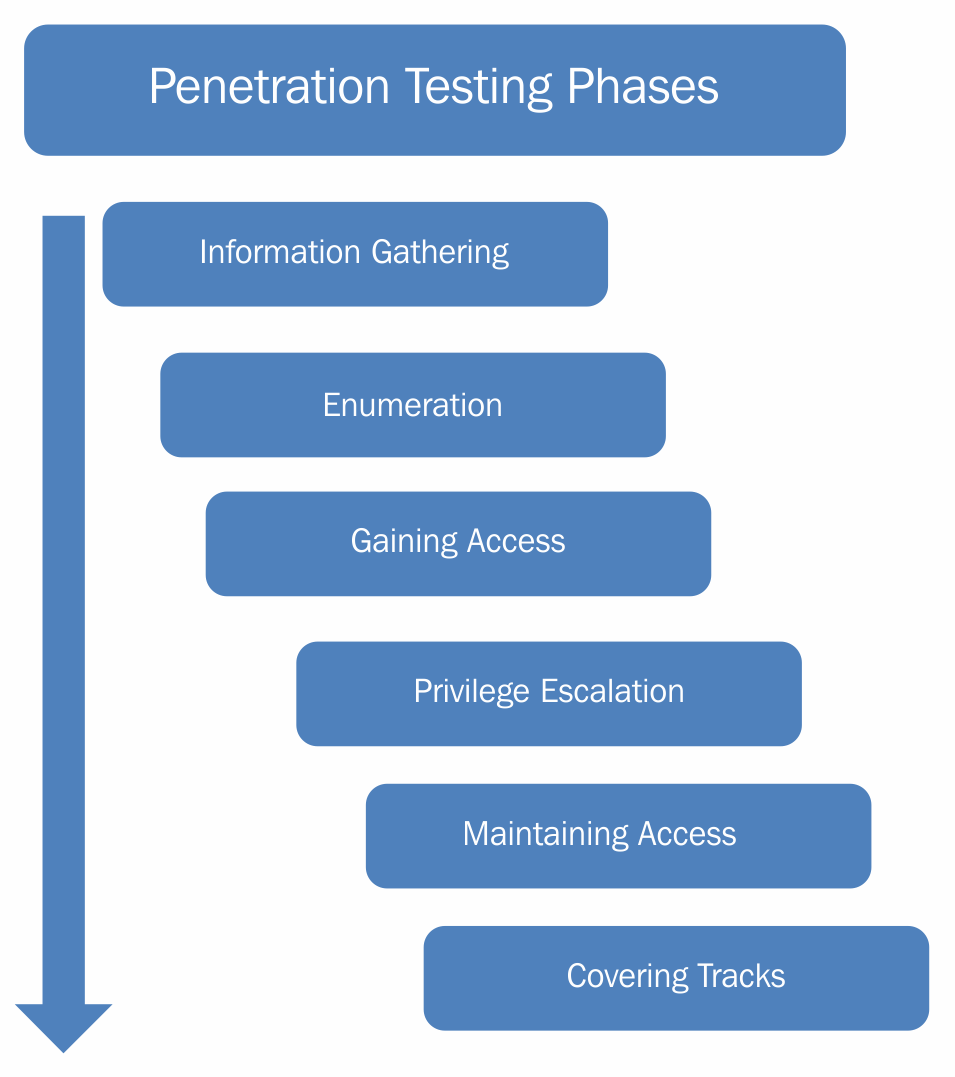
Penetration testing is not just a single activity, but a complete process. There are several standards available that outline steps to be followed during a penetration test. This section aims at introducing the penetration testing lifecycle in general and some of the industry-recognized penetration testing standards.
-
Book Overview & Buying

-
Table Of Contents

Network Vulnerability Assessment
By :

Network Vulnerability Assessment
By:
Overview of this book
The tech world has been taken over by digitization to a very large extent, and so it’s become extremely important for an organization to actively design security mechanisms for their network infrastructures. Analyzing vulnerabilities can be one of the best ways to secure your network infrastructure.
Network Vulnerability Assessment starts with network security assessment concepts, workflows, and architectures. Then, you will use open source tools to perform both active and passive network scanning. As you make your way through the chapters, you will use these scanning results to analyze and design a threat model for network security. In the concluding chapters, you will dig deeper into concepts such as IP network analysis, Microsoft Services, and mail services. You will also get to grips with various security best practices, which will help you build your network security mechanism.
By the end of this book, you will be in a position to build a security framework fit for an organization.
Table of Contents (15 chapters)
Preface
 Free Chapter
Free Chapter
Vulnerability Management Governance
Setting Up the Assessment Environment
Security Assessment Prerequisites
Information Gathering
Enumeration and Vulnerability Assessment
Gaining Network Access
Assessing Web Application Security
Privilege Escalation
Maintaining Access and Clearing Tracks
Vulnerability Scoring
Threat Modeling
Patching and Security Hardening
Vulnerability Reporting and Metrics
Other Books You May Enjoy