Historically, there haven't been many scenarios that require Windows servers to have more than a single network card. This is because most of the roles that they were accomplishing were done on whatever single network they were plugged into. There was no need for a server to have direct connections to multiple networks because that was the router and switch's job, right? In today's Windows Server world, there are numerous roles that can take advantage of multi-homing, which simply means having multiple NICs connected to different networks at the same time. There are some proxy roles that can use multiple NICs; Remote Access roles such as DirectAccess and VPN recommend a dual-NIC setup, and you can even use a Windows Server as a general router if you want to.
I work a lot with DirectAccess and I find many multi-homed servers with incorrect network configurations. This recipe is a collection of points that need to be followed when configuring a Windows Server with multiple NICs to make sure it behaves and flows traffic as you expect it to.
You just need a Windows Server 2016 online for this one. We have two NICs installed on this server and they are plugged into different networks. I am prepping a Remote Access server that will sit on the edge, so I have one NIC plugged into the corporate internal network, while the other NIC is connected to the Internet.
To configure a Windows Server with multiple NICs, perform the following process:
- Only one Default Gateway: In your NIC properties, you need to make sure that you only have a Default Gateway identified on one of your NICs. This is the most common mistake that I find in the field. If you have two NICs, it would seem logical that you would simply populate their IP address settings just like you would with any server or computer, right? Nope. The purpose of a Default Gateway is to be the fallback or the route of last resort. Whenever your server tries to send out network traffic, it will search the local routing table for information on how to send out that traffic. If it does not find a specific route that corresponds to the IP address that you are sending to, then it will default that traffic over to the Default Gateway address. Therefore, you only ever want to have one Default Gateway assigned on a server, no matter how many NICs are connected. On all other NICs installed on the system, simply leave the Default Gateway field unpopulated inside the TCP/IP properties. By the way, for a DirectAccess server or for pretty much any other server that faces the Internet, the Default Gateway needs to be on the External NIC, so I will be leaving that field empty in the properties of my Internal NIC.
- Limit your DNS servers: Another common configuration that I have seen is to have DNS server addresses defined for every network adapter installed on the system. While this doesn't usually break anything like multiple Default Gateways can, it does cause unnecessary slowness when the system is trying to resolve DNS names. Try to have DNS server addresses configured on only one NIC. Once again, using our example DirectAccess server setup, I will be configuring DNS server addresses on my Internal NIC because that is necessary for DA to work. I will not be putting my public DNS server specifications into the External NIC; instead, I will leave those fields empty.
- Use static IP addresses: The roles and functions you may perform on a Windows Server that requires multiple NICs will be best served by having static IP address information assigned to those network cards. If you let one or more of the NICs pull information from DHCP, you could easily create a situation where you have too many DNS servers defined, or where you have multiple Default Gateways on your system. As we already know, neither of these scenarios is desirable.
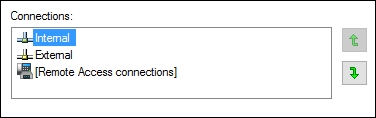
- Prioritize the NIC binding: It is a good practice to set a priority for your NICs so you can place the card that you expect to have the most network traffic as #1 in the list. For our DirectAccess server, we always want the Internal NIC to be placed on the top, so let's make sure that is set correctly using the following steps:
- Open up
Network and Sharing Centerand click onChange adapter settingsso that you are in theNetwork Connectionsscreen where you can see the network cards installed on your system. - Now press the Alt key on your keyboard and you will see the menus at the top of this window.
- Head into the
Advancedmenu and click onAdvanced Settings.... Now simply make sure that yourInternalNIC is listed on top:
- Open up
Note
The NIC binding prioritization order is a function that is no longer necessary in Windows Server 2016. The instructions are still included here because they apply to any older Windows Server operating systems, and should be followed on those platforms.
- Add static routes: A couple of minutes ago, you probably started thinking "Hey, if I don't have a Default Gateway on my Internal NIC, what tells the server how to get packets into the subnets of my internal network?" Great question! Because you only have one Default Gateway, when you need to send traffic out one of the other NICs, you need to make sure that a static route exists in the Windows routing table. This ensures that the server knows which interface gets traffic for each subnet. Make sure to check out our next recipe for specific information on how to add those routes.
Anybody can multi-home their server by simply plugging two NICs into two different networks. The tricky part is making sure that you configure those NICs and the operating system appropriately so that network traffic flows in the right directions at the right times. Following this list of rules will give you a solid foundation so that you can build out these types of scenarios and know that you are doing so in the correct fashion. Deviating from these rules will result in unexpected behavior, which sometimes is not immediately obvious. This can make for some very frustrating troubleshooting down the road.



