We are able to manage one or all the aforementioned security features from one of the administrative tools of the device, a graphical interface (the web-based manager), and a command line (CLI). In the following screenshot, we can see the dashboard of the web-based manager and the CLI paired in the same screen:
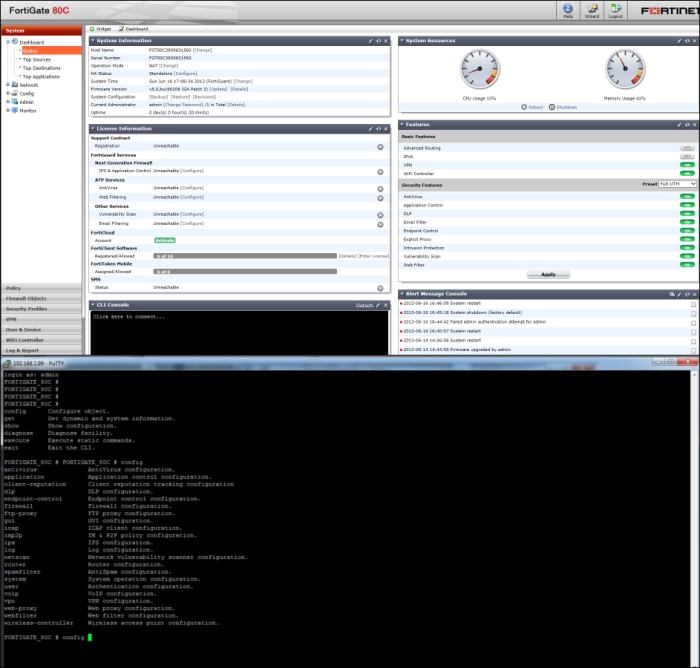
Access to the web-based manager requires a browser and an Ethernet connection between the FortiGate unit and the administrator's workstation.
The CLI can be used inside the graphical dashboard or we can detach it to use the command line in a separate window. The CLI is also the only administrative access we have when we access a FortiGate from a Telnet (or SSH) connection.
Note
A Telnet session uses clear text in all transmissions. Everything we type during a Telnet session, including passwords, is basically readable on the network. SSH encrypts information and makes it unreadable. If we have the option to select a connection type, SSH is to be preferred over Telnet.
We are able to open the CLI from the browser as a part of the web-based manager or using a terminal connection that requires an RJ-45 to DB-9 serial cable and a terminal emulation client like PuTTY.
While the graphical interface is easier to manage and does not require knowledge of specific commands, the command line has some advantages:
To troubleshoot problems with the operation of a FortiGate as we are able to use the
diagnose debugcommand in the CLI console. This is something we will see in more detail in Chapter 5, Troubleshooting.To script and automatize operations.
For accessing configuration items that are only available using the CLI. An example is the FortiGate Session Life Support Protocol (FGSP) explained in Chapter 4, High Availability.
To apply modifications and changes on multiple devices in a reliable and less error prone manner.



