Rules created for a VM only apply to that particular virtual machine. Even when the virtual machine is moved to a different node, the firewall follows the VM throughout the cluster. There are no rules cascading from this zone. Under the VM firewall feature, we can create Rules, Aliases, and IPSets, but we cannot create any security group. The firewall management is the same for both the KVM virtual machines and LXC containers. We can go to the firewall feature of a VM by navigating to the VM | Firewall tab menu. The following screenshot shows the firewall feature of our example VM #112:
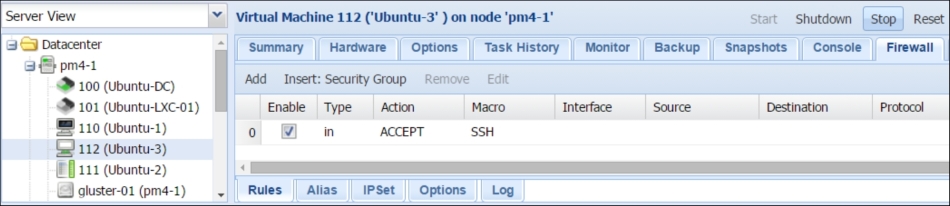
The process of creating new rules for a VM is identical to the rule creation process that we have already seen in the Configuring the Datacenter firewall through the CLI section earlier in this chapter. Besides creating rules from scratch, we can also assign predefined rules in the form of a Security Group to a VM. The preceding screenshot shows...



