Authentication and authorization are two of the most common aspects of the application security. In Windows, security is generally handled using the Kerberos or the NTLM security tokens. The user is provided with credentials that include a domain user ID and a password, and these credentials are validated against the user's entry in the Active Directory. Role-based security is implemented with the help of authorization managers that control the level of access for the user.
This works well within the boundaries of the Windows ecosystem; however, it gets difficult if the application has to support the users that do not have Windows Active Directory credentials. In the real world, the applications spanning multiple platforms interact with each other and require the security context to be shared. Using a claims-based identity model provides a robust way of handling authentication and authorization across the discrete systems. Throughout this chapter, we will explore the recipes that will help you gain an understanding of how claims-based identity is core to the .NET Framework 4.0 and help you get started on the Microsoft's Identity and Access Management paradigm. In this recipe, we will find out how a Windows identity can be abstracted with claims using the System.IdentityModel assembly in .NET Framework 4.0.
To create a collection of claims from a WindowsIdentity (System.Security.Principal) object, perform the following steps:
1. Create a new Visual C# Console Application project in Visual Studio 2010.

2. Add a reference to the System.IdentityModel assembly, as shown in the following screenshot:
3. Open the Program.cs file, and include the
System.IdentityModel.Claimsand theSystem.Security.Principalnamespaces.4. In the
Mainmethod, create a new instance of theWindowsClaimSetclass, and pass the current context identity as a parameter to the constructor:using (WindowsClaimSet claims = new WindowsClaimSet(WindowsIdentity.GetCurrent())) { }5. Loop through the
ClaimSetobject and print the claim information into the console output:using (WindowsClaimSet claims = new WindowsClaimSet(WindowsIdentity.GetCurrent())) { foreach (var claim in claims) { Console.WriteLine(string.Format("Claim Type: {0}", claim.ClaimType)); Console.WriteLine(string.Format("Resource: {0}", claim.Resource.ToString())); Console.WriteLine(string.Format("Right: {0}", claim.Right)); Console.WriteLine ("**********************************************"); } } Console.ReadLine();6. Compile and run the project. The result is displayed in the console window:
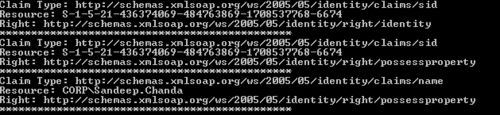
The WindowsClaimSet class inherits from the System.IdentityModel.Claims.ClaimSet. ClaimSet represents a collection of claims ( System.IdentityModel.Claims.Claim) associated with an entity. The WindowsClaimSet constructor accepts the current Windows user identity as a parameter and returns a ClaimSet object containing the collection of claims that represent the Windows Active Directory groups of the user. The current Windows user identity is fetched using the WindowsIdentity.GetCurrent method. Generated ClaimSet can be used to create a signed security token that can be passed on to a service to create a security context and implement role-based access control. We will see how to create a security token from a ClaimSet object later in the chapter.
Note
The default expiration time for the claims collection is set to 10 hours. You can explicitly set the expiration time in the WindowsClaimSet overloaded constructor.
A claim is used to identify a user or provide access to a particular resource requested by the user. There are three properties exposed by the Claim class:
ClaimType:It identifies the type of claim. In our example,Sid(security identifier) andNameare the two claim types displayed in the console window. A list of supported claim types is available at the following URL: http://msdn.microsoft.com/en-us/library/system.identitymodel.claims.claimtypes.aspx.Resource:It identifies the resource associated with the claim.Right:It is a URI representing theIdentityorPossessPropertyright associated with the claim.PossessPropertydetermines whether the user has the access toResource.
Both the Claim and the ClaimSet classes are serialization-friendly, which allows them to be transmitted over service boundaries.
In addition to WindowsClaimSet, the System.IdentityModel.Claims namespace provides a DefaultClaimSet class that allows you to create your implementation of claims, and a X509CertificateClaimSet class to abstract claims from an X.509 certificate.
The System.IdentityModel.Policy namespace exposes a AuthorizationContext class that can be used to evaluate the authorization policies in a sent message. The AuthorizationContext class has a ClaimSet property that allows a service to retrieve all the claims associated with the security token in the sent message. You can learn more with an example in the MSDN documentation at http://msdn.microsoft.com/en-us/library/system.identitymodel.policy.authorizationcontext.claimsets.aspx.



