When we explored the GUI in Chapter 1, The Splunk Interface, you probably noticed fields everywhere. Fields appear in the field picker on the left and under every event. Where fields actually come from is transparent to the user, who simply searches for key=value. We will discuss adding new fields in
Chapter 3, Tables, Charts, and Fields, and in Chapter 11, Configuring Splunk.
The field picker gives us easy access to the fields (currently defined) for the results of our query. Splunk will extract some fields from event data without your help, such as host, source, and sourcetype values, timestamps, and others. Additional fields to be extracted can be defined by you. Clicking on any field presents us with the details about that field in our current search results:
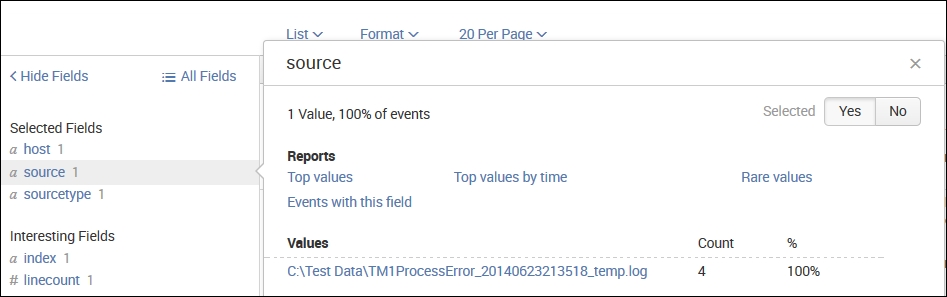
As we go through the following items in this widget, we see a wealth of information right away:
N Value, X% of events is a good indication of whether we are getting the results we think...



