-
Book Overview & Buying

-
Table Of Contents

Threat Modeling Best Practices
By :

 Sign In
Start Free Trial
Sign In
Start Free Trial

The threat modeling process will create a paper trail of artifacts that detail the findings from the activity. The security architecture diagram, the list of threat scenarios, and the identified threats all need to be cataloged and stored for tracking and future reference. Some organizations may require the security team to internally manage and maintain the documentation and artifacts under strict access controls and limit the visibility of this data. I do not recommend this approach.
Threat models and their identified risks should be made available to all stakeholders, as this demystifies the process and allows for more eyes and insight into how the practice is supporting the organization.
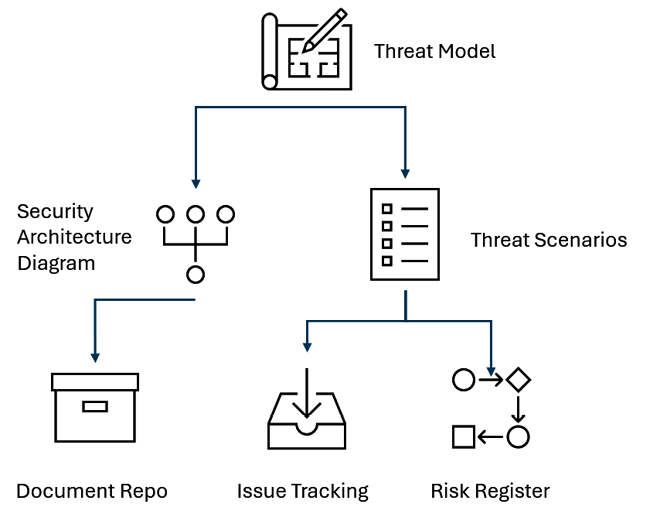
Figure 9.1: Artifacts from a threat model and their storage
For those organizations that have an open approach to their threat modeling artifacts, where they reside in the organization depends on how the documentation is already managed. An...

Change the font size
Change margin width
Change background colour