14.7 SSH Key-based Authentication using PuTTY
For Windows systems that do not have OpenSSH available, or as a more flexible alternative to using PowerShell, the PuTTY tool is a widely used alternative. The first step in using PuTTY is to download and install it on any Windows systems that need an SSH client. PuTTY is a free utility and can be downloaded using the following link:
https://www.chiark.greenend.org.uk/~sgtatham/putty/latest.html
Download the Windows installer executable that matches your Windows system (32-bit and 64-bit versions are available) then execute the installer to complete installation.
If a private key already exists on another system, create the .ssh folder in the home folder of the current user and copy the private id_rsa key into it.
Next, the private key file needs to be converted to a PuTTY private key format file using the PuTTYgen tool. Locate this utility in the Windows Start menu and launch it:
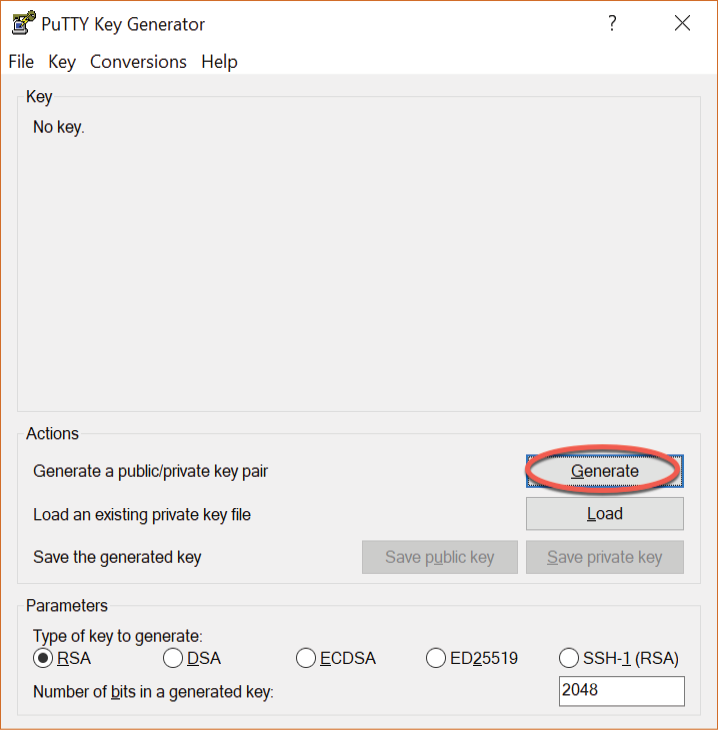
Figure 14-2
Once launched, click on...



