or susceptibility to phishing. A famous case involved the 2011 hack of HBGary Federal, where social engineering and poor password hygiene exposed sensitive emails and client data. IoT vulnerabilities and human error highlight the expanding and evolving nature of the threat landscape. While technology is at the forefront of cybersecurity, the human element is equally crucial. Cybersecurity awareness and education play a pivotal role in fortifying our defenses. Individuals, from the average internet user to top-level executives, must be cognizant of the risks they face in the digital realm and take proactive steps to protect themselves and their organizations.
In this chapter, we will cover the following key topics:
- The evolving landscape of cyber threats
- The significance of cybersecurity
- Types of threat actors and motives
- Introduction to the Cyber Kill Chain concept
- The state of cybersecurity in 2024
- The cost of a data breach
Free Benefits with Your Book
Your purchase includes a free PDF copy of this book along with other exclusive benefits. Check the Free Benefits with Your Book section in the Preface to unlock them instantly and maximize your learning experience.



 Free Chapter
Free Chapter