Citrix NetScaler supports authentication for load balancing and access gateway purposes. The load balancing authentication is called the authentication, authorization, and auditing (AAA) functionality in Citrix NetScaler. By enabling the AAA feature on the load balancing virtual server, you can provide an extra security layer. The load balancing feature is a good solution for reverse proxy deployments. Enabling AAA on load balancing provides the extra security that you prefer to use for some services. While implementing AAA, it's also possible to add extra security (for example, two-factor authentication) to services that support only active directory authentication. So, Outlook Web Access for Microsoft Exchange can be configured with Active Directory and two-factor authentication. The NetScaler AAA features will redirect a load balancing virtual server to the NetScaler AAA virtual server. After authentication, the client will be sent back to the load balancing virtual server and will show the configured backend environment. So, the client connects to the load balancing virtual server for the Microsoft Exchange; NetScaler will redirect the client to the NetScaler AAA virtual servers. The client needs to log in. After successful authentication, NetScaler sends the client back to the load balancing virtual server.
Citrix NetScaler supports a lot of different methods of authentication. These methods can be used for NetScaler Gateway authentication or for load balancing virtual servers. The most common authentication methods will be described in the following sections.
Tip
Authentication, Authorization, and Auditing (AAA) is available in the Enterprise and Platinum NetScaler license.
LDAP integration is a commonly used method of authentication in deployments. Almost all companies are using LDAP authentication in some way. In order to use LDAP authentication, there are some prerequisites, as follows:
A user account for "reading" the LDAP attributes
The IP addresses from the LDAP servers
How the user needs to log in (by username or e-mail address)
Whether all users need access through LDAP authentication or any particular LDAP group
Whether the LDAP server is responding with SSL or in PLAINTEXT
After you have the answers to these question, you can start building the configuration.
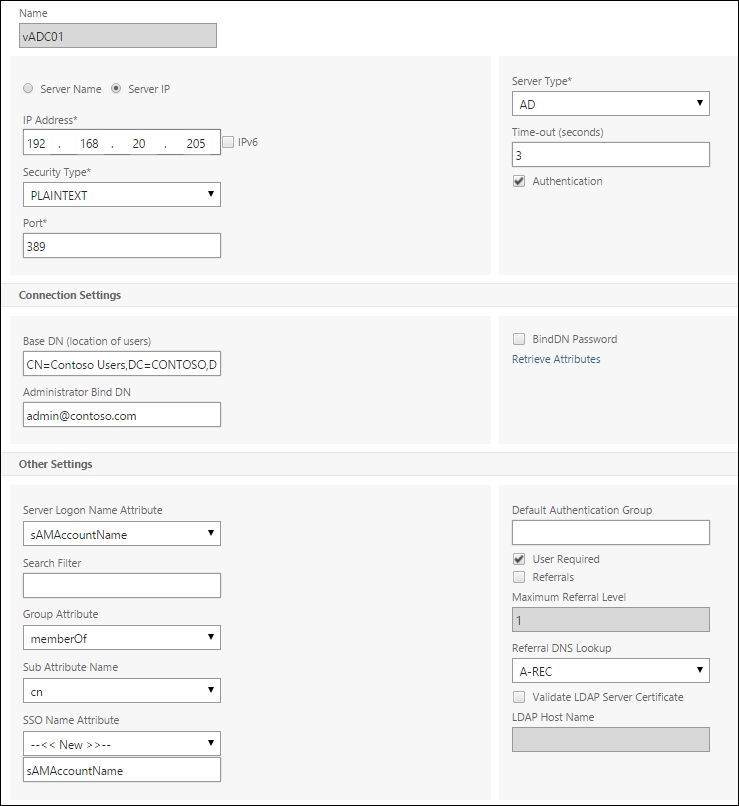
Go to System | Authentication | LDAP | Servers, and click on Add. Fill in the correct information based on the following explanation:
Name: Select a decent name that responds to the LDAP server, for example,
Pol_Srv-LDAP-LDAPS1.Select Server Name or Server IP. Server Name needs the FQDN, and Server IP needs the IP address from the LDAP server.
Security Type: Select the available security type. It is preferable to use SSL because the credentials will not be sent in PLAINTEXT.
Server Type: Select
ADfor Microsoft Active Directory orNDSif you're using Novell.Base DN: This box needs be filled in where Citrix NetScaler should look for users. If all the users are located in a particular organizational unit in Active Directory, it could be the Base DN. The less attributes needs be searched for the faster Citrix NetScaler will respond to the authentication questions. For example, a base DN for an organizational unit called Contoso Users in the
contoso.comdomain would look likeCN=Contoso Users,DC=CONTOSO,DC=COM.Administrator Bind DN: This is the username for the AD or NDS that can be used for query the domain. This user doesn't require any specific security; domain users are okay. The username can be written in the
domain\usernameor the[email protected]method.BindDN Password: This will be the password from the configured administrator account, corresponding to the username that has filled in the Administrator Bind DN field.
Server Logon Name Attribute: Commonly, this value contains the
sAMAccountNameorUserPrincipalNameActive Directory / NDS attribute. Using theUserPrincipalNamevalue allows you to log in with the e-mail address. Otherwise, the username is required to log in.Search Filter: This should be used if you'd like to allow access only for a particular Active Directory or NDS group. For example, you want to allow only the
AAA_Allowgroup in the supportOUto get the functionality to authenticate. The search filter would bememberOf=CN=AAA_Allow,OU=support,DC=contoso,DC=com. When a user is a member of this group, they will have access; otherwise, Citrix NetScaler will block the authentication. The source of this is http://support.citrix.com/article/CTX111079.Group Attribute: This will be used for group extraction. It's also possible to bind NetScaler Gateway policies to user groups. This will be explained later in the book. The default group attribute in the Active Directory /NDS is
memberOf.Sub Attribute Name: This value is used to identify the subattribute name for group extraction.
SSO Name Attribute: This attribute is used when Single Sign On (SSO) is configured. Depending on the backend, it should be
sAMAccountNameorUserPrincipalName.
Tip
Use SSL as Security Type if possible. Besides, for security reasons, it always allows users to change their password remotely.
After creating the LDAP servers, it's time to configure the LDAP Policies. These policies are necessary in order to bind it to a service. Depending on the configuration, there are many ways to configure it. With expressions, it is possible to, for example, allow access for specific client for a particular service. This will be done based on the source IP of the client and the destination IP for the particular service that you'd like to allow access to. The policy would be REQ.IP.SOURCEIP == 122.122.123.123 && REQ.IP.DESTIP == 192.168.100.14. In this example, the client with IP address 122.122.123.123 will be able to log in with the service 192.168.100.14.
It's also possible to add more than one LDAP authentication policy and bind them to the AAA or NetScaler Gateway authentication. This can be done by assigning priorities to the different policies. The LDAP policy with the lowest priority will be checked first to see whether the expression is matching. Otherwise, Citrix NetScaler will keep going down the list until it finds a match. If the policy matches but the server isn't responding within the configured timeout, Citrix NetScaler will automatically fill try the other expression.
Citrix NetScaler allows you to support two-factor authentication in many ways. The most commonly used way of two-factor authentication is by using the RADIUS protocol.
Most two-factor authentication providers support the RADIUS protocol because it's a standard protocol.
The RADIUS protocol uses a few codes to indicate the authentication step, as follows:
|
Code |
Assignment |
|---|---|
|
|
Access-Request |
|
|
Access-Accept |
|
|
Access-Reject |
|
|
Accounting-Request |
|
|
Accounting-Response |
|
|
Access-Challenge |
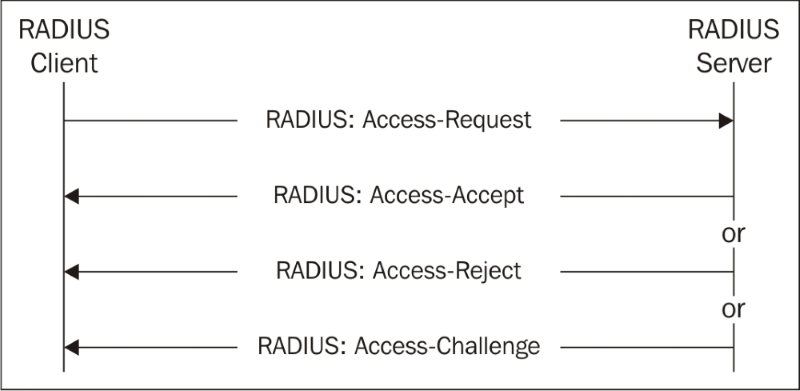
Depending on what the RADIUS server sends back, Citrix NetScaler will allow or deny the access to log in.
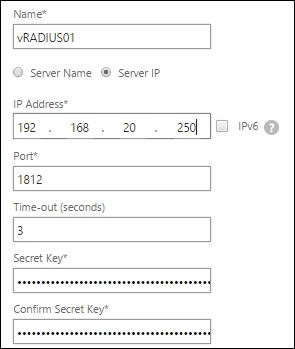
Go to System | Authentication | RADIUS | Servers, and click on Add. Fill in the correct information based on the following explanation:
Name: Select a decent name that responds to the RADIUS server, for example,
Pol_Srv-RADIUS-RADIUSS1.Select Server Name or Server IP. Server Name needs the FQDN, and Server IP needs the IP address from the RADIUS server.
Port: This is the RADIUS port.
Time-out (seconds): This is the time that the RADIUS server has to respond to Citrix NetScaler.
Secret Key: On the RADIUS server, a RADIUS client should also be created. This RADIUS client configuration requires a shared key. This key will be created during the configuration at the RADIUS server. The secret key needs to be filled in this box.
NAS ID: By default, Citrix NetScaler will send the hostname from the device. With the NAS ID, Citrix NetScaler will send the identifier configured in this box.
Group Vendor Identifier: This is the RADIUS vendor ID attribute. It is used for RADIUS group extraction.
Group Prefix: This is the RADIUS group's prefix string. This group prefix precedes the group names within a RADIUS attribute for RADIUS group extraction.
Group Attribute Type: This is the attribute number that contains the group information.
Group Separator: This is the group separator string that delimits group names within a RADIUS attribute for RADIUS group extraction.
IP Address Vendor Identifier: This is the vendor ID of the Intranet IP attribute in the RADIUS response. The default value of
0indicates that the attribute is not vendor encoded.IP Address Attribute Type: This is the remote IP address attribute type in a RADIUS response.
Password Vendor Identifier: This is the vendor ID of the attribute in the RADIUS response. It is used to extract the user's password.
Password Attribute Type: This is the vendor-specific password attribute type in a RADIUS response.
Password Encoding: This is the encoding type for passwords in the RADIUS packets that the NetScaler appliance sends to the RADIUS server. Citrix NetScaler supports PAP, CHAP, MS-CHAPv1, and MS-CHAPv2. MS-CHAPv2 is the most secure method.
Accounting: This allows Citrix NetScaler to support accounting. It can be ON or OFF.
Default Authentication Group: This is the default group that is chosen when the authentication succeeds in addition to extracted groups.
Tip
When using RADIUS authentication, it's necessary to create a RADIUS client on the RADIUS server. This RADIUS client will be Citrix NetScaler. The RADIUS client's IP address would be the NetScaler IP (NSIP).
After creating the RADIUS servers, it's time to configure the RADIUS Policies. These policies are necessary for binding it to services.
It's also possible to add more than one RADIUS authentication policy and bind them to the AAA or NetScaler Gateway authentication. This can be done by assigning priorities to the different policies. The way of configuring is the same as that for binding the LDAP authentication policy.
Tip
Citrix wrote an article on how to configure Citrix NetScaler with Microsoft NPS. Microsoft NPS is the RADIUS server from Microsoft. A lot of third-party vendors have written plugins for NPS server. An article that can be used is http://support.citrix.com/article/CTX126691.



