Understanding the security transformation
Over the years, security has evolved from being a shared role or a role that was non-existent within a business. Today, well-defined teams and organizational structures exist or are being created to focus solely on security. Not only are these teams maturing constantly, but the Chief Information Security Officer (CISO) has become a person of significant importance and may report directly to a Chief Executive Officer (CEO) and not the Chief Information Officer (CIO).
Over the years, many roles that never existed before have begun to appear within the security world, and new skill sets are always in demand. As an overview, here are some of the more common security roles that you can expect to see within a security program: CISO/CSO, Information Technology (IT) Security Director, IT Security Manager, Security Architect/Engineer, Security Analyst, Security/Compliance Officer, Security Administrator, Security Engineer, Software/Application Security Developer, Software/Application Security Engineer, Cryptographer/Cryptologist, Security Consultant/Specialist, Network Security Engineer, and Cloud Security Architect.
As an example, the following screenshot shows what a security organization may look like through an organization chart. Every organization is different, but this will provide you with a basis of what can be expected:
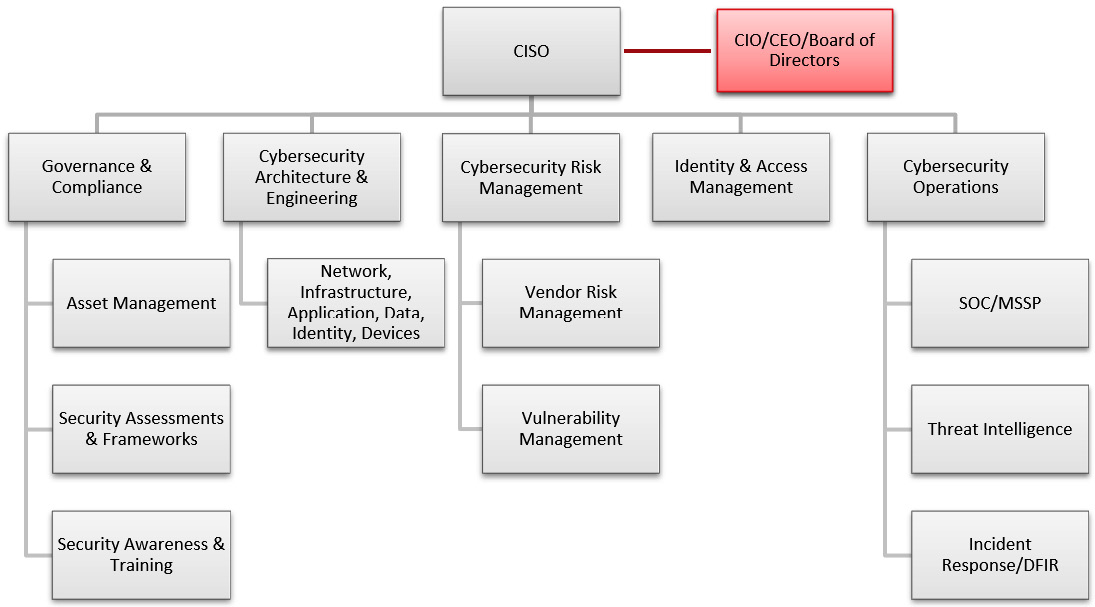
Figure 1.1 – Sample organization structure
One thing to point out regarding these roles is the shortage of a cybersecurity workforce throughout the world. Although an ongoing concern, the great news is that since the original version of this publication, there has been a significant increase in cybersecurity professionals worldwide, according to the cybersecurity workforce study by the International Information System Security Certification Consortium ((ISC)²). The updated (ISC)² 2021 Cybersecurity Workforce Study shows that a worldwide growth of 65% is still needed to meet the demand for cyber experts, which is significantly down from 2019 when 145% growth was needed. The study estimates that there are approximately 4.19 million cybersecurity professionals globally. This is an increase of more than 700,000 from 2020. The ongoing challenge continues to be with the growth of new positions that are continuously being created as cybersecurity programs continue to enhance. This makes it difficult to find well-seasoned talent and may require you to think outside the box as you look to onboard those new to the field or looking to shift careers. You can read more about the (ISC)² 2021 Cybersecurity Workforce Study here: https://www.isc2.org/Research/Workforce-Study.
One of the primary factors for a growing need for security experts correlates to the advancement of the personal computer (or PC) and its evolution throughout the years. The PC has changed the way we connect, and with this evolution comes the supporting infrastructure, which has evolved into the many data centers seen throughout the world.
As we are all aware, Windows has been the victim of numerous vulnerabilities over the years and continues to be a victim even today. The initial idea behind the Windows Operating System (OS) was a strong focus on usability and productivity. As a result of its success and adoption across the globe, it became a common target for exploits. This, in turn, created many gaps in the security of Windows that have traditionally been filled by many other companies. A good example was the need for third-party AV software. As the world has turned more toward digitization over the years and Windows usage has continued to grow, so has the need for improved security, along with dedicated roles within this area. Protecting Windows has not been an easy task, and it continues to be an ongoing challenge.



