This recipe will cover the planning steps that you should consider before you start preparing to deploy your DPM servers.
Before you start planning your DPM server deployment, it's imperative that you start working on classifying the data sources that you would like to protect. A common strategy that I have observed that many companies still follow is to backup everything once a day. This is not a good approach.
There are, of course, several servers within your datacenter that need to be regularly backed up, but not all servers are the same. It is vital to adapt to your business continuity and disaster-recovery plan before you start any implementation. You can do this by identifying all of the services and working with all of the stakeholders in your company to develop more effective backup approaches, and then break down those services into smaller components to clearly see how or why they are of importance to your business.
From a more technical perspective, there are some considerations that need to be addressed during the planning phase, such as the following:
- The total amount of data that should be protected
- Firewall settings
- Network consideration
- Who can interact with DPM
- Untrusted domains/workgroup
- Backup repository
To start provisioning resources for the DPM server that you want to deploy, you must first take into consideration the following:
- Starting with DPM 2016 onward, Microsoft removed the Logical Disk Manager (LDM) limits for protection groups. The absence of LDM limits allows the data sources to grow and shrink as many times as needed, without the need for manual intervention. DPM 2016 or later does not need to allocate storage to data sources beforehand compared to DPM 2012 R2. This will allow the backups to adjust dynamically as needed, thus achieving higher efficiency with less storage requirements. The snapshot limits do not apply to protection groups that have been created in DPM 2016, as DPM does not use disks anymore. Instead, it uses volumes. Please read Chapter 2, DPM Post-Installation and Management Tasks, for more information on this.
- Here are the suggested data limits according to Microsoft for a single DPM server:
- DPM can protect up to 600 volumes. The limit for each DPM is 120 TB, 80 TB ReplicaPoint Volume, and 40 TB RecoveryPoint.
- The total amount of SQL DBs that can be protected by one DPM server is 2,000 and the total size is 80 TB.
- The total amount of clients that can be protected with one DPM server is 3,000 and the total size is 80 TB.
- The total amount of virtual machines that can be protected with one DPM server is 800 and the total size is 80 TB.
- Firewall configuration for DPM deployment is required on the DPM server, on the machines that you want to protect, and on the SQL Server used for the DPM database (if you're hosting your DPM database on a remote SQL Server). If Windows Firewall is enabled when you install DPM, then DPM automatically configures the firewall settings on the DPM server.
Note
The firewall settings, including the port numbers, are documented in the following link: https://docs.microsoft.com/en-us/system-center/dpm/plan-dpm-deployment?view=sc-dpm-1711#BKMK_Firewall.
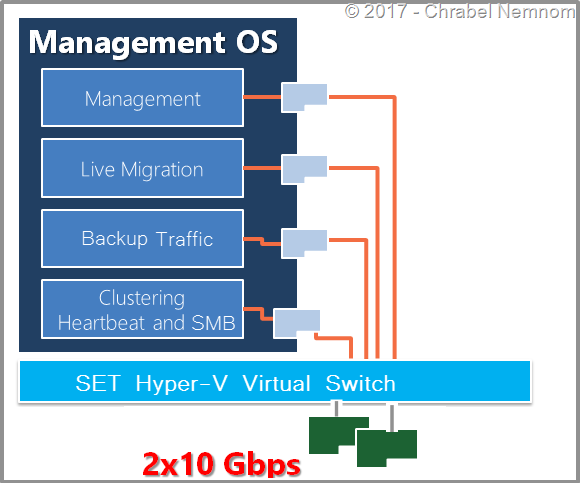
- The backup network for Hyper-V is not listed as a requirement by Microsoft. However, we strongly recommend isolating the backup traffic from the host Management OS by leveraging a converged network in Hyper-V where you combine multiple physical NICs with Switch-Embedded Teaming (SET) and Quality of Service (QoS) so that you can isolate all network traffic while maintaining resiliency. This implementation can be seen in following diagram:
Note
The required permissions needed are documented at the following link: https://docs.microsoft.com/en-us/system-center/dpm/plan-dpm-deployment?view=sc-dpm-1711#BKMK_Users.
- If you want to protect multiple domains, you can create a two-way transitive trust between the domains. By doing this, the DPM server will work in both domains without any limitations. However, this approach comes with a security risk—please take into consideration that you need to create a two-way transitive trust between the untrusted domains.
- Starting with System Center 2012 R2 Data Protection Manager, Microsoft added support for the protection of computers in workgroups and untrusted domains using NTLM with local accounts. However, in scenarios where an organization does not allow for the creation of local accounts, this solution does not work.
- As an alternative, you can use certificate-based authentication for computers in workgroups or untrusted domains. Please refer to Chapter 8, Protecting Workgroups and Untrusted Domains, for more information.
- A major part of your DPM deployment will be figuring out how to store data that's been backed up by DPM. There are currently three different solutions:
You should not just consider one of these three as an option. Instead, you need to focus on the requirements of the backup strategy in your organization by discussing the Recovery Point Objective (RPO) and Recovery Time Objective (RTO) with all stakeholders.
When you are planning for data source protection, you can choose the backup target based on how frequently you need to access and restore the data. For example, if the data sources will be used for archiving and need to be accessed once per month, you can go with Azure Backup. If the protected data sources need an archiving solution but should also be able to restore quickly, you can go with Virtual Tape Library (VTL) or Azure Backup. If you need to restore the data sources as quickly as possible, you go with disk storage on-premises. Finally, if the workloads need an off-site secure solution, you can go with Azure Backup.
Note
More information about the difference between RPO and RTO can be found here: https://en.wikipedia.org/wiki/Recovery_point_objective.
Having all of the information we have just discussed and presented in an organized manner, you can now start designing the structure of the Backup as a Service (BaaS). A piece of advice here—make sure that you spend enough time on the planning phase and take small steps toward your goal and never rush an implementation. You will probably bump into a challenge or two, so it is of key importance to work using a well-defined structure.
- Follow this blog post to learn more about how to set the firewall rules for DPM using Windows PowerShell: https://charbelnemnom.com/2017/03/installing-system-center-data-protection-manager-2016-agent-on-windows-server-2016-core-scdpm-dpm-ws2016/.
- Follow the following blog post to learn more on how to isolate DPM backup traffic: https://charbelnemnom.com/2014/04/isolate-dpm-backup-traffic-in-hyper-v/.



