-
Book Overview & Buying

-
Table Of Contents

How to Measure Anything in Cybersecurity Risk
By :

 Sign In
Start Free Trial
Sign In
Start Free Trial


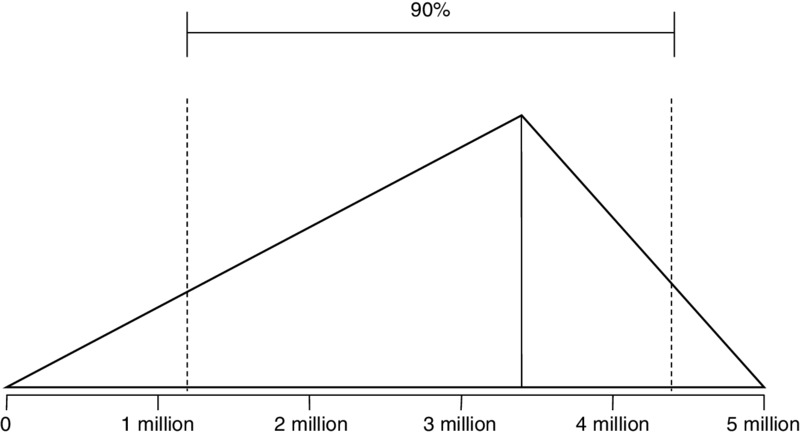
Figure A.1 Triangular Distribution
Parameters:
Note that UB and LB are absolute outer limits—a 100% CI.
For a triangular distribution, the UB and LB represent absolute limits. There is no chance that a value could be generated outside of these bounds. In addition to the UB and LB, this distribution also has a mode that can vary to any value between the UB and LB. This is sometimes useful as a substitute for a lognormal, when you want to set absolute limits on what the values can be but you want to skew the output in a way similar to a lognormal. It is useful in any situation where you know of absolute limits but the most likely value might not be in the middle, like the normal distribution.

Change the font size
Change margin width
Change background colour