In this section, we'll take a look at our testing lab environment. We will start by installing the VirtualBox software to run our lab VM. We'll access the vulnerable web application, get familiar with the text editor, and finally, I will give you an important warning.
The first tool that we need is VirtualBox. This will allow you to run the lab environment virtual machine created for this training. You can download VirtualBox from https://www.virtualbox.org/wiki/Downloads. Choose your host OS and download the installer. After downloading VirtualBox, we can download the virtual machine created for this course from https://drive.google.com/open?id=0ByatLxAqtgoqckVEeGZ4TE1faVE.
Once the file is downloaded, we can proceed with the installation of VirtualBox.
Install VirtualBox, which in my case I have to do by double-clicking on the .dmg file. Follow the installation instructions. And once you're finished, decompress the lab virtual machine. In my case, I use an archive in OS X. You can use 7 ZIP in other platforms.
Once decompressed, we will start VirtualBox.
Open the VM. Once the VM is loaded in VirtualBox, we'll start the machine and wait for it to boot until we get the login prompt. We'll log in with the user Packt and the password secret.
Now, we have our lab ready for action. For the purpose of this book, we have created a vulnerable web application that will allow us to test for different types of vulnerabilities using our own developed tools. The application simulates a very simple banking application.
It is developed in PHP with MySQL and it is served by Apache. Now, we'll open the browser in our VM. Load the URL www.scruffybank.com. I created an /ETC/hosts entry to redirect that hostname to local host. This application is running in an Apache server in the VM.
You should see the index page. If you click on Learn More, you will see the following information:
On the top right-hand side, you can access the login page.
Our last tool in the lab is the text editor, where we'll write the scripts. One possible choice would be Atom, a multi-platform open source and free editor developed by the GitHub folks. Feel free to install or use the editor you prefer.
In order to start Atom, go to the desktop item named Atom and the editor will start with a blank file. You can start typing the code, but until you save the file and add an extension, it won't do syntax highlighting.
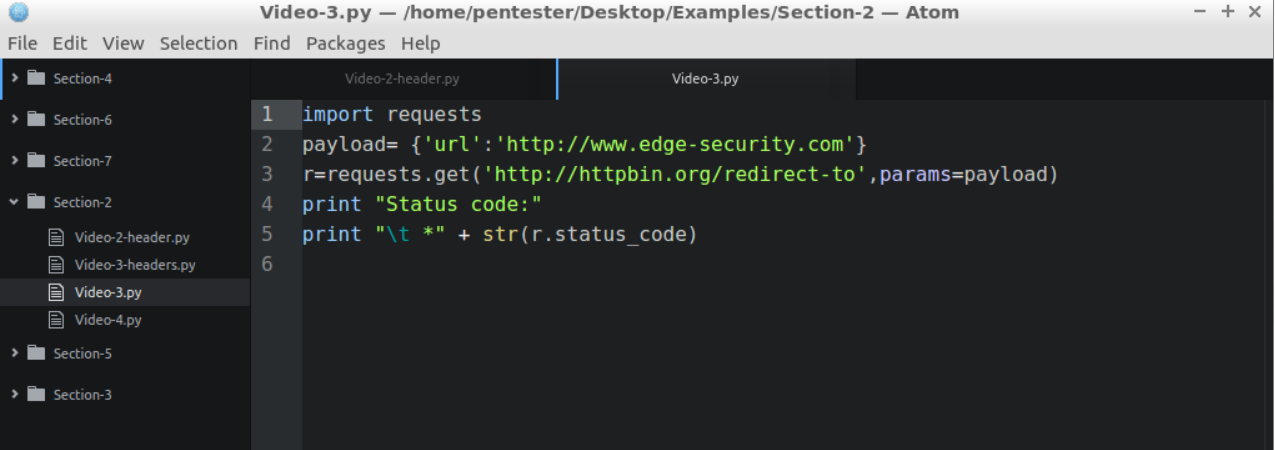
I will open an example in my home directory called Video-3.py. This is what a Python script looks like in Atom:
In many countries, these activities are illegal, again without proper permissions. Always use a testing environment whenever you want to try a new tool or technique. Again, whenever you'll perform a penetration test for a customer, get written authorization.


