The Open Web Application Security Project (OWASP), is a global community that focuses on security awareness and the development of secure applications. While this may be thought of as a single application or platform, OWASP is actually a collection of projects that can focus on any number of aspects of applications security. For this recipe, we will focus on the OWASP Broken Web Application (BWA) project to provide us with a standardized platform for the testing of our tools in later chapters.
Installing OWASP-BWA
Getting ready
To install the OWASP-BWA image, we will need to do the following:
- Download the latest version of OWASP-BWA in compressed form from https://sourceforge.net/projects/owaspbwa/
- Have VirtualBox installed and configured
How to do it...
To install OWASP-BWA into our VirtualBox environment, we will do the following:
- Unzip the ZIP file containing the OWASP-BWA files into a location you will reference in the next few steps.
- From the console of VirtualBox, on the upper left, we will select the New icon to begin the creation of a new virtual machine.
- We will name our new virtual machine OWASP-BWA, and define it as a 64 bit Ubuntu Linux system:
 Creating a virtual machine for OWASP-BWA
Creating a virtual machine for OWASP-BWA - Leave the default memory allocation as 1024 MB, and click Next.
- You will now select Use existing virtual hard disk and navigate to the directory where you unpacked OWASP-BWA. From that directory, select the following and click Create:
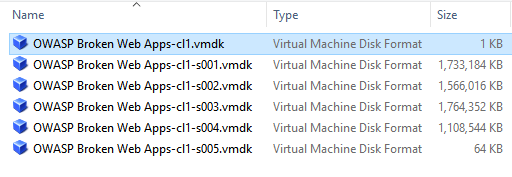
Selection of OWASP-BWA virtual disk
- Once you have created the virtual machine, we will need to make sure that the correct network interface has been designated. Right-click on on our new host on the left, and select Settings. Navigate to Network and ensure that the Adapter 1 is attached to the Host-only Adapter, and that the other adapters are not enabled:
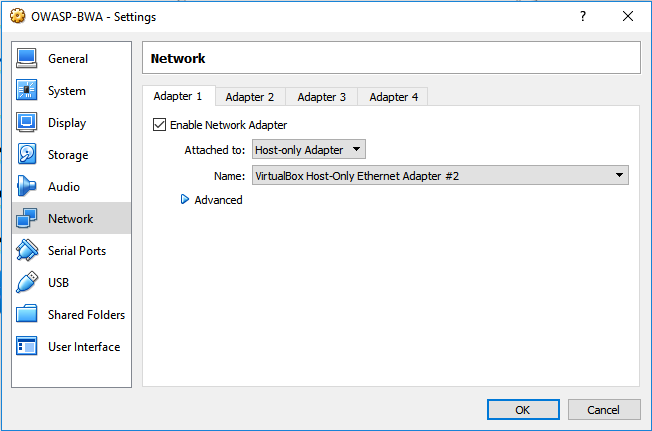
Designating the network adapter for OWASP-BWA in VirtualBox
- Once complete, start the new virtual machine and ensure that it boots properly.
It is very likely that fsck will run when first started due to the length of time since last run. You can allow this to complete to ensure there is no observed disk corruption - it only takes a few minutes.
- Once fully booted, login as root with the password owaspbwa.
- Ensure that you are receiving an IP address from DHCP by issuing ifconfig eth0 from the command line.
- Open a web browser, and navigate it to the IP address of the OWASP-BWA guest. Ensure that you are able to see the different projects within OWASP-BWA. If you are able to see the following web page, you have successfully configured OWASP-BWA:
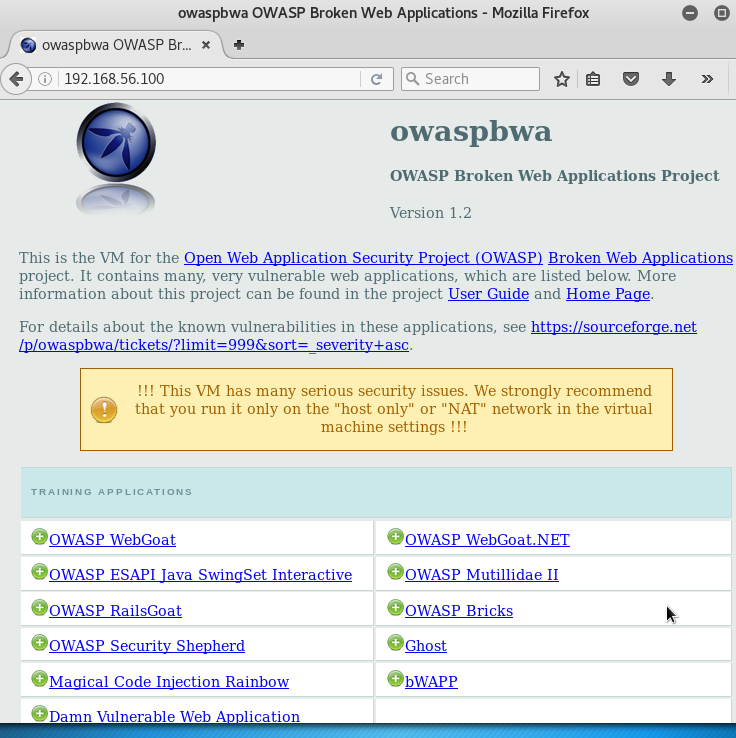
Confirmation of services running on OWASP-BWA



