The main purpose of this chapter is to help you integrate with popular web applications and social media, although at the same time allow you to get familiarized with the foundational principles of OAuth 2.0 specification.
Before diving into the recipes for several use cases, let's look at the big picture of the most scenarios which will be covered. This will give you the opportunity to review some important concepts about OAuth 2.0 specification so we can stay on the same page with the terminologies used throughout the book.
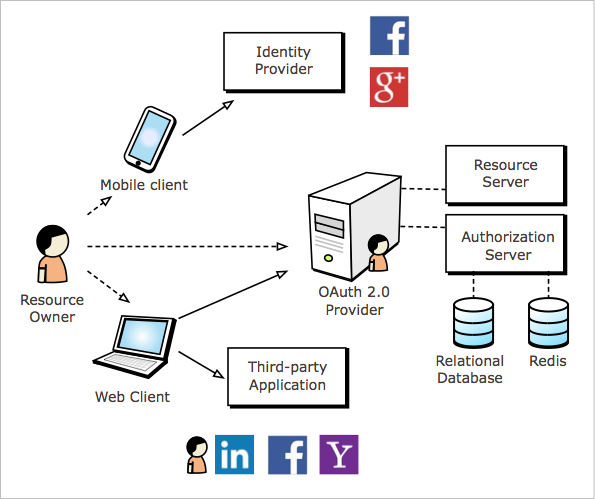
The preceding diagram shows the four main components of the OAuth 2.0 specification:
- Resource Owner
- Authorization Server
- Resource Server
- Client
Just to review the purpose of these components, remember that the Resource Owner is the user which delegates authority for third-party applications to use resources on its behalf. The third-party application mentioned is represented by the client which I depicted as Mobile client and Web Client. The user's resources are usually maintained and protected by the Resource Server which might be implemented together with the Authorization Server as a single component, for example. The composition of the Authorization Server and Resource Server are referred to as the OAuth 2.0 Provider to simplify the terminology given to the application which is protected by OAuth 2.0.



