-
Book Overview & Buying

-
Table Of Contents

The Official (ISC)2 Guide to the CCSP CBK - Second Edition
By :

 Sign In
Start Free Trial
Sign In
Start Free Trial


Data security is a core element of cloud security (Figure 2.1
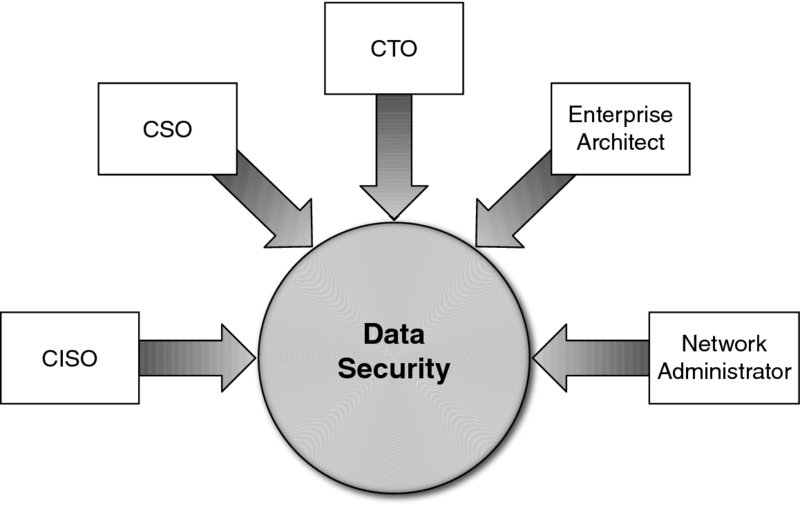
Figure 2.1 Many roles are involved in providing data security.
The data security lifecycle, as introduced by the Securosis Blog and then incorporated into the CSA guidance, enables the organization to map the different phases in the data lifecycle against the required controls that are relevant to each phase.1
The lifecycle contains the following steps:
The data lifecycle guidance provides a framework to map relevant use cases for data access, while assisting in the development of appropriate controls within each lifecycle stage.
The lifecycle model serves as a reference and framework to provide a standardized approach for data lifecycle and data security. Not all implementations or situations align fully or comprehensively.

Change the font size
Change margin width
Change background colour