Windows Intune is a subscription-based management solution that utilizes Microsoft cloud-based services to manage Windows-based PCs wherever they may be. It is primarily intended to provide all of the management power that SCCM has to offer to small to medium-sized organizations that do not wish to implement on-premises servers.
One of the features it provides is Endpoint Protection. The anti-malware client used by Intune is identical to the one SCEP uses, with the exception that Intune client reports back to Microsoft's cloud services.
If you have not tried Intune before, Microsoft offers a free 30-day trial to grant you access to all of its features. This recipe walks you through the process of installing the Intune client, enabling Endpoint Protection from the console, and verifying that your Intune client reports back to your Intune console when a virus is detected. The recipe assumes that you have signed up for a trial or own a subscription to Intune.
If you have not signed up for Intune, a free trial is offered on the following link:
http://www.microsoft.com/en-us/windows/windowsintune/pc-management.aspx
You will need to have administrator access to the Intune console and local administrator permissions on the PC you're performing this recipe on.
Now, perform the following steps:
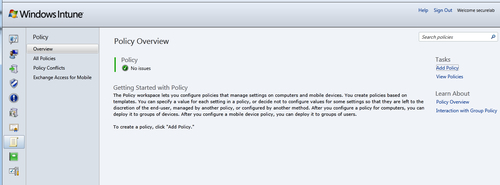
1. Begin by logging into the Intune console at https://manage.microsoft.com/WindowsIntune from the PC that you are testing with. Click on the scroll-shaped icon on the left-hand side of the console to access the Policy page. Refer to the following screenshot:
2. Next, click on the Add Policy button to create a new policy. The Create New Policy wizard should appear within your browser. Select Windows Intune Agent Settings and check the radio button next to the option for Create and Deploy a Custom Policy. Then click on the button titled Create Policy to proceed, as shown in the following screenshot:

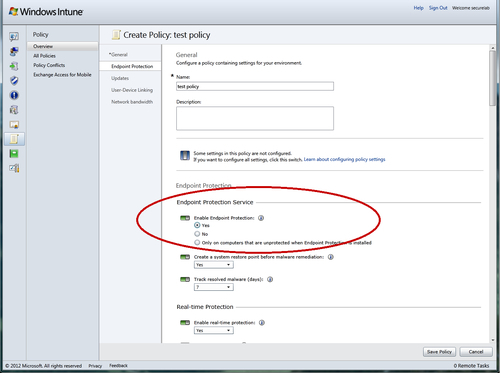
3. Your browser should now show you a policy template. Select Endpoint Protection from the center ribbon and locate the section titled Endpoint Protection Service. Click on the radio button next to the word Yes under the title Enable Endpoint Protection. This will force the removal of competing anti-malware products and the installation of Intune's Endpoint Protection client. The rest of the settings in this section should look familiar to you; they are the same set of options that you configure in SCEP when you are in the SCCM console. For now, just take the defaults and click on the Save Policy button to proceed, as shown in the following screenshot:
4. You will be prompted with the option to deploy the policy; select the Yes button to proceed, as shown in the following screenshot:

5. At this point, you can choose to deploy the policy to all of your Intune clients or a subset of clients. In this example, I will apply the policy to all clients. To do so, select All Devices from the column on the left-hand side and click on the Add button to move it over to the selected groups column. Then, click on OK to proceed, as shown in the following screenshot:

6. Next, we will install the Windows Intune client on your test PC. Click on the bottom button on left-hand side ribbon (the one with a screw driver and wrench) to get to the Administration page. Click on the Download Client Software button and the client software will download to your PC. Refer to the following screenshot:

7. Once the download is complete, extract the zip file and run
Windows_Intune_Setup, as shown in the following screenshot:
8. The Windows Intune Setup wizard should open. Click on Next on the first page to proceed, as shown in the following screenshot:

9. The installer will run for a few minutes; if all is successful, you will see a window stating the wizard has completed. Click on Finish to close it out, as shown in the following screenshot:

10. To verify whether the Intune client is on your PC, check the system tray. The Intune icon should now be there, as shown in the following screenshot:
11. After a few minutes, the Windows Intune Endpoint Protection client should also appear in the system tray. If you open it, you will notice that it is identical to the SCEP client except for the title on the top of the user interface. Refer to the following screenshot:
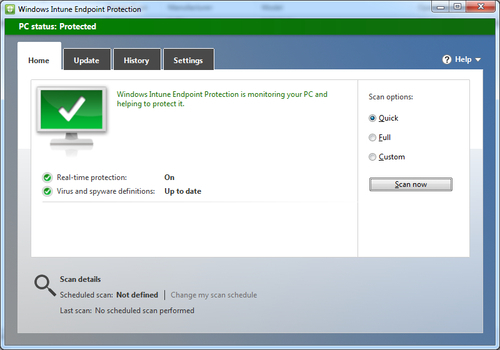
12. In order to test whether the Endpoint Protection client is working correctly and reporting to your Intune service in the cloud, I would suggest using the Eicar string to simulate a malware event. Eicar can be accessed at the following URL: http://www.eicar.org/
This is a completely safe packet of data that is added to the definitions of most anti-malware products for testing purposes.
13. Once you have triggered the Eicar detection, log back into your Intune dashboard and click on the icon for Endpoint Protection (the blue and white shield) from the ribbon on the left-hand side. If your client reported correctly, you should see an
Eicar_test_filedetection, as shown in the following screenshot: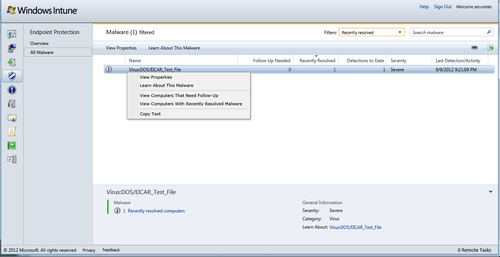
Windows Intune is a cloud-based management solution that offers a host of features, including the ability to deploy and manage a version of Microsoft's Endpoint Protection client.
Once the Intune client is on a PC, we can then deploy Endpoint Protection to the PC by setting a policy which requires the client to be already installed. After the client is installed, visibility into the state of the Endpoint Protection client as well as alerting for malware events, is accessible through the Intune management console.
In addition to being a great option for small to medium-sized organizations, some large companies may find Intune a suitable option for covering niche users. For example, if a large organization was to acquire a smaller organization and needed a stopgap solution to manage their systems, before their domains can be integrated into your root forest. Or, if for some political reason, part of an organization needed to be permanently managed at arm's length.



