As for the physical infrastructure, we have to design it securely. We have seen that the network security is critical and that there a lot of possible attacks in this realm. Is it possible to design a secure environment to run OpenStack? Yes it is, if you remember a few rules:
Create different networks, at the very least for management and external data (this network usually already exists in your organization and is the one where all your clients are)
Never put ports on trunking mode if you use VLANs in your infrastructure, otherwise physically separated networks will be needed
The following diagram is an example of how to implement it:
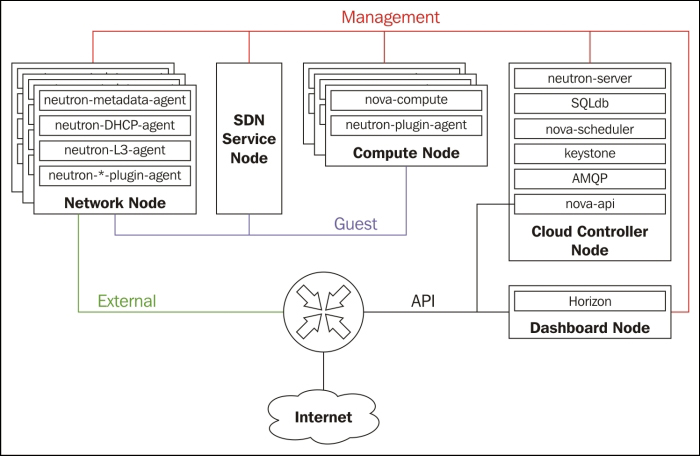
Here, the management, tenant external networks could be either VLAN or real networks. Remember that to not use VLAN trunking, you need at least the same amount of physical ports as of VLAN, and the machine has to be subscribed to avoid port trunking that can be a huge security hole.
A management network is...



