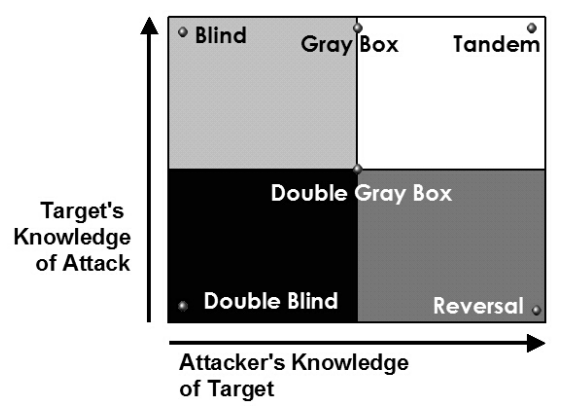
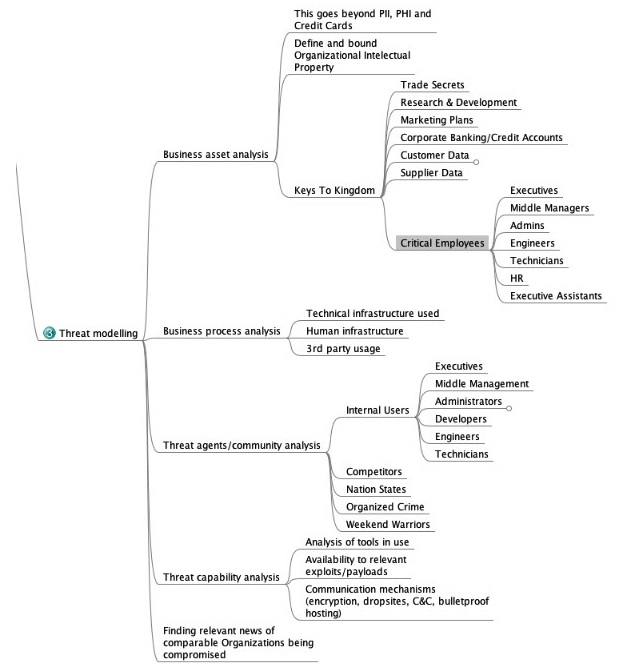
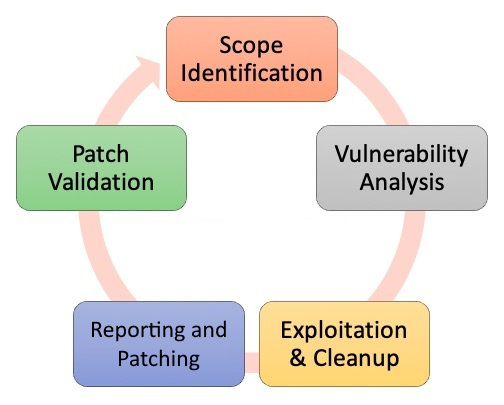
As we all know, there are no official penetration testing standards defined; however, our security community has introduced a few standards for all security personnel to follow. Some of the commonly known standards are the Open Source Security Testing Methodology Manual (OSSTMM), the Penetration Testing Execution Standard (PTES), and the Information Systems Security Assessment Framework (ISSAF). Most of them follow the same methodology, but their phases have been named differently. We will take a look at each of them in the following sections and cover PTES in detail.
-
Book Overview & Buying

-
Table Of Contents

Hands-On Web Penetration Testing with Metasploit
By :

Hands-On Web Penetration Testing with Metasploit
By:
Overview of this book
 Free Chapter
Free Chapter