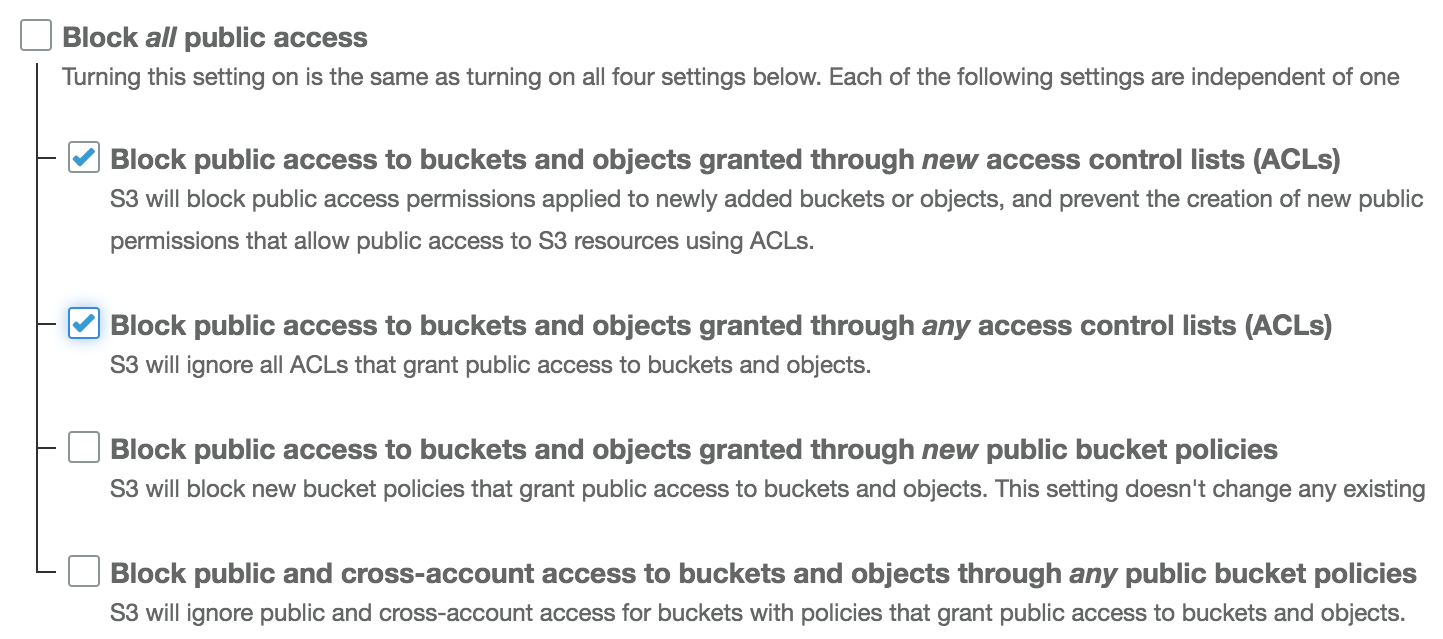
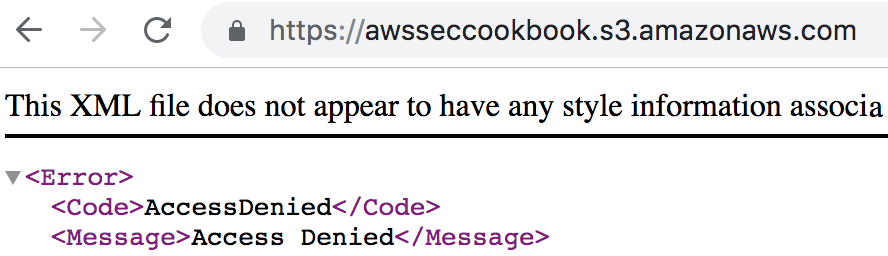
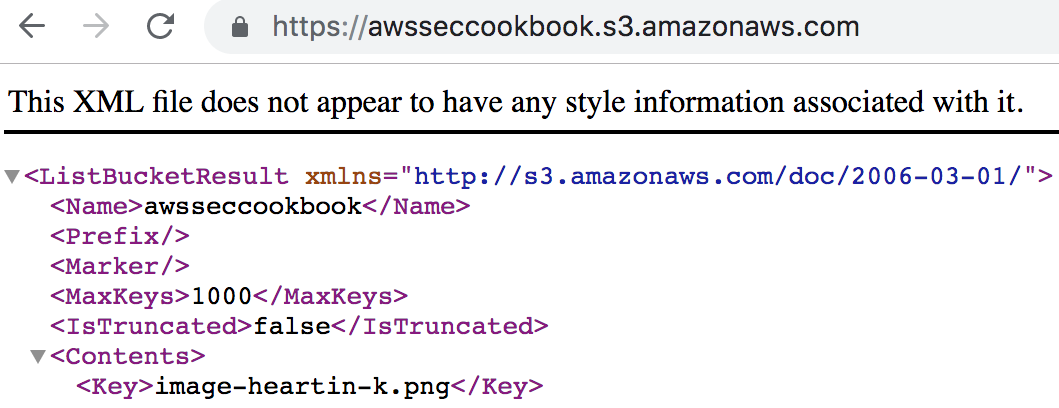
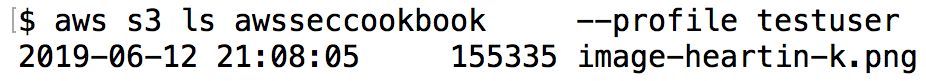In this recipe, we will learn to create bucket policies for our S3 buckets. Whenever possible, it is preferable to use a bucket policy or IAM policy instead of ACLs. The choice between bucket and IAM policies is mostly a personal preference. We can also create bucket policies using prefixes. S3 is an object store with no concept of folders, but prefixes can be used to imitate folders. Prefixes can represent objects as well.
-
Book Overview & Buying

-
Table Of Contents

AWS Security Cookbook
By :

AWS Security Cookbook
By:
Overview of this book
 Free Chapter
Free Chapter