In this section, we'll take a look at how to run dumpcap, which is another alternative to tshark and tcpdump.
Once again, we'll have to go todumpcap. In this example, it is installed with Wireshark on the system, and if we do a directory listing, you'll see that dumpcap is indeed listed. Tshark is actually based on dumpcap, and so we can type dumpcap.exe --help or -h. If we take a look at the output, it looks very similar to tshark and Wireshark:
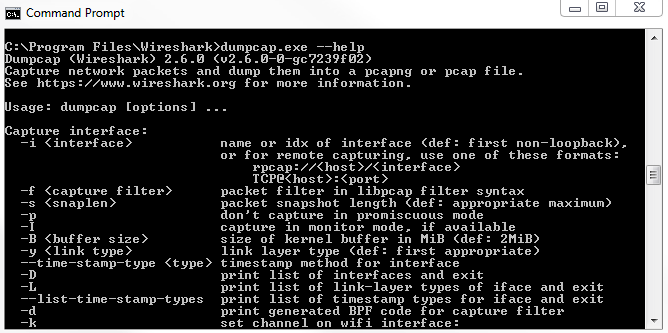
Depending on the system that you're using though, it may only have dumpcap available for one reason or another, or tshark may be using too much memory if it's a really small, embedded IoT system, or something like that. You could potentially use dumpcap to have an even lighter utility in order to capture traffic-or maybe you just like using this better. If we look at the arguments that are available, they are just like in tshark. We have -i, -D, and -w for output. They're all very much the same. We can illustrate that by running dumpcap...



