In this section, we'll take a look at how to change the time settings for packets and troubleshooting with the time column.
We have the PBS packet capture again, where I opened the browser and went to http://www.pbs.org/. If you notice in the packet capture, the second column says Time:
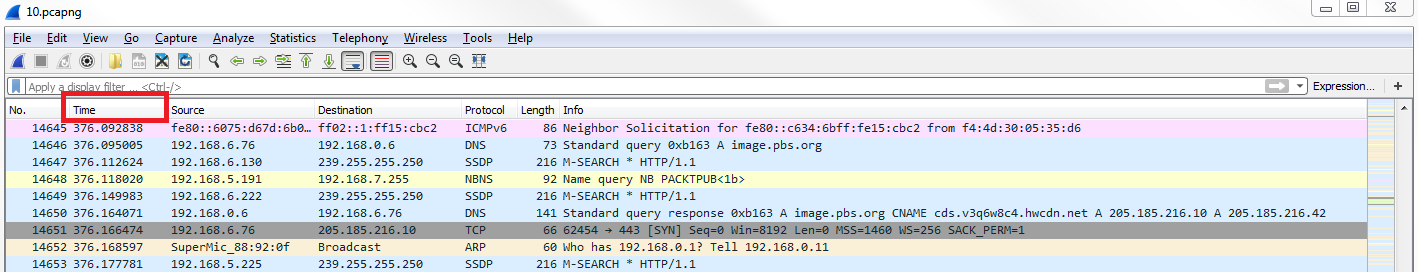
The Time column is a number with a decimal and it just keeps counting up as you scroll down through the packet capture. By default, in Wireshark, this is the time since the capture started. Having the time since it was captured can be useful so you know when certain packets arrive in relation to the entire data flow that you captured, but it's not all that useful for trying to diagnose a problem where there might be a delay in a certain service returning traffic that you're trying to capture back to your system.
In order to figure out the delay between captured packets, you'd have to look at the Time column and figure it out based on milliseconds, microseconds, and nanoseconds, and...



