If you want to use the Citrix Receiver functionality and Receiver for Web with the NetScaler Gateway environment as well, some changes should be made to the LDAP and RADIUS policies. You should make some adjustments to the expressions.
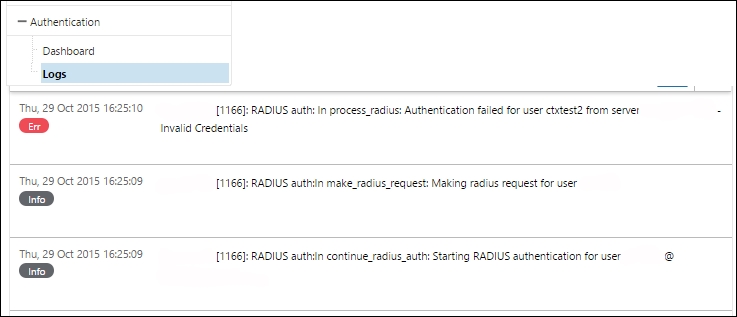
When a user contacts the NetScaler Gateway through the web browser, they will see three fields that need to be filled in.
The first box requires the username, the second requires the password, and the third requires the RADIUS code. This means that the LDAP authentication is primary and RADIUS is the secondary authentication. You can see this in the following screenshot:
When the user connects with Citrix Receiver, the authentication is different because Citrix Receiver verifies the RADIUS authentication as primary and the LDAP authentication as secondary.
In order to arrange this, we should create two different LDAP and RADIUS policies. The LDAP policies could bind to the same LDAP server. The RADIUS policies could be bind to the same RADIUS server as well.
Follow these steps to arrange authentication through Citrix Receiver when using two-factor authentication:
Create two LDAP policies:
Policy 1:
Name:
CitrixReceiver-DC1(whereDC1is the domain controller name)Expression:
REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiverServer:
DC1Policy 2:
Name:
NonCitrixReceiver-DC1(whereDC1is the domain controller name)Expression:
REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiverServer:
DC1
Create two RADIUS policies:
Policy 1:
Name:
CitrixReceiver-RADIUS1(whereRADIUS1is the RADIUS server)Expression:
REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiverServer:
RADIUS1Policy 2:
Name:
NonCitrixReceiver-RADIUS1(whereRADIUS1is the RADIUS server)Expression:
REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiverServer:
RADIUS1
Bind the
NonCitrixReceiver-DC1LDAP policy and theCitrixReceiver-RADIUS1RADIUS policy as the primary authentication.Bind the
CitrixReceiver-DC1LDAP policy and theNonCitrixReceiver-RADIUS1RADIUS policy as the secondary authentication.
When the user connects through Citrix Receiver, the authentication flow would first be CitrixReceiver-RADIUS1 as primary and CitrixReceiver-DC1 as secondary, because Citrix Receiver contains the User-Agent header with the CitrixReceiver value. All other non-Citrix Receiver users will authenticate with NonCitrixReceiver-DC1 as primary authentication and NonCitrixReceiver-RADIUS1 as secondary authentication.
For troubleshooting authentication, Citrix NetScaler provides a built-in tool that can be run from the CLI. Connect to the CLI with an SSH tool (PuTTY, for example). After logging in, type shell and then jump to the tmp location using cd /tmp. Run the following command after switching to the tmp location:
cat aaaa.debug
This built-in tool will give us information about what's going wrong during authentication.
Besides the built-in tool, Citrix also provides troubleshoot logging according to authentication in the GUI since NetScaler firmware release 11. So, if you are using Citrix NetScaler 11, troubleshooting through CLI isn't necessary.