-
Book Overview & Buying

-
Table Of Contents

MuleSoft for Salesforce Developers - Second Edition
By :

 Sign In
Start Free Trial
Sign In
Start Free Trial


In this section, let’s simplify how we can achieve API security using MuleSoft.
In Figure 10.1, we can see that the application network is formed using reusable building blocks, such as Mule applications, end systems, and non-Mule applications. Here, the outer dotted line depicts the periphery of the Mule application, and the inner dotted line shows the integration between a Mule application and an external end system/non-Mule application.
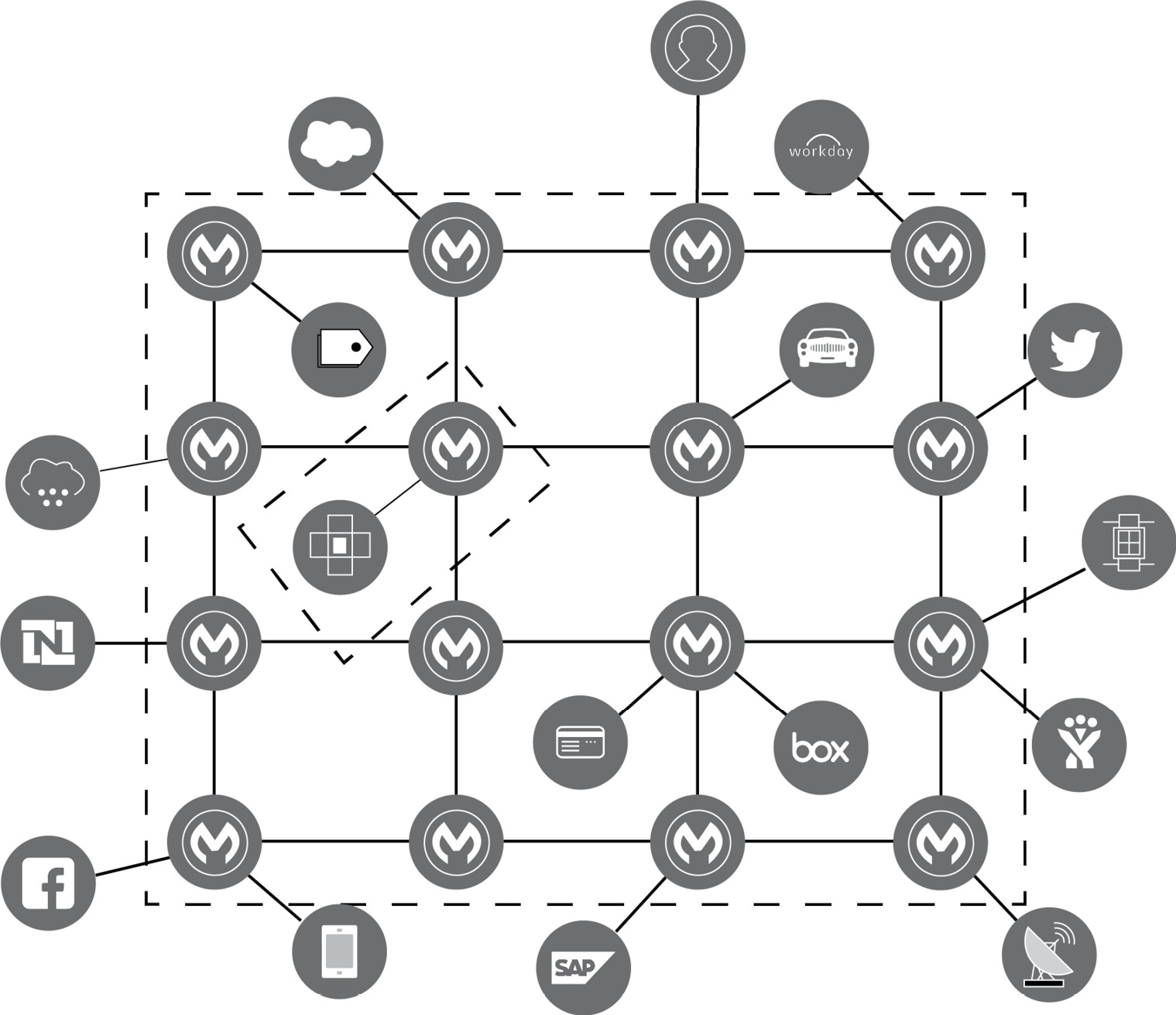
Figure 10.1 – A snapshot of Anypoint Platform depicting application networks
In order to achieve total security, you can apply security regulations on any of the following:
You can implement the preceding security mechanism in any permutation and combination as...
