For this scenario, we will construct a penetration test environment that relies quite heavily on pivoting. We will also use this scenario to try out some more inventive methods of setting scenes and will provide an interesting brief. I will reuse vulnerabilities from earlier in the book, but these environments can be set up with any vulnerabilities of your choosing.
The structure of the scenario is broken down into the following:
Network diagram
Brief
Setup
Exploitation guide
Variations
Summary
As you can see, the setup for the network diagram is fairly simple, as shown in the following diagram:
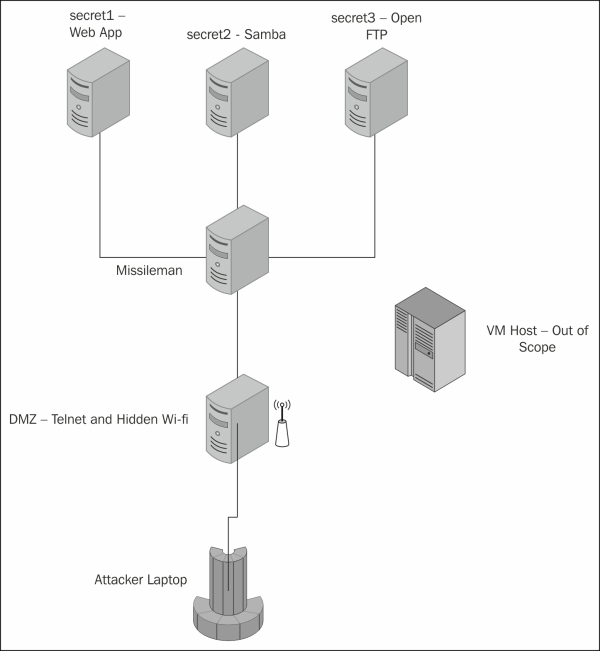
We start with a host called DMZ that is hosting a hidden wireless network. This is the breach that we will refer to in our brief. The DMZ host is also housing a telnet solution (from Chapter 2, Linux Environments) and a legitimate SSH server. Within the server itself, a set of obfuscated credentials for both DMZ and missileman are stored...



